Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Mar 30, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 111:
An loT device implements an encryption module built within its SoC where the asymmetric private key has been defined in a write-once read-many portion of the SoC hardware Which of the following should the loT manufacture do if the private key is compromised?
A. Use over-the-air updates to replace the private key
B. Manufacture a new loT device with a redesigned SoC
C. Replace the public portion of the loT key on its servers
D. Release a patch for the SoC software
-
Question 112:
A hospital has fallen behind with patching known vulnerabilities due to concerns that patches may cause disruptions in the availability of data and impact patient care. The hospital does not have a tracking solution in place to audit whether systems have been updated or to track the length of time between notification of the weakness and patch completion Since tracking is not in place the hospital lacks accountability with regard to who is responsible for these activities and the timeline of patching efforts. Which of the following should the hospital do first to mitigate this risk?
A. Complete a vulnerability analysis
B. Obtain guidance from the health ISAC
C. Purchase a ticketing system for auditing efforts
D. Ensure CVEs are current
E. Train administrators on why patching is important
-
Question 113:
A security engineer investigates an incident and determines that a rogue device is on the network. Further investigation finds that an employee's personal device has been set up to access company resources and does not comply with standard security controls. Which of the following should the security engineer recommend to reduce the risk of future reoccurrence?
A. Require device certificates to access company resources.
B. Enable MFA at the organization's SSO portal.
C. Encrypt all workstation hard drives.
D. Hide the company wireless SSID.
-
Question 114:
The general counsel at an organization has received written notice of upcoming litigation. The general counsel has issued a legal records hold. Which of the following actions should the organization take to comply with the request?
A. Preserve all communication matching the requested search terms
B. Block communication with the customer while litigation is ongoing
C. Require employees to be trained on legal record holds
D. Request that all users do not delete any files
-
Question 115:
After a server was compromised an incident responder looks at log files to determine the attack vector that was used The incident responder reviews the web server log files from the time before an unexpected SSH session began:

Which of the following is the most likely vulnerability that was exploited based on the log files?
A. Directory traversal revealed the hashed SSH password, which was used to access the server.
B. A SQL injection was used during the ordering process to compromise the database server
C. The root password was easily guessed and used as a parameter lo open a reverse shell
D. An outdated third-party PHP plug-in was vulnerable to a known remote code execution
-
Question 116:
A security engineer needs to select the architecture for a cloud database that will protect an organization's sensitive data. The engineer has a choice between a single-tenant or a multitenant database architecture offered by a cloud vendor. Which of the following best describes the security benefits of the single-tenant option? (Select two).
A. Most cost-effective
B. Ease of backup and restoration
C. High degree of privacy
D. Low resilience to side-channel attacks
E. Full control and ability to customize
F. Increased geographic diversity
-
Question 117:
A SOC analyst received an alert about a potential compromise and is reviewing the following SIEM logs:
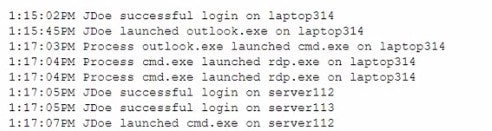
Which of the following is the most appropriate action for the SOC analyst to recommend?
A. Disabling account JDoe to prevent further lateral movement
B. Isolating laptop314 from the network
C. Alerting JDoe about the potential account compromise
D. Creating HIPS and NIPS rules to prevent logins
-
Question 118:
An organization established an agreement with a partner company for specialized help desk services. A senior security officer within the organization Is tasked with providing documentation required to set up a dedicated VPN between the two entities. Which of the following should be required?
A. SLA
B. ISA
C. NDA
D. MOU
-
Question 119:
Which of the following is a risk associated with SDN?
A. Expanded attack surface
B. Increased hardware management costs
C. Reduced visibility of scaling capabilities
D. New firmware vulnerabilities
-
Question 120:
A large organization is planning to migrate from on premises to the cloud. The Chief Information Security Officer (CISO) is concerned about security responsibilities. If the company decides to migrate to the cloud, which of the following describes who is responsible for the security of the new physical datacenter?
A. Third-party assessor
B. CSP
C. Organization
D. Shared responsibility
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.