Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 171:
An organization is running its e-commerce site in the cloud. The capacity is sufficient to meet the organization's needs throughout most of the year, except during the holidays when the organization plans to introduce a new line of products and expects an increase in traffic The organization is not sure how well its products will be received. To address this issue, the organization needs to ensure that:
1.
System capacity is optimized.
2.
Cost is reduced
Which of the following should be implemented to address these requirements? (Choose two.)
A. Containerization
B. Load balancer
C. Microsegmentation
D. Autoscaling
E. WAF
F. CDN
-
Question 172:
A bank hired a security architect to improve its security measures against the latest threats. The solution must meet the following requirements:
1.
Recognize and block fake websites.
2.
Decrypt and scan encrypted traffic on standard and non-standard ports.
3.
Use multiple engines for detection and prevention.
4.
Have central reporting.
Which of the following is the BEST solution the security architect can propose?
A. CASB
B. Web filtering
C. NGFW
D. EDR
-
Question 173:
A security manager has written an incident response play book for insider attacks and is ready to begin testing it. Which of the following should the manager conduct to test the playbook?
A. Automated vulnerability scanning
B. Centralized logging, data analytics, and visualization
C. Threat hunting
D. Threat emulation
-
Question 174:
A company wants to improve the security of its web applications that are running on in-house servers. A risk assessment has been performed, and the following capabilities are desired:
1.
Terminate SSL connections at a central location
2.
Manage both authentication and authorization for incoming and outgoing web service calls
3.
Advertise the web service API
4.
Implement DLP and anti-malware features
Which of the following technologies will be the BEST option?
A. WAF
B. XML gateway
C. ESB gateway
D. API gateway
-
Question 175:
A SaaS startup is maturing its DevSecOps program and wants to identify weaknesses earlier in the development process in order to reduce the average time to identify serverless application vulnerabilities and the costs associated with remediation. The startup began its early security testing efforts with DAST to cover public-facing application components and recently implemented a bug bounty program. Which of the following will BEST accomplish the company's objectives?
A. RASP
B. SAST
C. WAF
D. CMS
-
Question 176:
A company recently implemented a CI/CD pipeline and is now concerned with the current state of its software development processes. The company wants to augment its CI/CD pipeline with a solution to:
1.
Prevent code configuration drifts.
2.
Ensure coding standards are followed.
Which of the following should the company implement to address these concerns? (Choose two.)
A. Code signing
B. Fuzzers
C. Dynamic code analysis
D. Manual approval processes
E. Linters
F. Regression testing
-
Question 177:
A company is experiencing a large number of attempted network-based attacks against its online store. To determine the best course of action, a security analyst reviews the following logs.

Which of the following should the company do NEXT to mitigate the risk of a compromise from these attacks?
A. Restrict HTTP methods.
B. Perform parameterized queries.
C. Implement input sanitization.
D. Validate content types.
-
Question 178:
A company recently migrated all its workloads to the cloud and implemented a transit VPC with a managed firewall. The cloud infrastructure implements a 10.0.0.0/16 network, and the firewall implements the following ACLs:
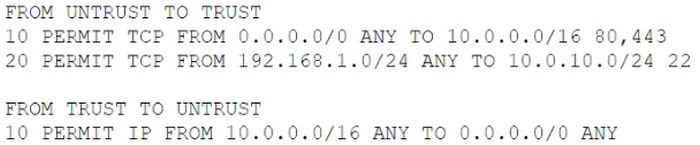
The Chief Information Security Officer wants to monitor relevant traffic for signs of data exfiltration. Which of the following should the organization place in its monitoring tool to BEST detect data exfiltration while reducing log size and the time to search logs?
A. FROM UDP 10.0.0.0/16 ANY TO 0.0.0.0/0 ANY
B. FROM TCP 10.0.0.0/16 80,443 TO 0.0.0.0/0 ANY
C. FROM TCP 0.0.0.0/0 ANY TO 10.0.0.0/16 80,443,22
D. FROM IP 10.0.0.0/16 ANY TO 0.0.0.0/0 ANY
E. FROM IP 0.0.0.0/0 ANY TO TCP 0.0.0.0/0 ANY
F. FROM UDP 0.0.0.0/0 ANY TO 0.0.0.0/0 ANY
-
Question 179:
A company recently deployed a SIEM and began importing logs from a firewall, a file server, a domain controller, a web server, and a laptop. A security analyst receives a series of SIEM alerts and prepares to respond. The following is the alert information:
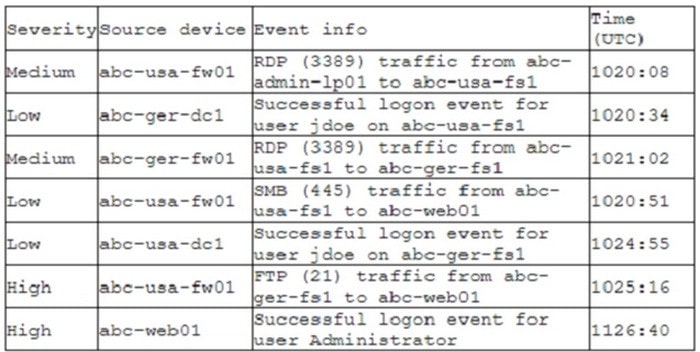
Which of the following should the security analyst do FIRST?
A. Disable Administrator on abc-usa-fs1; the local account is compromised.
B. Shut down the abc-usa-fs1 server; a plaintext credential is being used.
C. Disable the jdoe account; it is likely compromised.
D. Shut down abc-usa-fw01; the remote access VPN vulnerability is exploited.
-
Question 180:
A security analyst is reviewing the data portion acquired from the following command:
tcpdump -lnvi icmp and src net 192.168.1.0/24 and dst net 0.0.0.0/0 -w output.pcap
The data portion of the packet capture shows the following:
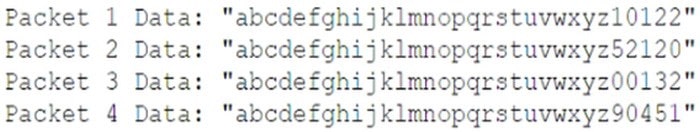
The analyst suspects that a data exfiltration attack is occurring using a pattern in which the last five digits are encoding sensitive information. Which of the following technologies and associated rules should the analyst implement to stop this specific attack? (Choose two.)
A. Intrusion prevention system
B. Data loss prevention
C. sed -e 's/a-z.*0-9.*//g'
D. reject icmp any any <> any any (msg:"alert"; regex [a-z]{26}[0-9]{5})
E. Second-generation firewall
F. drop icmp from 192.168.1.0/24 to 0.0.0.0/0
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.