Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 181:
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices: Which of the following mobile configuration settings is the mobile administrator verifying?
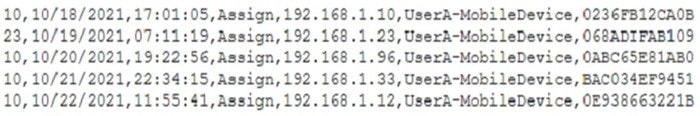
A. Service set identifier authentication
B. Wireless network auto joining
C. 802.1X with mutual authentication
D. Association MAC address randomization
-
Question 182:
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port. The service cannot be turned off, as it would impact a critical application's ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
A. service --status-all | grep ftpd
B. chkconfig --list
C. netstat --tulpn
D. systemctl list-unit-file --type service ftpd
E. service ftpd status
-
Question 183:
A new requirement for legislators has forced a government security team to develop a validation process to verify the integrity of a downloaded file and the sender of the file. Which of the following is the BEST way for the security team to comply with this requirement?
A. Digital signature
B. Message hash
C. Message digest
D. Message authentication code
-
Question 184:
A cyberanalyst has been tasked with recovering PDF files from a provided image file. Which of the following is the BEST file-carving tool for PDF recovery?
A. objdump
B. Strings
C. dd
D. Foremost
-
Question 185:
An organization has an operational requirement with a specific equipment vendor. The organization is located in the United States, but the vendor is located in another region. Which of the following risks would be MOST concerning to the organization in the event of equipment failure?
A. Support may not be available during all business hours.
B. The organization requires authorized vendor specialists.
C. Each region has different regulatory frameworks to follow.
D. Shipping delays could cost the organization money.
-
Question 186:
A company underwent an audit in which the following issues were enumerated:
1.
Insufficient security controls for internet-facing services, such as VPN and extranet
2.
Weak password policies governing external access for third-party vendors
Which of the following strategies would help mitigate the risks of unauthorized access?
A. 2FA
B. RADIUS
C. Federation
D. OTP
-
Question 187:
A MSSP has taken on a large client that has government compliance requirements. Due to the sensitive nature of communications to its aerospace partners, the MSSP must ensure that all communications to and from the client web portal are secured by industry-standard asymmetric encryption methods. Which of the following should the MSSP configure to BEST meet this objective?
A. ChaCha20
B. RSA
C. AES256
D. RIPEMD
-
Question 188:
An internal security assessor identified large gaps in a company's IT asset inventory system during a monthly asset review. The assessor is aware of an external audit that is underway. In an effort to avoid external findings, the assessor chooses not to report the gaps in the inventory system. Which of the following legal considerations is the assessor directly violating?
A. Due care
B. Due diligence
C. Due process
D. Due notice
-
Question 189:
Signed applications reduce risks by:
A. encrypting the application's data on the device
B. requiring the developer to use code-level hardening techniques.
C. providing assurance that the application is using unmodified source code.
D. costing the developer money to publish, which reduces the likelihood of malicious intent.
-
Question 190:
After installing an unapproved application on a personal device, a Chief Executive Officer reported an incident to a security analyst. This device is not controlled by the MDM solution, as stated in the BVOD policy. However, the device contained critical confidential information. The cyber incident response team performed the analysis on the device and found the following log:
Wed 12 Dec 2020 10:00:03 Unknown sources is now enabled on this device.
Which of the following is the MOST likely reason for the successful attack?
A. Lack of MDM controls
B. Auto-join hotspots enabled
C. Sideloading
D. Lack of application segmentation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.