Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 341:
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts most of the responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
A. IaaS
B. SaaS
C. FaaS
D. PaaS
-
Question 342:
A new, online file hosting service is being offered. The service has the following security requirements:
1.
Threats to customer data integrity and availability should be remediated first.
2.
The environment should be dynamic to match increasing customer demands.
3.
The solution should not interfere with customers' ability to access their data at anytime.
4.
Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
A. Expanding the use of IPS and NGFW devices throughout the environment
B. Increasing the number of analysts to identify risks that need remediation
C. Implementing a SOAR solution to address known threats
D. Integrating enterprise threat feeds in the existing SIEM
-
Question 343:
A systems administrator was given the following IOC to detect the presence of a malicious piece of software communicating with its command-and-control server:
1.
POST /malicious.php
2.
User-Agent: Malicious Tool V 1.0
3.
Host: www.malicious.com
The IOC documentation suggests the URL is the only part that could change. Which of the following regular expressions would allow the systems administrator to determine if any of the company hosts are compromised, while reducing false positives?
A. User-Agent: Malicious Tool.*
B. www\.malicious\.com\/malicious.php
C. Post /malicious\.php
D. Host: [a-z]*\.malicious\.com
E. malicious.*
-
Question 344:
In order to authenticate employees who, call in remotely, a company's help desk staff must be able to view partial information about employees because the full information may be considered sensitive. Which of the following solutions should be implemented to authenticate employees?
A. Data scrubbing
B. Field masking
C. Encryption in transit
D. Metadata
-
Question 345:
SIMULATION A. See the explanation below.
B. PlaceHoder
C. PlaceHoder
D. PlaceHoder
-
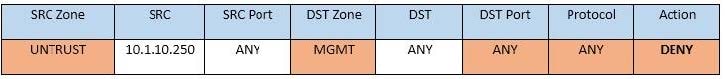
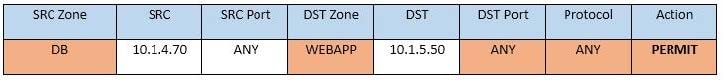
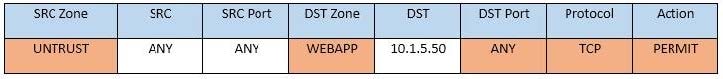
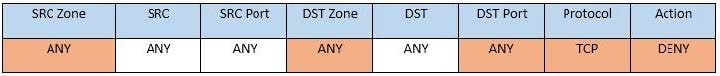
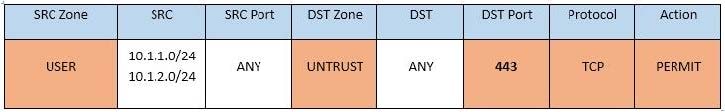
Question 346:
SIMULATION

Compliance with company policy requires a quarterly review of firewall rules. You are asked to conduct a review on the internal firewall sitting between several internal networks. The intent of this firewall is to make traffic more secure. Given
the following information perform the tasks listed below:
Untrusted zone: 0.0.0.0/0
User zone: USR 10.1.1.0/24
User zone: USR2 10.1.2.0/24
DB zone: 10.1.0/24
Web application zone: 10.1.5.0/24
Management zone: 10.1.10.0/24
Web server: 10.1.5.50
MS-SQL server: 10.1.4.70
MGMT platform: 10.1.10.250
Task 1) A rule was added to prevent the management platform from accessing the internet. This rule is not working. Identify the rule and correct this issue.
Task 2) The firewall must be configured so that the SQL server can only receive requests from the web server.
Task 3) The web server must be able to receive unencrypted requests from hosts inside and outside the corporate network.
Task 4) Ensure the final rule is an explicit deny.
Task 5) Currently the user zone can access internet websites over an unencrypted protocol. Modify a rule so that user access to websites is over secure protocols only.
Instructions: To perform the necessary tasks, please modify the DST port, SRC zone, Protocol, Action, and/or Rule Order columns. Type ANY to include all ports. Firewall ACLs are read from the top down. Once you have met the simulation
requirements, click Save. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
A. See the explanation below.
B. PlaceHoder
C. PlaceHoder
D. PlaceHoder
-
Question 347:
A security consultant has been asked to identify a simple, secure solution for a small business with a single access point. The solution should have a single SSID and no guest access. The customer facility is located in a crowded area of town, so there is a high likelihood that several people will come into range every day. The customer has asked that the solution require low administrative overhead and be resistant to offline password attacks. Which of the following should the security consultant recommend?
A. WPA2-Preshared Key
B. WPA3-Enterprise
C. WPA3-Personal
D. WPA2-Enterprise
-
Question 348:
city government's IT director was notified by the City council that the following cybersecurity requirements must be met to be awarded a large federal grant:
Logs for all critical devices must be retained for 365 days to enable monitoring and threat hunting. All privileged user access must be tightly controlled and tracked to mitigate compromised accounts. Ransomware threats and zero-day vulnerabilities must be quickly identified. Which of the following technologies would BEST satisfy these requirements? (Select THREE).
A. Endpoint protection
B. Log aggregator
C. Zero trust network access
D. PAM
E. Cloud sandbox
F. SIEM
G. NGFW
-
Question 349:
A security analyst at a global financial firm was reviewing the design of a cloud-based system to identify opportunities to improve the security of the architecture. The system was recently involved in a data breach after a vulnerability was exploited within a virtual machine's operating system. The analyst observed the VPC in which the system was located was not peered with the security VPC that contained the centralized vulnerability scanner due to the cloud provider's limitations. Which of the following is the BEST course of action to help prevent this situation m the near future?
A. Establish cross-account trusts to connect all VPCs via API for secure configuration scanning.
B. Migrate the system to another larger, top-tier cloud provider and leverage the additional VPC peering flexibility.
C. Implement a centralized network gateway to bridge network traffic between all VPCs.
D. Enable VPC traffic mirroring for all VPCs and aggregate the data for threat detection.
-
Question 350:
A company has moved its sensitive workloads lo the cloud and needs to ensure high availability and resiliency of its web-based application. The cloud architecture team was given the following requirements
The application must run at 70% capacity at all times The application must sustain DoS and DDoS attacks. Services must recover automatically.
Which of the following should the cloud architecture team implement? (Select THREE).
A. Read-only replicas
B. BCP
C. Autoscaling
D. WAF
E. CDN
F. Encryption
G. Continuous snapshots
H. Containenzation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.