Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 361:
A security analyst wants to keep track of alt outbound web connections from workstations. The analyst's company uses an on-premises web filtering solution that forwards the outbound traffic to a perimeter firewall. When the security analyst gets the connection events from the firewall, the source IP of the outbound web traffic is the translated IP of the web filtering solution. Considering this scenario involving source NAT. Which of the following would be the BEST option to inject in the HTTP header to include the real source IP from workstations?
A. X-Forwarded-Proto
B. X-Forwarded-For
C. Cache-Control
D. Strict-Transport-Security
E. Content-Security-Policy
-
Question 362:
A company is looking at sending historical backups containing customer PII to a cloud service provider to save on storage costs. Which of the following is the MOST important consideration before making this decision?
A. Availability
B. Data sovereignty
C. Geography
D. Vendor lock-in
-
Question 363:
An organization is deploying a new, online digital bank and needs to ensure availability and performance. The cloud-based architecture is deployed using PaaS and SaaS solutions, and it was designed with the following considerations:
Protection from DoS attacks against its infrastructure and web applications is in place.
Highly available and distributed DNS is implemented.
Static content is cached in the CDN.
A WAF is deployed inline and is in block mode.
Multiple public clouds are utilized in an active-passive architecture.
With the above controls in place, the bank is experiencing a slowdown on the unauthenticated payments page. Which of the following is the MOST likely cause?
A. The public cloud provider is applying QoS to the inbound customer traffic.
B. The API gateway endpoints are being directly targeted.
C. The site is experiencing a brute-force credential attack.
D. A DDoS attack is targeted at the CDN.
-
Question 364:
An organization recently recovered from an attack that featured an adversary injecting Malicious logic into OS bootloaders on endpoint devices Therefore, the organization decided to require the use of TPM for measured boot and attestation, monitoring each component from the IJEFI through the full loading of OS components. of the following TPM structures enables this storage functionality?
A. Endorsement tickets
B. Clock/counter structures
C. Command tag structures with MAC schemes
D. Platform configuration registers
-
Question 365:
A security analyst needs to recommend a remediation to the following threat:
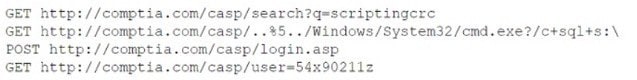
Which of the following actions should the security analyst propose to prevent this successful exploitation?
A. Patch the system.
B. Update the antivirus.
C. Install a host-based firewall.
D. Enable TLS 1.2.
-
Question 366:
A company's IT department currently performs traditional patching, and the servers have a significant longevity that may span over five years. A security architect is moving the company toward an immune server architecture in which servers are replaced rather than patched. Instead of having static servers for development, test, and production, the severs will move from environment to environment dynamically. Which of the following are required to move to this type of architecture? (Select Two.)
A. Network segmentation
B. Forward proxy
C. Netflow
D. Load balancers
E. Automated deployments
-
Question 367:
A municipal department receives telemetry data from a third-party provider The server collecting telemetry sits in the municipal departments screened network and accepts connections from the third party over HTTPS. The daemon has a code execution vulnerability from a lack of input sanitization of out-of-bound messages, and therefore, the cybersecurity engineers would like to Implement nsk mitigations. Which of the following actions, if combined, would BEST prevent exploitation of this vulnerability? (Select TWO).
A. Implementing a TLS inspection proxy on-path to enable monitoring and policy enforcement
B. Creating a Linux namespace on the telemetry server and adding to it the servicing HTTP daemon
C. Installing and configuring filesystem integrity monitoring service on the telemetry server
D. Implementing an EDR and alert on Identified privilege escalation attempts to the SIEM
E. Subscribing to a UTM service that enforces privacy controls between the internal network and the screened subnet
F. Using the published data schema to monitor and block off nominal telemetry messages
-
Question 368:
A system engineer is reviewing output from a web application vulnerability scan. The engineer has determined data is entering the application from an untrusted source and is being used to construct a query dynamically. Which of the following code snippets would BEST protect the application against an SQL injection attack?

A. String input = request.getParameter ("SegNo"); String characterPattern = "[0-9a-zA-Z]" If (! Input. Matches (characterPattern)) out.println ("Invalid Input");
B. '/>
C. catch (Exception e) if (log.isDebugEnabled ()) log.debug (context, EVENTS.ADHOC, "CaughtInvalidGSMException Exception --"
+ e.tostring ());
D.
-
Question 369:
A security analyst is reviewing an endpoint that was found to have a rookit installed. The rootkit survived multiple attempts to clean the endpoints, as well as an attempt to reinstall the QS. The security analyst needs to implement a method to prevent other endpoint from having similar issues. Which of the following would BEST accomplish this objective?
A. Utilize measured boot attestation.
B. Enforce the secure boot process.
C. Reset the motherboard's TPM chip.
D. Reinstall the OS with known-good media.
E. Configure custom anti-malware rules.
-
Question 370:
A corporation with a BYOD policy is very concerned about issues that may arise from data ownership. The corporation is investigating a new MDM solution and has gathered the following requirements as part of the requirements-gathering phase.
1.
Each device must be issued a secure token of trust from the corporate PKI.
2.
All corporate application and local data must be able to deleted from a central console.
3.
Cloud storage and backup applications must be restricted from the device.
4.
Devices must be on the latest OS version within three weeks of an OS release.
Which of the following should be feature in the new MDM solution to meet these requirement? (Select TWO.)
A. Application-based containerization
B. Enforced full-device encryption
C. Mandatory acceptance of SCEP system
D. Side-loaded application prevention
E. Biometric requirement to unlock device
F. Over-the-air restriction
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.