Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 381:
A hospital is deploying new imaging softwares that requires a web server for access to image for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following:
1.
The imaging server IP is 192.168.101.24
2.
The domain controller IP is 192.168.100.1
3.
The client machine IP is 192.168.200.37
Which of the following should be used to confirm this is the only open post on the web server?
A. nmap "p 80,443 192.168.101.24
B. nmap "p 80,443,389,636 192.168.100.1
C. nmap "p 80,389 192.168.200.37
D. nmap "p" 192.168.101.24
-
Question 382:
A security is testing a server finds the following in the output of a vulnerability scan:

Which of the following will the security analyst most likely use NEXT to explore this further?
A. Exploitation framework
B. Reverse engineering tools
C. Vulnerability scanner
D. Visualization tool
-
Question 383:
A company recently deployed an agent-based DLP solution to all laptop in the environment. The DLP solution is configured to restrict the following:
1.
USB ports
2.
FTP connections
3.
Access to cloud-based storage sites
4.
Outgoing email attachments
5.
Saving data on the local C: drive
6.
Despite these restrictions, highly confidential data was from a secure fileshare in the research department.
Which of the following should the security team implement FIRST?
A. Application whitelisting for all company-owned devices
B. A secure VDI environment for research department employees
C. NIDS/NIPS on the network segment used by the research department
D. Bluetooth restriction on all laptops
-
Question 384:
Which of the following is the MOST likely reason an organization would decide to use a BYOD policy?
A. It enables employees to use the devices they are already own, thus reducing costs.
B. It should reduce the number of help desk and tickets significantly.
C. It is most secure, as the company owns and completely controls the devices.
D. It is the least complex method for systems administrator to maintain over time.
-
Question 385:
The Chief Information Security Officer (CISO) of a new company is looking for a comprehensive assessment of the company's application services Which of the following would provide the MOST accurate number of weaknesses?
A. White-box penetration test
B. Internal vulnerability scanning
C. Internal controls audit
D. Third-party red-team engagement
-
Question 386:
Within change management, winch of the following ensures functions are earned out by multiple employees?
A. Least privilege
B. Mandatory vacation
C. Separator of duties
D. Job rotation
-
Question 387:
An organization is creating requirements for new laptops that will be issued to staff One of the company's key security objectives is to ensure the laptops nave hardware-enforced data-at-rest protection tied to permanent hardware identities. The laptops must also provide attestation for secure boot processes To meet these demands, which of the following BEST represent the features that should be included in the requirements set? (Select TWO.)
A. TPM2.0e
B. Opal support
C. MicroSD token authenticator
D. TLS1.3
E. Shim and GRUB
F. ARMv7 with TrustZone
-
Question 388:
A security administrator is confirming specific ports and IP addresses that are monitored by the IPS- IDS system as well as the firewall placement on the perimeter network between the company and a new business partner Which of the following business documents defines the parameters the security administrator must confirm?
A. BIA
B. ISA
C. NDA
D. MOU
-
Question 389:
An administrator wants to ensure hard drives cannot be removed from hosts and men installed into and read by unauthorized hosts Which of the following techniques would BEST support this?
A. Access control lists
B. TACACS+ server for AAA
C. File-level encryption
D. TPM with sealed storage
-
Question 390:
A security analyst is comparing two virtual servers that were bum from the same image and patched at the same regular intervals Server A is used to host a public-facing website, and Server B runs accounting software inside the firewalled accounting network. The analyst runs the same command and obtains the following output from Server A and Server B. respectively:
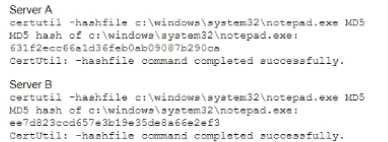
Which of the following will the analyst most likely use NEXT?
A. Exploitation tools
B. Hash cracking tools
C. Malware analysis tools
D. Log analysis tools
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.