Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 391:
A security analyst is attempting to identify code that is vulnerable to butler and integer overflow attacks. Which of the following code snippets is safe from these types of attacks?
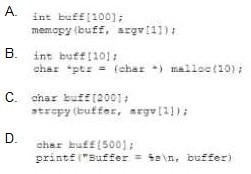
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 392:
A system administrator recently conducted a vulnerability scan of the internet. Subsequently, the organization was successfully attacked by an adversary. Which of the following in the MOST likely explanation for why the organization network was compromised?
A. There was a false positive since the network was fully patched.
B. The system administrator did not perform a full system sun.
C. The systems administrator performed a credentialed scan.
D. The vulnerability database was not updated.
-
Question 393:
A developer needs to provide feedback on a peer's work during the SDLC. While reviewing the code changes, the developers session ID tokens for a web application will be transmitted over an unsecure connection. Which of the following code snippets should the developer recommend implement to correct the vulnerability?
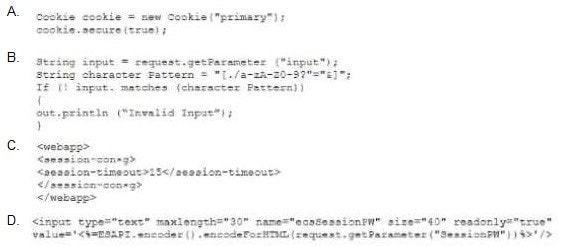
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 394:
A hospital is deploying new imaging software that requires a web server for access to images for both local and remote users. The web server allows user authentication via secure LDAP. The information security officer wants to ensure the server does not allow unencrypted access to the imaging server by using Nmap to gather additional information. Given the following:
1.
The imaging server IP is 192.168.101.24.
2.
The domain controller IP is 192.168.100.1.
3.
The client machine IP is 192.168.200.37.
Which of the following should be used to confirm this is the only open port on the web server?
A. nmap -p 80,443 192.168.101.24
B. nmap -p 80, 443,389,636 192.168.100.1
C. nmap --p 80,389 192.168.200.37
D. nmap -p- 192.168.101.24
-
Question 395:
A security researcher at an organization is reviewing potential threats to the VoIP phone system infrastructure, which uses a gigabit Internet connection. The researcher finds a vulnerability and knows placing an IPS in front of the phone system will mitigate the risk. The researcher gathers the following information about various IPS systems:
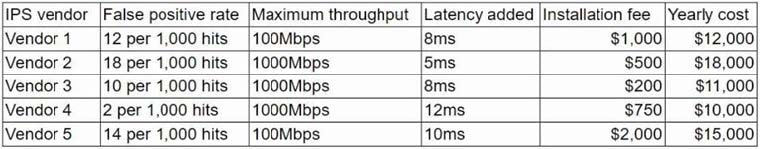
The organization is concerned about cost, but call quality is critical to its operations. Which of the following vendors would be BEST for the organization to choose?
A. Vendor 1
B. Vendor 2
C. Vendor 3
D. Vendor 4
E. Vendor 5
-
Question 396:
A security manager wants to standardize security settings, firmware, and software across a heterogeneous environment. Which of the following can be used in combination to meet these goals? (Choose three).
A. Attestation services
B. TPM
C. HIPS software
D. OOB management software
E. Group Policy
F. EDR software
G. MDM software
-
Question 397:
A server was compromised recently, and two unauthorized daemons were set up to listen for incoming connections. In addition, CPU cycles were being used by an additional unauthorized cron job. Which of the following would have prevented the breach if it was properly configured?
A. Set up log forwarding and utilize a SIEM for centralized management and alerting.
B. Use a patch management system to close the vulnerabilities in a shorter time frame.
C. Implement a NIDS/NIPS.
D. Deploy SELinux using the system baseline as the starting point.
E. Configure the host firewall to block unauthorized inbound connections.
-
Question 398:
A company that uses AD is migrating services from LDAP to secure LDAP. During the pilot phase, services are not connecting properly to secure LDAP. Block is an except of output from the troubleshooting session:
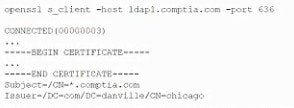
Which of the following BEST explains why secure LDAP is not working? (Select TWO.)
A. The clients may not trust idapt by default.
B. The secure LDAP service is not started, so no connections can be made.
C. Danvills.com is under a DDoS-inator attack and cannot respond to OCSP requests.
D. Secure LDAP should be running on UDP rather than TCP.
E. The company is using the wrong port. It should be using port 389 for secure LDAP.
F. Secure LDAP does not support wildcard certificates.
G. The clients may not trust Chicago by default.
-
Question 399:
A penetration tester is trying to gain access to a building after hours as part of a physical assessment of an office complex. The tester notes that each employee touches a badge near a small black box outside the side door, and the door unlocks. The tester uses a software-defined radio tool to determine a 125kHz signal is used during this process. Which of the following technical solutions would be BEST to help the penetration tester gain access to the building?
A. Generate a 125kHz tone.
B. Compromise the ICS/SCADA system.
C. Utilize an RFID duplicator.
D. Obtain a lock pick set.
-
Question 400:
An organization that develops military technology is considering expansion into a foreign country. The organization's owners want to understand the risks associated with such an expansion, and the organization does not want to fund an intensive assessment. Which of the following approaches should be taken?
A. Penetration test
B. Tabletop assessment
C. Compliance assessment
D. Configuration security test
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.