Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 421:
A health company has reached the physical and computing capabilities in its datacenter, but the computing demand continues to increase. The infrastructure is fully virtualized and runs custom and commercial healthcare application that process sensitive health and payment information. Which of the following should the company implement to ensure it can meet the computing demand while complying with healthcare standard for virtualization and cloud computing?
A. Hybrid IaaS solution in a single-tenancy cloud
B. Pass solution in a multinency cloud
C. SaaS solution in a community cloud
D. Private SaaS solution in a single tenancy cloud.
-
Question 422:
A company is outsourcing to an MSSP that performs managed detection and response services. The MSSP requires a server to be placed inside the network as a log aggregate and allows remote access to MSSP analyst. Critical devices send logs to the log aggregator, where data is stored for 12 months locally before being archived to a multitenant cloud. The data is then sent from the log aggregate to a public IP address in the MSSP datacenter for analysis.
A security engineer is concerned about the security of the solution and notes the following:
1.
The critical devise send cleartext logs to the aggregator.
2.
The log aggregator utilize full disk encryption.
3.
The log aggregator sends to the analysis server via port 80.
4.
MSSP analysis utilize an SSL VPN with MFA to access the log aggregator remotely.
5.
The data is compressed and encrypted prior to being achieved in the cloud.
Which of the following should be the engineer's GREATEST concern?
A. Hardware vulnerabilities introduced by the log aggregate server
B. Network bridging from a remote access VPN
C. Encryption of data in transit
D. Multinancy and data remnants in the cloud
-
Question 423:
A cybersecurity analyst created the following tables to help determine the maximum budget amount the business can justify spending on an improved email filtering system:
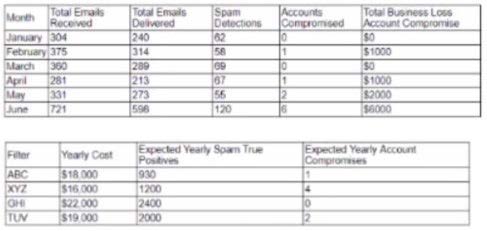
Which of the following meets the budget needs of the business?
A. Filter ABC
B. Filter XYZ
C. Filter GHI
D. Filter TUV
-
Question 424:
A security is assisting the marketing department with ensuring the security of the organization's social media platforms. The two main concerns are:
1.
The Chief marketing officer (CMO) email is being used department wide as the username
2.
The password has been shared within the department
Which of the following controls would be BEST for the analyst to recommend?
A. Configure MFA for all users to decrease their reliance on other authentication.
B. Have periodic, scheduled reviews to determine which OAuth configuration are set for each media platform.
C. Create multiple social media accounts for all marketing user to separate their actions.
D. Ensue the password being shared is sufficiently and not written down anywhere.
-
Question 425:
A company's Chief Information Security Officer (CISO) is working with the product owners to perform a business impact assessment. The product owners provide feedback related to the critically of various business processes, personal, and technologies. Transitioning into risk assessment activities, which of the following types of information should the CISO require to determine the proper risk ranking? (Select TWO).
A. Trend analysis
B. Likelihood
C. TCO
D. Compensating controls
E. Magnitude
F. ROI
-
Question 426:
A security analyst is reviewing the following pseudo-output snippet after running the command less /tmp/file,tmp.

The information above was obtained from a public-facing website and used to identify military assets. Which of the following should be implemented to reduce the risk of a similar compromise?
A. Deploy a solution to sanitize geotagging information
B. Install software to wipe data remnants on servers
C. Enforce proper input validation on mission-critical software
D. Implement a digital watermarking solution
-
Question 427:
Over the last 90 days, many storage services has been exposed in the cloud services environments, and the security team does not have the ability to see is creating these instance. Shadow IT is creating data services and instances faster than the small security team can keep up with them. The Chief information security Officer (CIASO) has asked the security officer (CISO) has asked the security lead architect to architect to recommend solutions to this problem.
Which of the following BEST addresses the problem best address the problem with the least amount of administrative effort?
A. Compile a list of firewall requests and compare than against interesting cloud services.
B. Implement a CASB solution and track cloud service use cases for greater visibility.
C. Implement a user-behavior system to associate user events and cloud service creation events.
D. Capture all log and feed then to a SIEM and then for cloud service events
-
Question 428:
A developer implement the following code snippet.

Which of the following vulnerabilities does the code snippet resolve?
A. SQL inject
B. Buffer overflow
C. Missing session limit
D. Information leakage
-
Question 429:
A security engineer at a company is designing a system to mitigate recent setbacks caused competitors that are beating the company to market with the new products. Several of the products incorporate propriety enhancements developed by the engineer's company. The network already includes a SEIM and a NIPS and requires 2FA for all user access. Which of the following system should the engineer consider NEXT to mitigate the associated risks?
A. DLP
B. Mail gateway
C. Data flow enforcement
D. UTM
-
Question 430:
Company A is establishing a contractual with Company B. The terms of the agreement are formalized in a document covering the payment terms, limitation of liability, and intellectual property rights. Which of the following documents will MOST likely contain these elements
A. Company A-B SLA v2.docx
B. Company A OLA v1b.docx
C. Company A MSA v3.docx
D. Company A MOU v1.docx
E. Company A-B NDA v03.docx
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.