Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 441:
A systems engineer is reviewing output from a web application vulnerability scan. The engineer has determined data is entenng the application from an untrusted source and is being used to construct a query dynamically. Which of the following code snippets would BEST protect the application against an SQL injection attack?
A. String input = request.getParameter ("SeqNo"); String characterPattern = "[0-9a0zA-Z] If (! input. Matches (characterPattern)) { out.println ("Invalid Input"); }
B. Cinput type= "text" maxlength= "30" name= "ecsChangePwdForm" size= "40" readonly= "true" value= '<%=ESAPI.encoder().encodeForHTML (request.getParameter("userName")) %>'/>
C. catch (Exception e) { if (log.isDebugEnabled()) log.debug (context, EVENTS.ADHOC, "Caught InvalidGSMException Exception --"
+ e.toString() );
}
D.
-
Question 442:
The email administrator must reduce the number of phishing emails by utilizing more appropriate security controls. The following configurations already are in place:
1.
Keyword blocking based on word lists
2.
URL rewnting and protection
3.
Stopping executable files from messages
Which of the following is the BEST configuration change for the administrator to make?
A. Configure more robust word lists for blocking suspicious emails
B. Configure appropriate regular expression rules per suspicious email received
C. Configure Bayesian filtering to block suspicious inbound email
D. Configure the mail gateway to strip any attachments.
-
Question 443:
A security auditor needs to review the manner in which an entertainment streaming device operates The auditor is analyzing the output of a port scanning tool to determine the next steps in the security review. Given the following log output:
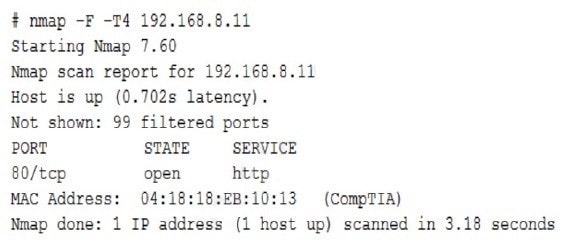
The best option for the auditor to use NEXT is:
A. a SCAP assessment
B. reverse engineering
C. fuzzing
D. network interception
-
Question 444:
A security administrator wants to implement an MDM solution to secure access to company email and files in a BYOD environment The solution must support the following requirements:
1.
Company administrators should not have access to employee's personal information.
2.
A rooted or jailbroken device should not have access to company sensitive information. Which of the following BEST addresses the associated risks?
A. Codesigning
B. VPN
C. FDE
D. Containerization
-
Question 445:
Ann. a user, brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output:
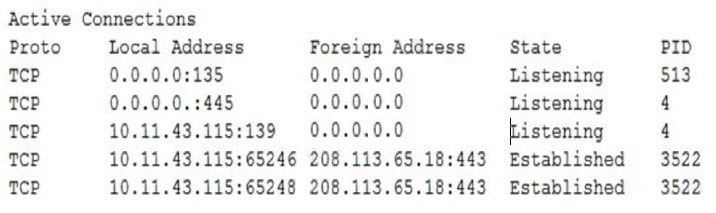
Which of the following will the analyst most likely use NEXT?
A. Process explorer
B. Vulnerability scanner
C. Antivirus
D. Network enumerator
-
Question 446:
A security analyst is trying to identify the source of a recent data loss incident The analyst has reviewed all the logs for the time surrounding the incident and identified all the assets on the network at the time of the data loss. The analyst suspects the key to finding the source was obfuscated in an application.
Which of the following tools should the analyst use NEXT?
A. Software decompiler
B. Network enumerator
C. Log reduction and analysis tool
D. Static code analysis
-
Question 447:
A penetration tester is given an assignment to gam physical access to a secure facility with perimeter cameras. The secure facility does not accept visitors, and entry is available only through a door protected by an RFID key and a guard stationed inside the door.
Which of the following would be BEST for the penetration tester to attempt?
A. Gain entry into the building by posing as a contractor who is performing routine building maintenance
B. Tailgate into the facility with an employee who has a valid RFID badge to enter
C. Duplicate an employee's RFID badge and use an IR camera to see when the guard leaves the post
D. Look for an open window that can be used to gain unauthorized entry into the facility.
-
Question 448:
security analyst is validating the MAC policy on a set of Android devices The policy was written to ensure non-cntical applications are unable to access certain resources. When reviewing dmesg, the analyst notes many entries, such as:
avc: denied { open } for pid=1018 comm= "ire" path= "/dev/if0" dev= "tmpfs" scontext=u:r:irc:sO tcontext=u:object_r:default:s0 tclass=chr_file permissive=l
Despite the deny message, this action was still permitted Which of the following is the MOST likely fix for this issue?
A. Add the objects of concern to the default context
B. Set the devices to enforcing mode
C. Create separate domain and context files for irc
D. Rebuild the sepolicy, reinstall, and test
-
Question 449:
Following the most recent patch deployment, a security engineer receives reports that the ERP application is no longer accessible The security engineer reviews the situation and determines a critical secunty patch that was applied to the ERP server is the cause. The patch is subsequently backed out.
Which of the following security controls would be BEST to implement to mitigate the threat caused by the missing patch?
A. Anti-malware
B. Patch testing
C. HIPS
D. Vulnerability scanner
-
Question 450:
A company's internet connection is commonly saturated during business hours, affecting internet availability. The company requires all Internet traffic to be business related After analyzing the traffic over a period of a few hours, the security administrator observes the following:
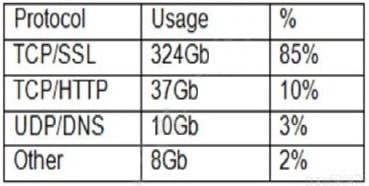
The majority of the IP addresses associated with the TCP/SSL traffic resolve to CDNs
Which of the following should the administrator recommend for the CDN traffic to meet the corporate security requirements?
A. Block outbound SSL traffic to prevent data exfiltration.
B. Confirm the use of the CDN by monitoring NetFlow data.
C. Further investigate the traffic using a sanctioned MITM proxy.
D. Implement an IPS to drop packets associated with the CDN.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.