Exam Details
Exam Code
:CAS-004Exam Name
:CompTIA Advanced Security Practitioner (CASP+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:743 Q&AsLast Updated
:
CompTIA CompTIA Certifications CAS-004 Questions & Answers
-
Question 61:
IoCs were missed during a recent security incident due to the reliance on a signature-based detection platform. A security engineer must recommend a solution that can be implemented to address this shortcoming. Which of the following would be the most appropriate recommendation?
A. FIM
B. SASE
C. UEBA
D. CSPM
E. EAP
-
Question 62:
A security analyst discovers a new device on the company's dedicated IoT subnet during the most recent vulnerability scan. The scan results show numerous open ports and insecure protocols in addition to default usernames and passwords. A camera needs to transmit video to the security server in the IoT subnet. Which of the following should the security analyst recommend to securely operate the camera?
A. Harden the camera configuration.
B. Send camera logs to the SIEM.
C. Encrypt the camera's video stream.
D. Place the camera on an isolated segment.
-
Question 63:
An application engineer is using the Swagger framework to leverage REST APIs to authenticate endpoints. The engineer is receiving HTTP 403 responses. Which of the following should the engineer do to correct this issue? (Choose two.)
A. Obtain a security token.
B. Obtain a public key.
C. Leverage Kerberos for authentication
D. Leverage OAuth for authentication.
E. Leverage LDAP for authentication.
F. Obtain a hash value.
-
Question 64:
To bring digital evidence in a court of law the evidence must be:
A. material
B. tangible
C. consistent
D. conserved
-
Question 65:
A compliance officer is responsible for selecting the right governance framework to protect individuals' data. Which of the following is the appropriate framework for the company to consult when collecting international user data for the purpose of processing credit cards?
A. ISO 27001
B. COPPA
C. NIST 800-53
D. PCI DSS
-
Question 66:
To bring digital evidence in a court of law, the evidence must be:
A. material.
B. tangible.
C. consistent.
D. conserved.
-
Question 67:
A company's software developers have indicated that the security team takes too long to perform application security tasks. A security analyst plans to improve the situation by implementing security into the SDLC. The developers have the following requirements:
1.
The solution must be able to initiate SQL injection and reflected XSS attacks.
2.
The solution must ensure the application is not susceptible to memory leaks.
Which of the following should be implemented to meet these requirements? (Choose two.)
A. Side-channel analysis
B. Protocol scanner
C. HTTP interceptor
D. DAST
E. Fuzz testing
F. SAST
G. SCAP
-
Question 68:
A company has received threat intelligence about bad routes being advertised. The company has also been receiving reports of degraded internet activity. When looking at the routing table on the edge router, a security engineer discovers the following:
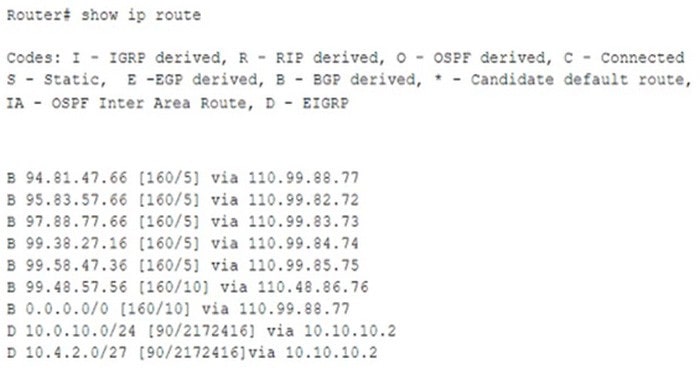
Which of the following can the company implement to prevent receiving bad routes from peers, while still allowing dynamic updates?
A. OSPF prefix list
B. BGP prefix list
C. EIGRP prefix list
D. DNS
-
Question 69:
A financial institution generates a list of newly created accounts and sensitive information on a daily basis. The financial institution then sends out a file containing thousands of lines of data. Which of the following would be the best way to reduce the risk of a malicious insider making changes to the file that could go undetected?
A. Write a SIEM rule that generates a critical alert when files are created on the application server.
B. Implement a FIM that automatically generates alerts when the file is accessed by IP addresses that are not associated with the application.
C. Create a script that compares the size of the file on an hourly basis and generates alerts when changes are identified.
D. Tune the rules on the host-based IDS for the application server to trigger automated alerts when the application server is accessed from the internet.
-
Question 70:
A security engineer is re-architecting a network environment that provides regional electric distribution services. During a pretransition baseline assessment, the engineer identified the following security-relevant characteristics of the environment:
1.
Enterprise IT servers and supervisory industrial systems share the same subnet.
2.
Supervisory controllers use the 750MHz band to direct a portion of fielded PLCs.
3.
Command and telemetry messages from industrial control systems are unencrypted and unauthenticated.
Which of the following re-architecture approaches would be best to reduce the company's risk?
A. Implement a one-way guard between enterprise IT services and mission-critical systems, obfuscate legitimate RF signals by broadcasting noise, and implement modern protocols to authenticate ICS messages.
B. Characterize safety-critical versus non-safety-critical systems, isolate safety-critical systems from other systems, and increase the directionality of RF links in the field.
C. Create a new network segment for enterprise IT servers, configure NGFW to enforce a well-defined segmentation policy, and implement a WIDS to monitor the spectrum.
D. Segment supervisory controllers from field PLCs, disconnect the entire network from the internet, and use only the 750MHz link for controlling energy distribution services.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CAS-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.