Exam Details
Exam Code
:CV0-003Exam Name
:CompTIA Cloud+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:503 Q&AsLast Updated
:Mar 26, 2025
CompTIA CompTIA Certifications CV0-003 Questions & Answers
-
Question 451:
A company's website is continuously being brute forced, and its users have reported multiple account intrusions in the last few months. All users are using passwords that are at least 12 characters long. The systems administrator needs to implement a control that will mitigate this issue without negatively affecting the user experience. Which of the following should the administrator implement to achieve the objective?
A. Account lockout
B. Progressive login delay
C. Reduced password complexity
D. Increased password length
-
Question 452:
A small marketing company recently moved all of its storage to a cloud provider. The budget for storage has limited the company to buying a small amount of SSD storage and a lot of spinning disks. The storage administrator needs to find a way to optimize this environment to realize maximum speed. Which of the following would best achieve this?
A. Compression
B. Automated storage tiering
C. Deduplication
D. Autoscaling
-
Question 453:
A systems administrator is implementing a file storage solution that stores files using integrity verification. Which of the following algorithms is most resistant to collisions?
A. SHA-2
B. MD5
C. CRC32
D. RIPEMD-160
-
Question 454:
A cloud engineer is troubleshooting poor performance that was reported on the corporate website. The website was configured behind a cloud application load balancer, and the following output was collected on the cloud console:
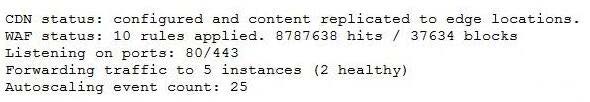
Based on the provided output, which of the following options is the most likely cause of the issue?
A. The web servers are not responding properly.
B. The web firewall is blocking legitimate traffic.
C. The CDN should not be used during high loads.
D. Autoscaling events are too high.
-
Question 455:
A public cloud administrator needs to implement a mechanism to monitor the expense of the company's cloud resources. Which of the following options will allow the administrator to execute this task fastest way and with minimal effort?
A. Set up daily expense reports with the cloud provider.
B. Enable custom notifications for exceeding budget thresholds.
C. Use the API to collect expense information from cloud resources.
D. Implement a financial tool to monitor cloud resource expenses.
-
Question 456:
Which of the following design factors would an MSP use to build cloud service offerings?
A. Public
B. Community
C. Private
D. Multitenancy
-
Question 457:
A systems administrator wants to ensure a system can adjust its resources based on usage. Which of the following will best accomplish this goal?
A. Anti-affinity
B. Autoscaling
C. Right-sizing
D. Oversubscription
-
Question 458:
A cloud architect is receiving complaints from VDI users overseas about slowness even though the remote office has Gigabit internet. Which of the following will most likely solve the issue?
A. Increasing bandwidth
B. Enabling compression
C. Lowering latency
D. Adding redundancy
-
Question 459:
A systems administrator receives a ticket stating the following:
“The programming team received an error during the process deploying applications to the container platform. The error after the containerized applications were created”
Which the following should the administrator Check FIRST?
A. The containers
B. The application
C. The Scripts
D. The templates
-
Question 460:
CORRECT TEXT
The QA team is testing a newly implemented clinical trial management (CTM) SaaS application that uses a business intelligence application for reporting. The UAT users were instructed to use HTTP and HTTPS.
Refer to the application dataflow:
1A -The end user accesses the application through a web browser to enter and view clinical data.
2A -The CTM application server reads/writes data to/from the database server.
1B -The end user accesses the application through a web browser to run reports on clinical data.
2B -The CTM application server makes a SOAP call on a non-privileged port to the BI application server.
3B -The BI application server gets the data from the database server and presents it to the CTM application server.
When UAT users try to access the application using https://ctm.app.com or http://ctm.app.com, they get a message stating: "Browser cannot display the webpage." The QA team has raised a ticket to troubleshoot the issue.
INSTRUCTIONS
You are a cloud engineer who is tasked with reviewing the firewall rules as well as virtual network settings.
You should ensure the firewall rules are allowing only the traffic based on the dataflow.
You have already verified the external DNS resolution and NAT are working.
Verify and appropriately configure the VLAN assignments and ACLs. Drag and drop the appropriate VLANs to each tier from the VLAN Tags table. Click on each Firewall to change ACLs as needed.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
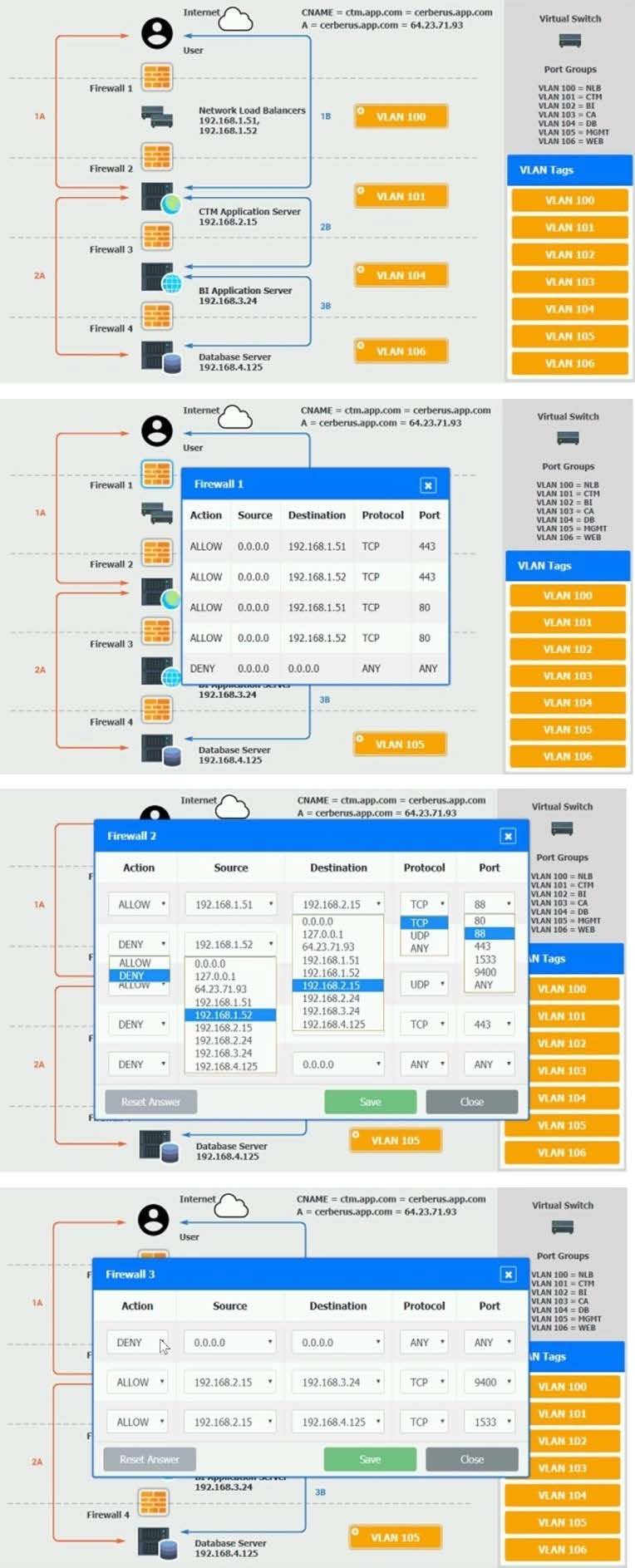
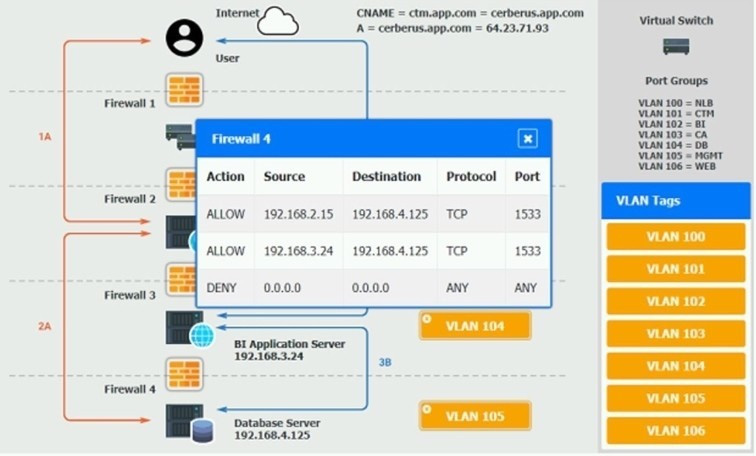
A. Check the answer in explanation.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CV0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.