Exam Details
Exam Code
:CV0-004Exam Name
:CompTIA Cloud+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:285 Q&AsLast Updated
:
CompTIA CompTIA Certifications CV0-004 Questions & Answers
-
Question 131:
An organization's internal security team mandated that public cloud resources must be accessible only by a corporate VPN and not by direct public internet access.
Which of the following would achieve this objective?
A. WAF
B. ACL
C. VPC
D. SSH
-
Question 132:
Which of the following is an auditing procedure that ensures service providers securely manage the data to protect the interests of the organization and the privacy of its clients?
A. CIS
B. ITIL
C. SOC2
D. ISO 27001
-
Question 133:
A systems administrator is provisioning VMs according to the following requirements:
5.
A VM instance needs to be present in at least two data centers.
6.
During replication, the application hosted on the VM tolerates a maximum latency of one second.
7.
When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
A. Snapshot
B. Transactional
C. Live
D. Point-in-time
-
Question 134:
A cloud engineer wants containers to run the latest version of a container base image to reduce the number of vulnerabilities. The applications in use requite Python 3.10 and ate not compatible with any other version. The containers' images are created every time a new version is released from the source image. Given the container Dockerfile below: Which of the following actions will achieve the objectives with the least effort?
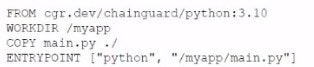
A. Perform docker pull before executing docker run.
B. Execute docker update using a local cron to get the latest container version.
C. Change the image to use python:latest on the image build process.
D. Update the Dockerfile to pin the source image version.
-
Question 135:
A cloud engineer wants to implement a monitoring solution to detect cryptojacking and other cryptomining malware on cloud instances. Which of the following metrics would most likely be used to identify the activity?
A. Disk I/O
B. Network packets
C. Average memory utilization
D. Percent of CPU utilization
-
Question 136:
An organization's critical data was exfiltrated from a computer system in a cyberattack. A cloud analyst wants to identify the root cause and is reviewing the following security logs of a software web application:
"2021/12/18 09:33:12" "10. 34. 32.18" "104. 224. 123. 119" "POST / login.php?u=administratorandp=or%201%20=1"
"2021/12/18 09:33:13" "10.34. 32.18" "104. 224. 123.119" "POST /login.php?u=administratorandp=%27%0A"
"2021/12/18 09:33:14" "10. 34. 32.18" "104. 224. 123. 119" "POST /login.php?u=administratorandp=%26"
"2021/12/18 09:33:17" "10.34. 32.18" "104. 224. 123.119" "POST / login.php?u=administratorandp=%3B"
"2021/12/18 09:33:12" "10.34. 32. 18" "104. 224. 123. 119" "POST / login.php?u=adminandp=or%201%20=1"
"2021/12/18 09:33:19" "10.34.32.18" "104. 224. 123.119" "POST / login.php?u=adminandp=%27%0A"
"2021/12/18 09:33:21" "10. 34. 32.18" "104.224. 123.119" "POST / login.php?u=adminandp=%26"
"2021/12/18 09:33:23" "10. 34. 32.18" "104. 224. 123.119" "POST / login.php?u=adminandp=%3B"
Which of the following types of attacks occurred?
A. SQL injection
B. Cross-site scripting
C. Reuse of leaked credentials
D. Privilege escalation
-
Question 137:
Which of the following describes what CRUD is typically used for?
A. Relational databases
B. Time series databases
C. Graph databases
D. NoSQL databases
-
Question 138:
A developer is deploying a new version of a containerized application. The DevOps team wants:
1.
No disruption
2.
No performance degradation
3.
Cost-effective deployment
4.
Minimal deployment time
Which of the following is the best deployment strategy given the requirements?
A. Canary
B. In-place
C. Blue-green
D. Rolling
-
Question 139:
A cloud engineer is designing a high-performance computing cluster for proprietary software. The software requires low network latency and high throughput between cluster nodes.
Which of the following would have the greatest impact on latency and throughput when designing the HPC infrastructure?
A. Node placement
B. Node size
C. Node NIC
D. Node OS
-
Question 140:
An administrator used a script that worked in the past to create and tag five virtual machines. All of the virtual machines have been created: however, the administrator sees the following results:
{ tags: [ ] }
Which of the following is the most likely reason for this result?
A. API throttling
B. Service quotas
C. Command deprecation
D. Compatibility issues
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CV0-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.