Exam Details
Exam Code
:CV0-004Exam Name
:CompTIA Cloud+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:285 Q&AsLast Updated
:Apr 01, 2025
CompTIA CompTIA Certifications CV0-004 Questions & Answers
-
Question 141:
A cloud architect attempts to modify a protected branch but is unable to do so. The architect receives an error indicating the action cannot be completed. Which of the following should the architect try instead?
A. Adding a new remote
B. Creating a pull request
C. Merging the branch
D. Rebasing the branch
-
Question 142:
A company uses containers stored in Docker Hub to deploy workloads (or its laaS infrastructure. The development team releases changes to the containers several times per hour.
Which of the following should a cloud engineer do to prevent the proprietary code from being exposed to third parties?
A. Use laC to deploy the laaS infrastructure.
B. Convert the containers to VMs.
C. Deploy the containers over SSH.
D. Use private repositories for the containers.
-
Question 143:
The company's IDS has reported an anomaly. The cloud engineer remotely accesses the cloud instance, runs a command, and receives the following information:
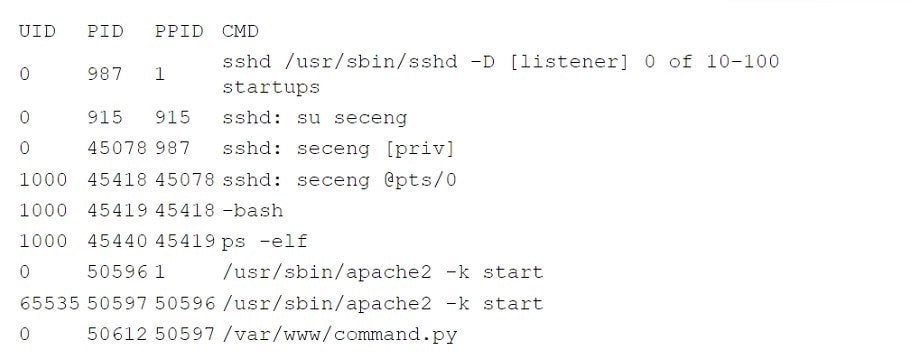
Which of the following is the most likely root cause of this anomaly?
A. Privilege escalation
B. Leaked credentials
C. Cryptojacking
D. Defaced website
-
Question 144:
A government agency in the public sector is considering a migration from on premises to the cloud. Which of the following are the most important considerations for this cloud migration? (Select two).
A. Compliance
B. laaS vs. SaaS
C. Firewall capabilities
D. Regulatory
E. Implementation timeline
F. Service availability
-
Question 145:
Which of the following compute resources is the most optimal for running a single scripted task on a schedule?
A. Bare-metal server
B. Managed container
C. Virtual machine
D. Serverless function
-
Question 146:
Which of the following container storage types loses data after a restart?
A. Object
B. Persistent volume
C. Ephemeral
D. Block
-
Question 147:
A cloud security analyst is looking for existing security vulnerabilities on software applications. Which of the following describes this vulnerability management phase?
A. Analyze
B. Report
C. Remediation
D. identification
-
Question 148:
Which of the following cloud-native architecture designs is the most easily maintained, decentralized, and decoupled?
A. Monolithic
B. Hybrid cloud
C. Mainframe
D. Microservices
-
Question 149:
A log-parsing application requires significant processing power to ingest the logs streaming from web servers. The engineering team presents the cloud architect with four proposals using the same underlying hardware.
Which of the following should the cloud architect select in order to minimize the impact of an instance failure while keeping the cost as low as possible?
A. Four instances of 4vCPU, 8GB RAM, 80GB SSD
B. Four instances of 4vCPU, 8GB RAM, 80GB HDD
C. Two instances of 8vCPU, 16GB RAM, 80GB SSD
D. Two instances of 8vCPU, 16GB RAM, 80GB HDD
-
Question 150:
Which of the following is used to detect signals and measure physical properties, such as the temperature of the human body?
A. Beacon
B. Transmission protocols
C. Sensors
D. Gateways
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CV0-004 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.