Exam Details
Exam Code
:DEA-2TT3Exam Name
:Dell EMC Cloud Infrastructure and Services v3 (DEA-2TT3)Certification
:EMC CertificationsVendor
:EMCTotal Questions
:66 Q&AsLast Updated
:Apr 10, 2025
EMC EMC Certifications DEA-2TT3 Questions & Answers
-
Question 1:
What are the key approaches to application transformation?
A. Restore, Reuse, Retain, Retire
B. Refactor, Revise, Retain, Retire
C. Retain, Refactor, Reuse, Revise
D. Revise, Restore, Retain, Re-iterate
-
Question 2:
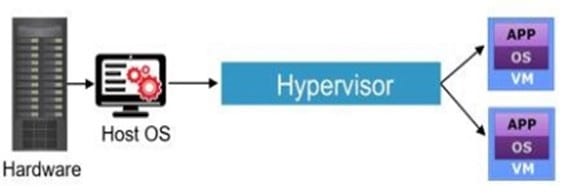
Refer to the exhibit.
Which type of hypervisor is installed in this environment?
A. Hosted Hypervisor-Type 1
B. Bare Metal Hypervisor-Type 1
C. Hosted Hypervisor-Type 2
D. Bare Metal Hypervisor-Type 2
-
Question 3:
What is a key function of the cloud service component?
A. Allows consumers to create service offerings for a service catalog
B. Enables service providers to request the purchase of new IT resources
C. Presents cloud infrastructure for use of services by consumers
D. Allows consumers to modify the existing service offerings in a service catalog
-
Question 4:
Which method compares observed events with normal activities to identify abnormal patterns in a system?
A. Encryption-based authentication
B. Anomaly-based intrusion detection
C. Multi-factor authentication
D. Signature-based intrusion detection
-
Question 5:
In which technique does an application maintain limited functionality, even when some of the modules or supporting services of that application become unavailable?
A. Retry logic
B. Persistent state model
C. Graceful degradation
D. Checkpointing
-
Question 6:
To implement a new service desk management tool, the capacity of the servers has to be extended. Who is responsible for managing the request for additional capacity?
A. Change Manager
B. Financial Manager
C. Capacity Manager
D. Service Level Manager
-
Question 7:
Which Dell EMC product provides a converged infrastructure solution?
A. XC Series Appliance
B. VxBlock
C. VxRail Appliance
D. XtremIO
-
Question 8:
What is a service contract?
A. Agreement between provider and consumer that states the terms of service usage
B. Agreement between provider and supplier that describes the service template specifics
C. Agreement between provider and consumer that lists the conditions for greenfield service deployment D. Agreement between provider and supplier that states the terms and conditions of a balanced scorecard
-
Question 9:
An organization deployed a storage system that is configured with erasure coding. The erasure coding technique divides data into five data segments and two coding segments.
What is the maximum number of drive failures supported in the storage system?
A. 2
B. 5
C. 7
D. 10
-
Question 10:
An organization wants to deploy performance sensitive applications to meet their business requirements. Which type of storage device is suitable?
A. SATA drive
B. Solid-state drive
C. SAS drive
D. Optical disk drive
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your DEA-2TT3 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.