Exam Details
Exam Code
:DEA-2TT3Exam Name
:Dell EMC Cloud Infrastructure and Services v3 (DEA-2TT3)Certification
:EMC CertificationsVendor
:EMCTotal Questions
:66 Q&AsLast Updated
:Mar 23, 2025
EMC EMC Certifications DEA-2TT3 Questions & Answers
-
Question 21:
A specific intrusion detection and prevention system (IDPS) scans events against known attack patterns. Which technique is the IDPS using?
A. Plug-in-based detection
B. Signature-based detection
C. Device-based detection
D. Anomaly-based detection
-
Question 22:
What term refers to the entry points from which an attack can be launched?
A. Work factor
B. Velocity of attack
C. Attack vector
D. Attack surface
-
Question 23:
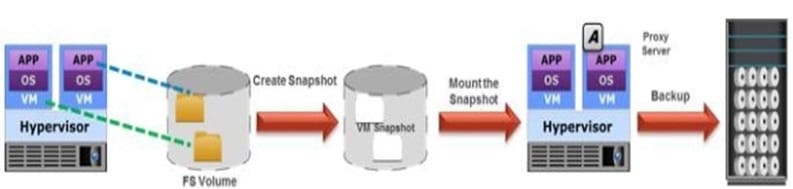
Which backup method type is represented in the exhibit?
A. Direct backup
B. Guest VM level backup
C. Image-level backup
D. Guest OS level backup
-
Question 24:
What is a function of business relationship management?
A. Determine if the capacity of IT services can deliver the agreed upon service levels
B. Identify requirements and ensure that the appropriate services are provided
C. Identify accurate information for all operational services
D. Determine what the sufficient capacity is to meet business demand
-
Question 25:
A new service has been created and the service instance is ready to use. What type of an alert is generated to notify the user about this event?
A. Instructional
B. Informational
C. Warning
D. Caution
-
Question 26:
What ensures that the cloud services and service creation processes adhere to relevant policies and legal requirements?
A. Problem management
B. Risk management
C. Audit management
D. Compliance management
-
Question 27:
What term refers to businesses that cautiously and gradually embrace digital transformation?
A. Digital Laggards
B. Digital Evaluators
C. Digital Leaders
D. Digital Adopters
-
Question 28:
A service is offered to consumers from 9 A.M. to 5 P.M., Monday through Friday. The service experiences downtime from 3 P.M. to 5 P.M. on Wednesday of a given week.
What is the service availability for that week?
A. 95.00%
B. 95.88%
C. 96.42%
D. 98.33%
-
Question 29:
Which activity is a part of people transformation?
A. Automation of IT tasks that reduces manpower needs
B. Adoption of a modern IT infrastructure
C. Communication between IT staff and business leaders
D. Adoption of a standard framework such as ITL
-
Question 30:
Which compliance standard provides policies and procedures to optimize the security of credit card transactions?
A. HIPAA
B. ENISA
C. CSA CCM
D. PCI DSS
Related Exams:
D-GAI-F-01
Dell GenAI Foundations AchievementD-MSS-DS-23
Dell Midrange Storage Solutions Design 2023D-OME-OE-A-24
Dell OpenManage Operate AchievementD-PDD-DY-23
Dell PowerProtect DD Deploy 2023D-PE-OE-23
Dell PowerEdge Operate 2023D-PEXE-IN-A-00
Dell PowerEdge XE9680 and XE8640 InstallD-PSC-MN-01
Dell GenAI Foundations AchievementD-PST-MN-A-24
Dell PowerStore Maintenance AchievementD-PWF-DS-23
Dell PowerFlex Design 2023D-RP-DY-A-24
Dell RecoverPoint Deploy Achievement
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EMC exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your DEA-2TT3 exam preparations and EMC certification application, do not hesitate to visit our Vcedump.com to find your solutions here.