Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Apr 13, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 221:
While auditing a web application for vulnerabilities, Donald uses Burp proxy and modifies the get requests
as below:
http://www.example.com/GET/process.php./../../../../../../../../etc/password
What is Donald trying to achieve?
A. Donald is modifying process.php file to extract /etc/password file
B. Donald is trying directory traversal to extract /etc/password file
C. Donald is trying SQL injection to extract the contents of /etc/password file
D. Donald is trying to upload /etc/password file to the web server root folder
-
Question 222:
Rock is a disgruntled employee of XYZ Inc. He wanted to take revenge. For that purpose, he created a malicious software that automatically visits every page on the company's website, checks pages for important links to other content recursively, and indexes them in a logical flow. By using this malicious software, he gathered a lot of crucial information that is required to exploit the organization. What is the type of software that Rock developed?
A. Web spider
B. Web fuzzer
C. Web scanner
D. Web proxy
-
Question 223:
An organization recently faced a cyberattack where an attacker captured legitimate user credentials and gained access to the critical information systems. He also led other malicious hackers in gaining access to the information systems. To defend and prevent such attacks in future, the organization has decided to route all the incoming and outgoing network traffic through a centralized access proxy apart from validating user credentials. Which of the following defensive mechanisms the organization is trying to strengthen?
A. Authentication
B. Serialization
C. Encryption
D. Hashing
-
Question 224:
Charles, a network penetration tester, is part of a team assessing the security of perimeter devices of an
organization. He is using the following Nmap command to bypass the firewall:
nmap -D 10.10.8.5, 192.168.168.9, 10.10.10.12
What Charles is trying to do?
A. Packet Fragmentation
B. Cloaking a scan with decoys
C. Spoofing source address
D. Spoofing source port number
-
Question 225:
You are working on a pen testing assignment. Your client has asked for a document that shows them the
detailed progress of the pen testing.
Which document is the client asking for?
A. Scope of work (SOW) document
B. Rule of engagement with signatures of both the parties
C. Project plan with work breakdown structure
D. Engagement log
-
Question 226:
Adam is a senior penetration tester at XYZsecurity Inc. He is auditing a wireless network for vulnerabilities.
Before starting the audit, he wants to ensure that the wireless card in his machine supports injection. He
decided to use the latest version of aircrack-ng tool.
Which of the following commands will help Adam check his wireless card for injection?
A. aireplay-ng -9 wlan0
B. airodump-ng wlan0
C. airdecap-ng -3 wlan0
D. aireplay-ng -5 –b wlan0
-
Question 227:
Smith, a pen tester, has been hired to analyze the security posture of an organization and is trying to find the operating systems used in the network using Wireshark. What can be inferred about selected packet in the Wireshark screenshot below?
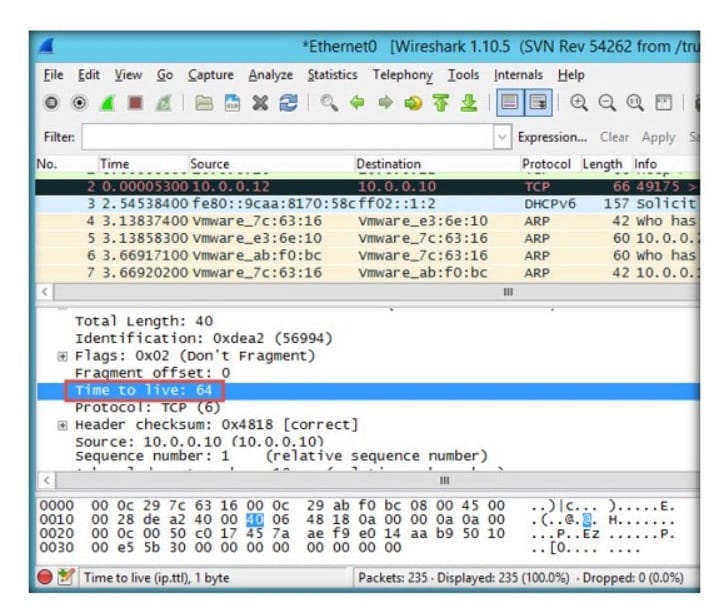
A. The machine with IP 10.0.0.10 is running on Linux
B. The machine with IP 10.0.0.12 is running on Linux
C. The machine with IP 10.0.0.12 is running on Windows
D. The machine with IP10.0.0.10 is running on Windows
-
Question 228:
Harry, a penetration tester in SqSac Solutions Ltd., is trying to check if his company's SQL server database is vulnerable. He also wants to check if there are any loopholes present that can enable the perpetrators to exploit and gain access to the user account login details from the database. After performing various test attempts, finally Harry executes an SQL query that enabled him to extract all the available Windows Login Account details. Which of the following SQL queries did Harry execute to obtain the information?
A. SELECT name FROM sys.server_principals WHERE TYPE = 'R'
B. SELECT name FROM sys.server_principals WHERE TYPE = 'U'
C. SELECT name FROM sys.server_principals WHERE TYPE = 'G'
D. SELECT name FROM sys.server_principals WHERE TYPE = 'S'
-
Question 229:
Analyze the ICMP packet below and mark the correct statement.
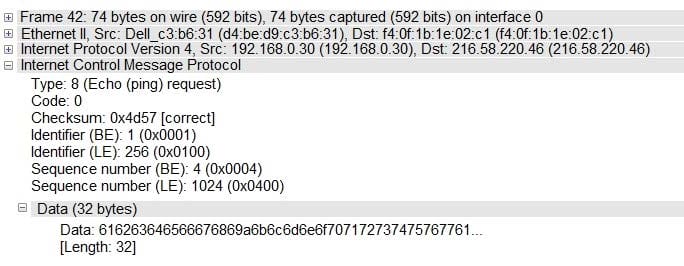
A. It is a ping packet that requires fragmentation, but the Don't Fragment flag is set
B. It is a ping request, but the destination port is unreachable
C. It is a ping response, when the destination host is unknown
D. It is a ping request, but the destination network is unreachable
-
Question 230:
Adam is working as a senior penetration tester at Eon Tech Services Ltd. The company asked him to
perform penetration testing on their database. The company informs Adam they use Microsoft SQL Server.
As a part of the penetration testing, Adam wants to know the complete information about the company's
database. He uses the Nmap tool to get the information.
Which of the following Nmap commands will Adam use to get the information?
A. nmap -p2051 --script ms-sql-info
B. nmap -p1801 --script ms-sql-info
C. nmap -p1443 --script ms-sql-info
D. nmap -p1521 --script ms-sql-info
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.