Exam Details
Exam Code
:ECSAV10Exam Name
:EC-Council Certified Security Analyst (ECSA) v10Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:354 Q&AsLast Updated
:Mar 24, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAV10 Questions & Answers
-
Question 341:
Identify the PRGA from the following screenshot: A. replay_src-0124-161120.cap
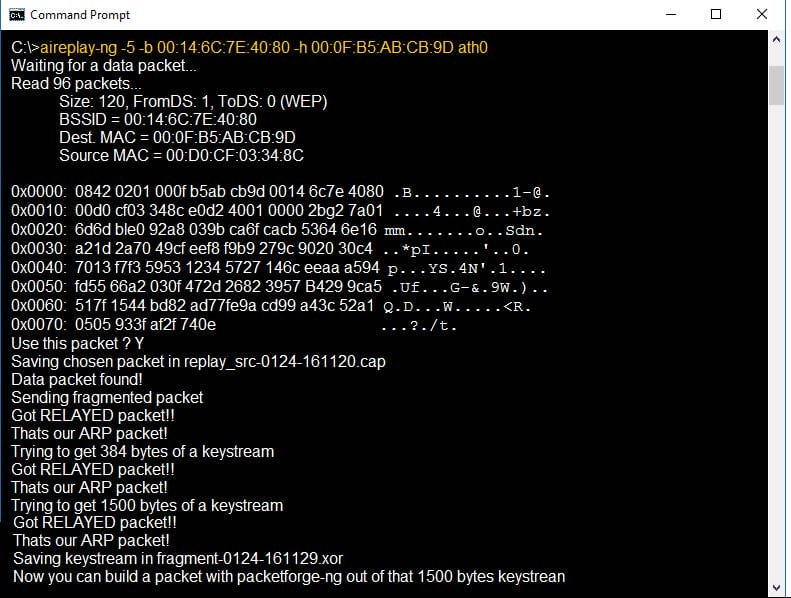
B. fragment-0124-161129.xor
C. 0505 933f af2f 740e
D. 0842 0201 000f b5ab cd9d 0014 6c7e 4080
-
Question 342:
Richard, a penetration tester was asked to assess a web application. During the assessment, he discovered a file upload field where users can upload their profile pictures. While scanning the page for vulnerabilities, Richard found a file upload exploit on the website. Richard wants to test the web application by uploading a malicious PHP shell, but the web page denied the file upload. Trying to get around the security, Richard added the `jpg' extension to the end of the file. The new file name ended with `.php.jpg'. He then used the Burp suite tool and removed the `jpg'' extension from the request while uploading the file. This enabled him to successfully upload the PHP shell.
Which of the following techniques has Richard implemented to upload the PHP shell?
A. Session stealing
B. Cookie tampering
C. Cross site scripting
D. Parameter tampering
-
Question 343:
Sandra, a wireless network auditor, discovered her client is using WEP. To prove the point that the WEP
encryption is very weak, she wants to decrypt some WEP packets. She successfully captured the WEP
data packets, but could not reach the content as the data is encrypted.
Which of the following will help Sandra decrypt the data packets without knowing the key?
A. Fragmentation Attack
B. Chopchop Attack
C. ARP Poisoning Attack
D. Packet injection Attack
-
Question 344:
Peter, a disgruntled ex-employee of Zapmaky Solutions Ltd., is trying to jeopardize the company's website http://zapmaky.com. He conducted the port scan of the website by using the Nmap tool to extract the information about open ports and their corresponding services. While performing the scan, he recognized that some of his requests are being blocked by the firewall deployed by the IT personnel of Zapmaky and he wants to bypass the same. For evading the firewall, he wanted to employ the stealth scanning technique which is an incomplete TCP three-way handshake method that can effectively bypass the firewall rules and logging mechanisms. Which if the following Nmap commands should Peter execute to perform stealth scanning?
A. nmap -sT -v zapmaky.com
B. nmap -T4 -A -v zapmaky.com
C. nmap -sX -T4 -A -v zapmaky.com
D. nmap -sN -A zapmaky.com
-
Question 345:
Joseph, a penetration tester, was hired by Xsecurity Services. Joseph was asked to perform a pen test on
a client's network. He was not provided with any information about the client organization except the
company name.
Identify the type of testing Joseph is going to perform for the client organization?
A. White-box Penetration Testing
B. Black-box Penetration Testing
C. Announced Testing
D. Grey-box Penetration Testing
-
Question 346:
An organization deployed Microsoft Azure cloud services for running their business activities. They appointed Jamie, a security analyst for performing cloud penetration testing. Microsoft prohibits certain tests to be carried out on their platform. Which of the following penetration testing activities Jamie cannot perform on the Microsoft Azure cloud service?
A. Post scanning
B. Denial-of-Service
C. Log monitoring
D. Load testing
-
Question 347:
Sam was asked to conduct penetration tests on one of the client's internal networks. As part of the testing
process, Sam performed enumeration to gain information about computers belonging to a domain, list of
shares on the individual hosts in the network, policies and passwords.
Identify the enumeration technique.
A. NTP Enumeration
B. NetBIOS Enumeration
C. DNS Enumeration
D. SMTP Enumeration
-
Question 348:
Jason is working on a pen testing assignment. He is sending customized ICMP packets to a host in the
target network. However, the ping requests to the target failed with "ICMP Time Exceeded Type = 11" error
messages.
What can Jason do to overcome this error?
A. Set a Fragment Offset
B. Increase the Window size in the packets
C. Increase the TTL value in the packets
D. Increase the ICMP header length
-
Question 349:
Thomas is an attacker and he skimmed through the HTML source code of an online shopping website for the presence of any vulnerabilities that he can exploit. He already knows that when a user makes any selection of items in the online shopping webpage, the selection is typically stored as form field values and sent to the application as an HTTP request (GET or POST) after clicking the Submit button. He also knows that some fields related to the selected items are modifiable by the user (like quantity, color, etc.) and some are not (like price). While skimming through the HTML code, he identified that the price field values of the items are present in the HTML code. He modified the price field values of certain items from $200 to $2 in the HTML code and submitted the request successfully to the application. Identify the type of attack performed by Thomas on the online shopping website?
A. Session poisoning attack
B. Hidden field manipulation attack
C. HTML embedding attack
D. XML external entity attack
-
Question 350:
Steven is performing a wireless network audit. As part of the engagement, he is trying to crack a WPAPSK key. Steven has captured enough packets to run aircrack-ng and discover the key, but aircrack-ng did
not yield any result, as there were no authentication packets in the capture.
Which of the following commands should Steven use to generate authentication packets?
A. aireplay-ng --deauth 11 -a AA:BB:CC:DD:EE:FF
B. airmon-ng start eth0
C. airodump-ng --write capture eth0
D. aircrack-ng.exe -a 2 -w capture.cap
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAV10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.