Exam Details
Exam Code
:ECSAv8Exam Name
:EC-Council Certified Security Analyst (ECSA) v8Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:200 Q&AsLast Updated
:Mar 22, 2025
EC-COUNCIL EC-COUNCIL Certifications ECSAv8 Questions & Answers
-
Question 51:
John, a penetration tester from a pen test firm, was asked to collect information about the host file in a Windows system directory. Which of the following is the location of the host file in Window system directory?
A. C:\Windows\System32\Boot
B. C:\WINNT\system32\drivers\etc
C. C:\WINDOWS\system32\cmd.exe
D. C:\Windows\System32\restore
-
Question 52:
Which among the following information is not furnished by the Rules of Engagement (ROE) document?
A. Techniques for data collection from systems upon termination of the test
B. Techniques for data exclusion from systems upon termination of the test
C. Details on how data should be transmitted during and after the test
D. Details on how organizational data is treated throughout and after the test
-
Question 53:
An attacker injects malicious query strings in user input fields to bypass web service authentication mechanisms and to access back-end databases. Which of the following attacks is this?
A. Frame Injection Attack
B. LDAP Injection Attack
C. XPath Injection Attack
D. SOAP Injection Attack
-
Question 54:
Identify the type of authentication mechanism represented below: A. NTLMv1
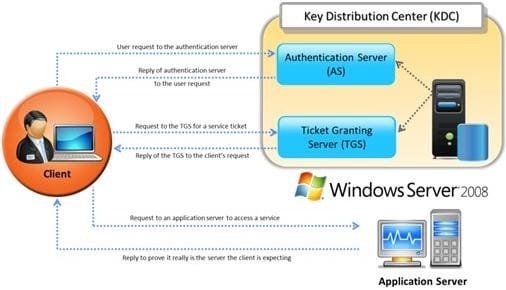
B. NTLMv2
C. LAN Manager Hash
D. Kerberos
-
Question 55:
Which of the following acts is a proprietary information security standard for organizations that handle cardholder information for the major debit, credit, prepaid, e-purse, ATM, and POS cards and applies to all entities involved in payment card processing?
A. PIPEDA
B. PCI DSS
C. Human Rights Act 1998
D. Data Protection Act 1998
-
Question 56:
The term social engineering is used to describe the various tricks used to fool people (employees, business partners, or customers) into voluntarily giving away information that would not normally be known to the general public.
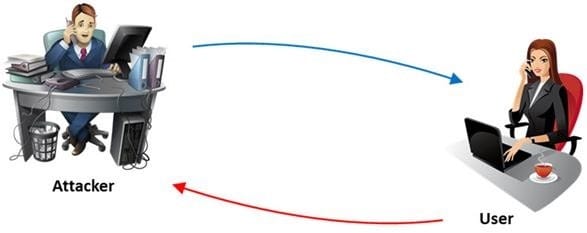
What is the criminal practice of social engineering where an attacker uses the telephone system in an attempt to scam the user into surrendering private information?
A. Phishing
B. Spoofing
C. Tapping
D. Vishing
-
Question 57:
Which of the following equipment could a pen tester use to perform shoulder surfing?
A. Binoculars
B. Painted ultraviolet material
C. Microphone
D. All the above
-
Question 58:
Which of the following password hashing algorithms is used in the NTLMv2 authentication mechanism?
A. AES
B. DES (ECB mode)
C. MD5
D. RC5
-
Question 59:
Identify the attack represented in the diagram below: A. Input Validation
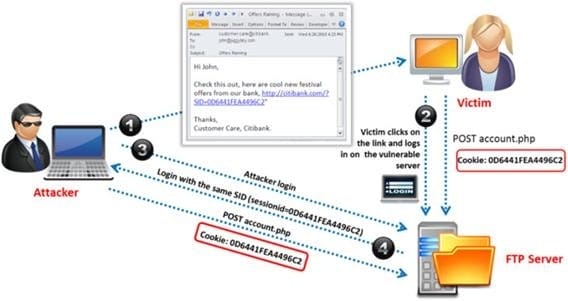
B. Session Hijacking
C. SQL Injection
D. Denial-of-Service
-
Question 60:
Which of the following is developed to address security concerns on time and reduce the misuse or threat of attacks in an organization?
A. Vulnerabilities checklists
B. Configuration checklists
C. Action Plan
D. Testing Plan
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your ECSAv8 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.