Exam Details
Exam Code
:JN0-334Exam Name
:Security, Specialist (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:90 Q&AsLast Updated
:Mar 27, 2025
Juniper Juniper Certifications JN0-334 Questions & Answers
-
Question 51:
What is the default timeout period for a TCP session in the session table of a Junos security device?
A. 1 minute
B. 60 minutes
C. 15 minutes
D. 30 minutes
-
Question 52:
After a software upgrade on an SRX5800 chassis cluster, you notice that both node0 and node1 are in the primary state, when node1 should be secondary. All control and fabric links are operating normally.
In this scenario, which step must you perform to recover the cluster?
A. Execute the request system rebootcommand on node1.
B. Execute the request system software rollbackcommand on node0.
C. Execute the request system software addcommand on node1.
D. Execute the request system rebootcommand on node0.
-
Question 53:
Click the Exhibit button.
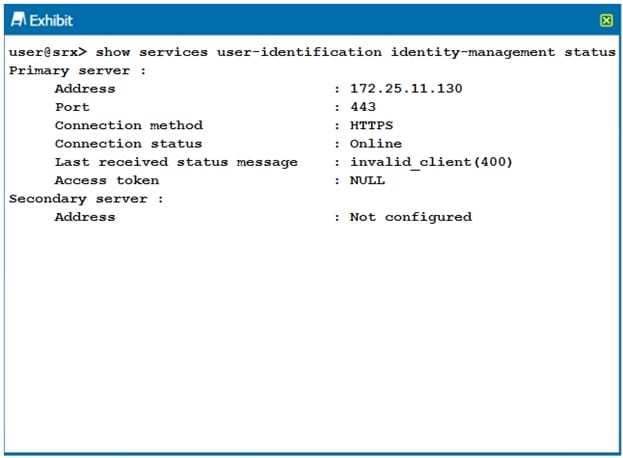
You have configured your SRX Series device to receive authentication information from a JIMS server. However, the SRX is not receiving any authentication information.
Referring to the exhibit, how would you solve the problem?
A. Use the JIMS Administrator user interface to add the SRX device as a client.
B. Generate an access token on the SRX device that matches the access token on the JIMS server.
C. Update the IP address of the JIMS server
D. Change the SRX configuration to connect to the JIMS server using HTTP.
-
Question 54:
What are two types of collectors for the JATP core engine? (Choose two.)
A. SNMP
B. e-mail
C. Web
D. telemetry
-
Question 55:
Your manager asks you to find employees that are watching YouTube during office hours. Which AppSecure component would you configure to accomplish this task?
A. AppQoE
B. AppFW
C. AppTrack
D. AppQoS
-
Question 56:
In an Active/Active chassis cluster deployment, which chassis cluster component is responsible for RG0 traffic?
A. the backup routing engine of the primary node
B. the master routing engine of the secondary node
C. the primary node
D. the secondary node
-
Question 57:
You are using the JIMS Administrator user interface to add multiple SRX client devices. You must share common configuration attributes across the SRX clients without having to re-enter those attributes for each SRX client instance.
Which JIMS Administrator feature would be used to accomplish this task?
A. JIMS automation
B. JIMS templates
C. JIMS client profiles
D. JIMS client defaults
-
Question 58:
Which two solutions provide a sandboxing feature for finding zero-day malware threats? (Choose two.)
A. Sky ATP
B. UTM
C. JATP
D. IPS
-
Question 59:
Click the Exhibit button.
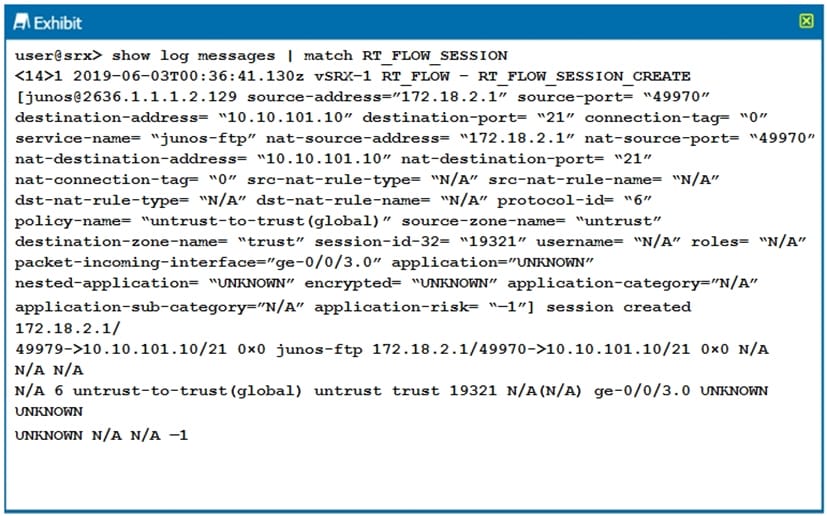
The output shown in the exhibit is displayed in which format?
A. syslog
B. WELF
C. binary
D. sd-syslog
-
Question 60:
You must configure JSA to accept events from an unsupported third-party log source. In this scenario, what should you do?
A. Separate event collection and flow collection on separate collectors.
B. Configure an RPM for a third-party device service module.
C. Configure JSA to silently discard unsupported log types.
D. Configure a universal device service module.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-334 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.