Exam Details
Exam Code
:JN0-334Exam Name
:Security, Specialist (JNCIS-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:90 Q&AsLast Updated
:Mar 27, 2025
Juniper Juniper Certifications JN0-334 Questions & Answers
-
Question 61:
What are two valid JIMS event log sources? (Choose two.)
A. Microsoft Windows Server 2012 audit logs
B. Microsoft Active Directory server event logs
C. Microsoft Exchange Server event logs
D. Microsoft Active Directory audit logs
-
Question 62:
What is the default session timeout value for ICMP and UDP traffic?
A. 30 seconds
B. 30 minutes
C. 60 seconds
D. 5 minutes
-
Question 63:
Which two statements describe application-layer gateways (ALGs)? (Choose two.)
A. ALGs are designed for specific protocols that require multiple sessions.
B. ALGs are used with protocols that use multiple ports.
C. ALGs can only be configured using Security Director.
D. ALGs are designed for specific protocols that use a single TCP session.
-
Question 64:
You are configuring a client-protection SSL proxy profile. Which statement is correct in this scenario?
A. A server certificate is not used but a root certificate authority is used.
B. A server certificate and root certificate authority are not used.
C. A server certificate is used but a root certificate authority is not used.
D. A server certificate and a root certificate authority are both used.
-
Question 65:
The AppQoE module of AppSecure provides which function?
A. The AppQoE module provides application-based routing.
B. The AppQoE module prioritizes important applications.
C. The AppQoE module provides routing, based on network conditions.
D. The AppQoE module blocks access to risky applications.
-
Question 66:
Which solution should you use if you want to detect known attacks using signature-based methods?
A. SSL proxy
B. JIMS
C. IPS
D. ALGs
-
Question 67:
Which feature supports sandboxing of zero-day attacks?
A. Sky ATP
B. SSL proxy
C. ALGs
D. high availability
-
Question 68:
Which two statements describe how rules are used with Juniper Secure Analytics? (Choose two.)
A. When a rule is triggered, JSA can respond by sending an e-mail to JSA administrators.
B. Rules are defined on Junos Space Security Director, and then pushed to JSA log collectors.
C. A rule defines matching criteria and actions that should be taken when an events matches the rule.
D. When a rule is triggered, JSA can respond by blocking all traffic from a specific source address.
-
Question 69:
Click the Exhibit button.
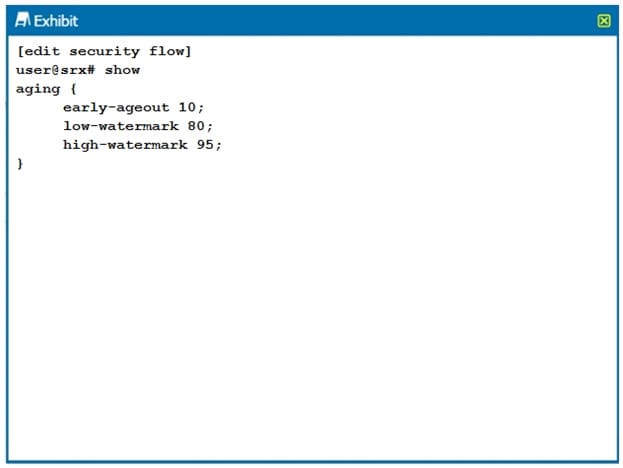
Which two statements are true about the configuration shown in the exhibit? (Choose two.)
A. The session is removed from the session table after 10 seconds of inactivity.
B. The session is removed from the session table after 10 milliseconds of inactivity.
C. Aggressive aging is triggered if the session table reaches 95% capacity.
D. Aggressive aging is triggered if the session table reaches 80% capacity.
-
Question 70:
You want to deploy vSRX in Amazon Web Services (AWS) virtual private clouds (VPCs). Which two statements are true in this scenario? (Choose two.)
A. The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Network Director instance.
B. MPLS LSPs can be used to connect vSRXs in different VPCs.
C. IPsec tunnels can be used to connect vSRX in different VPCs.
D. The vSRX devices serving as local enforcement points for VPCs can be managed by a centralized Junos Space Security Director instance.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-334 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.