Exam Details
Exam Code
:JN0-361Exam Name
:Service Provider Routing and Switching, Specialist (JNCIS-SP)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:542 Q&AsLast Updated
:Apr 15, 2025
Juniper Juniper Certifications JN0-361 Questions & Answers
-
Question 361:
Which configuration can be applied to ensure that no more than 600 MAC addresses are learned by a virtual switch?
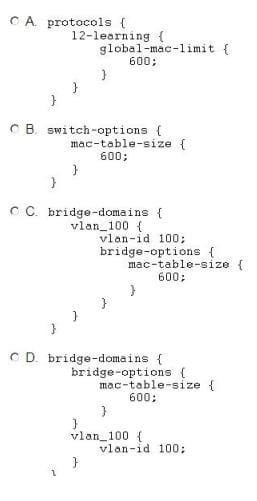
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 362:
Click the Exhibit button

You have two routers connected over a Gigabit Ethernet link as shown in the exhibit It is required that an IS-IS adjacency be established without the need for a designated intermediate system (DIS)
Which configuration statement entered on both routers will achieve this goal?
A. set interface ge-0/0/2 unit 0 family iso no-dis
B. set interface ge-0/0/2 unit 0 family iso point-to-point
C. set protocols isis interface ge-0/0/2.0 no-dis
D. set protocols isis interface ge-0/0/2.0 point-to-point
-
Question 363:
Click the Exhibit button
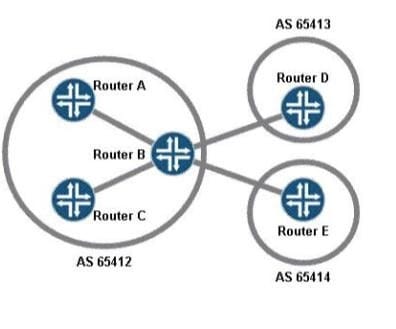
In the exhibit, all routers are sending routes to Router B
Which routes will be advertised from Router B to Router D?
A. BGP routes learned from Router A only
B. BGP routes learned from Router E only
C. BGP routes learned from Routers A and C only
D. BGP routes learned from Routers A, C and E only
-
Question 364:
Which two problems occur when increasing numbers of users are added to an Ethernet LAN with no switches present? (Choose two.)
A. There is a greater chance for collisions to occur
B. The MAC table sizes increase
C. Some devices will not see certain traffic
D. There is unnecessary consumption of network bandwidth
-
Question 365:
Click the Exhibit button
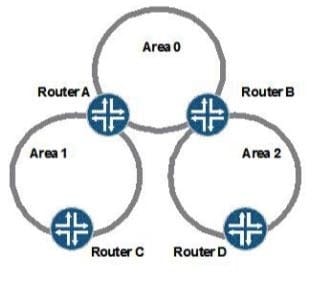
Given the OSPF network topology shown in the exhibit, you would like to inject external (non-OSPF) routes into the network on Router D.
Which two OSPF area types will support this configuration? (Choose two)
A. stub area
B. totally stubby area
C. not-so-stubby area
D. non-backbone area
-
Question 366:
You want to ensure that your RSVP LSPs are following a particular path across the network.
Which RSVP object ensures that your desire will be met?
A. explicit route object
B. record route object
C. session object
D. traffic specification object
-
Question 367:
Which statement is true about the operation of Layer 2 VPNs?
A. Layer 2 VPNs require that CE devices use the same Layer 2 encapsulation
B. Layer 2 VPNs do not permit CE devices to operate a Layer 3 protocol with each other
C. Service provider routers must evaluate the IP header of packets as they traverse their network
D. Layer 2 VPNs allow CEs to use different encapsulations on either side of the VPN
-
Question 368:
Click the Exhibit button
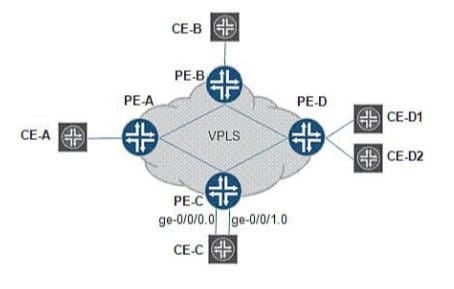
Based on the illustration shown in the exhibit, what would PE-B do with a VPLS packet received from PE-A if the matching entry in its VPLS routing table showed the destination was connected to PE-D?
A. PE-B would flood the packet to all attached PEs
B. PE-B would forward the packet to the root PE device
C. PE-B would forward the packet to all attached CE devices
D. PE-B would discard the packet
-
Question 369:
Click the Exhibit button
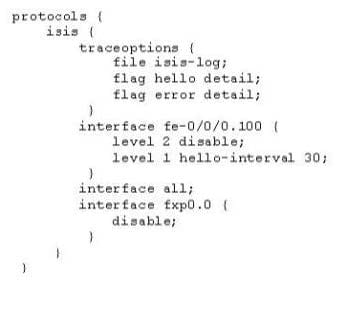
Based on the configuration shown in the exhibit, which command would you use to display real-time hellos and errors for IS-IS?
A. monitor file isis-log
B. monitor start isis-log
C. monitor log isis-log
D. monitor syslog isis-log
-
Question 370:
An Ethernet bridge is configured such that all interfaces are in a single broadcast domain, by default. Which two tasks does the bridge perform in response to receiving a multicast frame? (Choose two)
A. It learns the source MAC address
B. It drops the frame
C. It floods the frame out of all interfaces except the one on which it was received
D. It floods the frame out of particular interfaces based on its multicast MAC table
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)JN0-1361
Service Provider Design Specialist (JNCDS-SP)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JN0-361 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.