Exam Details
Exam Code
:MD-100Exam Name
:Windows ClientCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:409 Q&AsLast Updated
:Mar 30, 2025
Microsoft Microsoft Certifications MD-100 Questions & Answers
-
Question 381:
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while
others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
A user named User1 has a computer named Computer1 that runs Windows 10. Computer1 is joined to an Azure Active Directory (Azure AD) tenant named contoso.com. User1 joins Computer1 to contoso.com by using [email protected].
Computer1 contains a folder named Folder1. Folder1 is in drive C and is shared as Share1. Share1 has the permission shown in the following table.
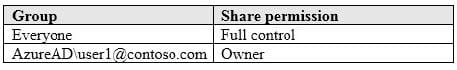
A user named User2 has a computer named Computer2 that runs Windows 10. User2 joins Computer2 to contoso.com by using [email protected].
User2 attempts to access Share1 and receives the following error message: "The username or password is incorrect."
You need to ensure that User2 can connect to Share1.
Solution: In Azure AD, you create a group named Group1 that contains User1 and User2.
You grant Group1 Change access to Share1.
Does this meet the goal?
A. Yes
B. No
-
Question 382:
You are preparing to deploy Windows 10.
You download and install the Windows Assessment and Deployment Kit (Windows ADK).
You need to create a bootable WinPE USB drive.
What should you do first?
A. Run the MakeWinPEMedia command.
B. Download and install Windows Configuration Designer.
C. Run the WPEUcil command.
D. Download and install the WinPE add-on.
-
Question 383:
You have a computer named Computer1 that runs Windows 10.
Computer1 has a folder named C:\Folder1.
You need to meet the following requirements:
1.
Log users that access C:\Folder1.
2.
Log users that modify and delete files in C:\Folder1. Which two actions should you perform?
A. From the properties of C:\Folder1, configure the Auditing settings.
B. From the properties of C:\Folder1, select the Encryption contents to secure data option.
C. From the Audit Policy in the local Group Policy, configure Audit directory service access.
D. From the Audit Policy in the local Group Policy, you configure Audit object access.
E. From the Audit Policy in the local Group Policy, you configure Audit system events.
-
Question 384:
You are troubleshooting an issue that prevents you from installing Windows 10 updates.
You discover that the issue relates to corrupt protected system files.
You need to restore the corrupt system files.
Which command should you run?
A. scanscace
B. sfc
C. chlcdslc
D. chkncfs
-
Question 385:
Your network contains an Active Directory domain. All users have been issued with computers that run Windows 8.1.
A user named Mia Hamm has a computer named Computer1. You upgrade Computer1 to Windows 10 by performing a clean installation of Windows 10 without formatting the drives.
You need to migrate the settings for Mia Hamm from Windows 8.1 to Windows 10.
Which two actions should you perform?
NOTE: Each correct selection is worth one point.
A. Run scanstate.exe and specify the C:\Users folder
B. Run loadstate.exe and specify the C:\Windows.old folder
C. Run usmultils.exe and specify the C:\Users folder
D. Run scanstate.exe and specify the C:\Windows.old folder
E. Run loadstate.exe and specify the C:\Users folder
F. Run usmultils.exe and specify the C:\Windows.old folder
-
Question 386:
You have a computer named Computer! that runs Windows 11.
You need to ensure that when Computer 1 is low on disk space, the computer automatically cleans up temporary files and empties the Recycle Bin.
What should you use?
A. Optimize Drives
B. Disk Cleanup
C. Storage Sense
D. Storage Spaces
-
Question 387:
Which users can sign in to Computer3 when the computer starts in Safe Mode?
A. User31 only
B. User31 and User32 only
C. User31 and Admin1 only
D. User31, User 32, User33, and Admin1
E. User31, User32, and User33 only
-
Question 388:
You need to ensure that you can manage Computer2 by using Windows Admin Center on Server1. What should you do on Computer2?
A. Install the Remote Server Administration Tool (RSAT) optional features.
B. Run the winrm quickconfigcommand.
C. Set the Windows Management Service Startup type to Automatic and start the service.
D. Run the Set-Locationcmdlet.
-
Question 389:
On Computer1, you need to configure the custom Visual Effects performance settings. Which user accounts can you use?
A. Admin1, User11, and User13 only
B. Admin1 only
C. Admin1, User11, User12, and User13
D. Admin1, User11, and User12 only
E. Admin1 and User 11 only
-
Question 390:
You need to ensure that you can manage Computer2 by using Windows Admin Center on Server1. What should you do on Computer2?
A. Allow the Windows Device Management feature through Windows Defender Firewall.
B. Run the winrm quickconfigcommand.
C. Allow the Windows Remote Management (WinRM) feature through Windows Defender Firewall.
D. Set the Windows Management Service Startup type to Automatic and start the service.
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-100 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.