Exam Details
Exam Code
:MS-101Exam Name
:Microsoft 365 Mobility and SecurityCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:525 Q&AsLast Updated
:Mar 25, 2025
Microsoft Microsoft Certifications MS-101 Questions & Answers
-
Question 21:
You have a Microsoft 365 E5 subscription that contains the groups shown in the following table.
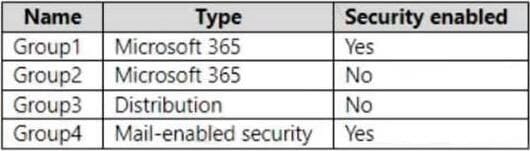
You create a Policies for Office apps configuration named Policy1.
You need to deploy Policy1.
To which groups can you deploy the configuration?
A. Group3 only
B. Group4 only
C. Group1 and Group2 only
D. Group1 and Group4 only
E. Group1, Group2, Group3, and Group4
-
Question 22:
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365 and contains a mailbox name Mailbox1.
You plan to use Mailbox 1 to collect and analyze unfiltered email messages.
You need to ensure that Defender for Office 365 takes no action on any inbound emails delivered to Mailbox1.
What should you do?
A. Create a mail flow.rule.
B. Configure a retention policy for Mailbox1.
C. Place a litigation hold on Mailbox1.
D. Configure Mailbox1 as a SecOps mailbox.
-
Question 23:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint.
You plan to perform device discovery and authenticated scans of network devices.
You install and register the network scanner on a device named Device1.
What should you do next?
A. Download and run an onboarding package.
B. Connect Defender for Endpoint to Microsoft Intune.
C. Apply for Microsoft Threat Experts – Targeted Attack Notifications.
D. Create an assessment job.
-
Question 24:
You have a Microsoft 365 E5 subscription that contains the devices shown in the following table.
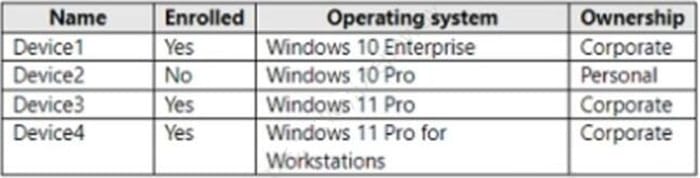
You need to implement Windows Information Protection (WIP). The solution must meet the following requirements:
Ensure that users on enrolled devices can override the WIP policy settings. Prevent users on unenrolled devices from overriding the WIP policy settings. What is the minimum number of app protection policies required?
A. 1
B. 2
C. 3
D. 4
-
Question 25:
You have a Microsoft SharePoint Online site named Site1.
On March 1, you delete a document named Document1.docx from Site1.
On April 1, you empty the Recycle Bin of Site1.
You need to identify the latest date a user who has the SharePoint admin role can recover Document1.docx.
Which date should you identify?
A. April 1
B. May 1
C. June 1
D. September 1
E. December 1
-
Question 26:
You have a new Microsoft 365 E5 tenant.
You need to enable an alert policy that will be triggered when an elevation of Microsoft Exchange Online administrative privileges is detected.
What should you do first?
A. Enable Microsoft 365 usage analytics.
B. Create a communication compliance policy.
C. Enable auditing.
D. Create an Insider risk management policy.
-
Question 27:
You have a Microsoft 365 subscription that contains 500 Windows 11 devices enrolled in Microsoft Intune.
You deploy a new Win32 app named App1 to all the devices and verify that users can install App1 manually by using the Company Portal app.
You need to configure App1 to ensure that all future deployments of the app install automatically without user intervention. The solution must minimize administrative effort.
What should you do?
A. Modify the detection rules for App1.
B. Delete App1, and then redeploy App1.
C. Modify the assignments for App1.
D. Modify the install command for App1.
-
Question 28:
From the Microsoft 365 compliance center, you create a content export as shown in the exhibit. (Click the Exhibit tab.)
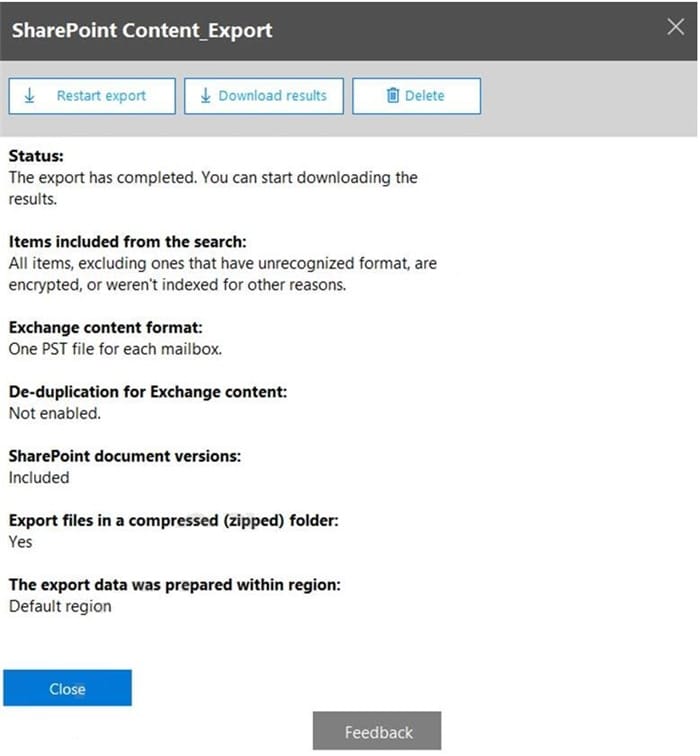
What will be excluded from the export?
A. a 75-MB PDF file
B. a 5-KB RTF file
C. an 80-MB PPTX file
D. a 12-MB BMP file
-
Question 29:
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
You need to ensure that users are prevented from opening or downloading malicious files from Microsoft Teams, OneDrive, or SharePoint Online.
What should you do?
A. Configure the Safe Links global settings.
B. Create a new Anti-malware policy.
C. Configure the Safe Attachments global settings.
D. Create a new Anti-phishing policy.
-
Question 30:
You have a Microsoft 365 E5 subscription.
You need to ensure that administrators receive an email when Microsoft 365 Defender detects a sign-in from a risky IP address.
What should you create?
A. an incident assignment filter
B. a vulnerability notification rule
C. an incident notification rule
D. an alert
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.