Exam Details
Exam Code
:MS-101Exam Name
:Microsoft 365 Mobility and SecurityCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:525 Q&AsLast Updated
:Mar 25, 2025
Microsoft Microsoft Certifications MS-101 Questions & Answers
-
Question 31:
You plan to use Microsoft Sentinel and Microsoft Defender for Cloud Apps.
You need to connect Microsoft Defender for Cloud Apps to Microsoft Sentinel.
What should you do in the Microsoft Defender for Cloud Apps portal?
A. From Automatic log upload, add a data source.
B. From Automatic log upload, add a log collector.
C. From Connected apps, add an app connector.
D. From Security extensions, add a SIEM agent.
-
Question 32:
You have a Microsoft 365 E5 subscription.
You plan to deploy Microsoft Defender for Cloud Apps.
You need to ensure that Microsoft Defender for Cloud Apps can differentiate between internal and external users.
What should you do?
A. From the Microsoft 365 admin center, configure the Org settings.
B. From the Microsoft 365 admin center, configure the default domain.
C. From the Microsoft Defender for Cloud Apps portal, add a list of managed domains.
D. From the Microsoft Defender for Cloud Apps portal, configure the Organization details.
-
Question 33:
You have a Microsoft 365 E5 subscription.
You need to be alerted when Microsoft 365 Defender detects high-severity incidents.
What should you use?
A. a threat policy
B. a custom detection rule
C. an alert policy
D. a notification rule
-
Question 34:
You have a Microsoft 365 tenant.
You plan to implement Endpoint Protection device configuration profiles.
Which platform can you manage by using the profiles?
A. Android
B. Android Enterprise
C. CentOS Linux
D. macOS
-
Question 35:
You have a Microsoft 365 subscription that uses Microsoft Defender for Office 365.
A Built-in protection preset security policy is applied to the subscription.
Which two policy types will be applied by the Built-in protection policy? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
A. Safe Links
B. Anti-malware
C. Anti-phishing
D. Anti-spam
E. Safe Attachments
-
Question 36:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Office 365.
You have the policies shown in the following table.
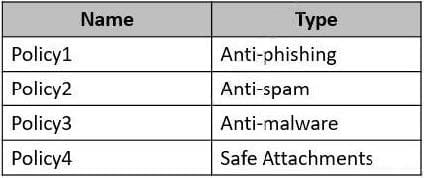
All the policies are configured to send malicious email messages to quarantine. Which policies support a customized quarantine retention period?
A. Policy1 and Policy3 only
B. Policy2 and Policy4 only
C. Policy1 and Policy2 only
D. Policy3 and Policy4 only
-
Question 37:
You have a Microsoft 365 tenant.
You plan to manage incidents in the tenant by using the Microsoft 365 Defender.
Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
A. Azure Information Protection
B. Azure Arc
C. Microsoft Sentinel
D. Microsoft Defender for Identity
-
Question 38:
You have a Microsoft 365 E5 tenant.
You need to create a policy that will trigger an alert when unusual Microsoft Office 365 usage patterns are detected.
What should you use to create the policy?
A. the Microsoft 365 admin center
B. the Microsoft 365 compliance center
C. the Microsoft Defender for Cloud Apps portal
D. the Microsoft Apps admin center
-
Question 39:
You have a Microsoft 365 E5 tenant that contains two groups named Group1 and Group2.
You need to prevent the members of Group1 from communicating with the members of Group2 by using Microsoft Teams. The solution must comply with regulatory requirements and must not affect other users in the tenant.
What should you use?
A. administrative units in Azure Active Directory (Azure AD)
B. information barriers
C. moderated distribution groups
D. communication compliance policies
-
Question 40:
You have a Microsoft 365 subscription.
You discover that some external users accessed content on a Microsoft SharePoint site. You modify the SharePoint sharing policy to prevent sharing outside your organization.
You need to be notified if the SharePoint sharing policy is modified in the future.
Solution: From Microsoft 365 Defender, you create a Threat policy.
Does this meet the goal?
A. Yes
B. No
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MS-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.