Exam Details
Exam Code
:N10-007Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1251 Q&AsLast Updated
:Mar 23, 2025
CompTIA CompTIA Certifications N10-007 Questions & Answers
-
Question 71:
A network administrator has noticed many systems on the network have traffic that is anomalous and may be part of a botnet. The administrator wants to implement an access control method that requires a computer to have antivirus software installed before being granted network access. Which of the following should the administrator deploy?
A. 802.1X
B. Captive portal
C. Port security
D. NAC
-
Question 72:
A company's server-naming convention is overly complicated. The systems administrator wants to change the naming convention to make it easier for users to remember which hosts they should log into. However, renaming servers is complicated and requires some downtime. Which of the following DNS record types would accomplish this goal without requiring servers to be renamed?
A. TXT
B. A
C. SRV
D. CNAME
-
Question 73:
A network technician is working on a way to set up a new branch office securely. The network manager confirms the company does not have any plans to expand to any other new sites and wants to implement the most cost-effective solution. Which of the following would be the BEST type of VPN to implement?
A. Client-to-site VPN
B. DMVPN
C. Site-to-site VPN
D. MPLS VPN
-
Question 74:
The network team at a university, which has on-campus residences, recently expanded the WiFi offerings to the dormitories. Each dormitory houses approximately 75 students, who each have multiple wireless devices. The WLAN utilizes an intelligent wireless controller for configuration and management. While the WiFi in academic buildings continues to receive few to no complaints, dormitory complaints are on the rise. Which of the following is MOST likely causing the complaints?
A. Frequency mismatch
B. Crosstalk
C. Interference
D. Channel overlap
-
Question 75:
A network technician is setting up a new web server on the company network. One of the requirements for the web server is to ensure the end users can securely authenticate to the application to perform their job duties. Which of the following ports should the network technician request from the firewall team to comply with this requirement?
A. 22
B. 69
C. 80
D. 389
E. 443
-
Question 76:
Company policy dictates that full backups are taken every Sunday evening, and incremental backups occur Monday through Saturday in the evening. If data loss were to occur on a Thursday before the backup window, which of the following is the number of backup sets that would be needed to retrieve the lost data come Friday morning?
A. 1
B. 2
C. 3
D. 4
E. 5
-
Question 77:
A network technician is performing an initial configuration of a new network switch. Per company policy, the only authorized manner for remotely administering the switch is through a command line. Which of the following protocols should the technician disable to adhere to the company policy?
A. HTTP
B. Telnet
C. SSH
D. TFTP
-
Question 78:
A network technician is troubleshooting a connectivity issue with Joe, a user. Joe has reported that when he attempts to RDP to machine1 (192.168.21.21) by name, he is connected to machine3 (192.168.21.23). When the network technician runs the command nslookup machine1, it returns the IP address 192.168.21.23; but when the ping –a 192.168.21.23 command is run, the results return the hostname machine3. Which of the following DNS records should be updated to allow RDP connections to machine1 by hostname?
A. A
B. SRV
C. PTR
D. TXT
-
Question 79:
A technician is trying to identify the cause of an issue several wireless users are experiencing at an office. The office is in a square-shaped building, with four 802.11b WAPs with omnidirectional antennas located in the four corners of the building. Users near the center of the building report sporadic issues connecting to resources. The technician checks the signal strength in the middle of the building and determines it is adequate. Which of the following is causing the reported issue?
A. The antenna types are incorrect, and unidirectional should be used.
B. MAC filtering has not been updated.
C. There is channel overlap of the access points.
D. The power levels are set too low on the WAPs.
-
Question 80:
A network administrator is reviewing the following output from a switch.
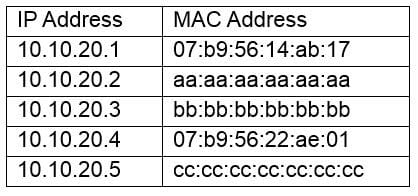
Which of the following attacks has occurred on the switch?
A. DNS poisoning
B. ARP poisoning
C. VLAN hopping
D. MAC address spoofing
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-007 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.