Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Apr 13, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 181:
A penetration tester is performing a social engineering penetration test and was able to create a remote session. Which of the following social engineering techniques was most likely successful?
A. SMS phishing
B. Dumpster diving
C. Executive impersonation attack
D. Browser exploitation framework
-
Question 182:
A penetration tester identified numerous flaws that could lead to unauthorized modification of critical data. Which of the following would be best for the penetration tester to recommend?
A. Flat access
B. Role-based access control
C. Permission-based access control
D. Group-based control model
-
Question 183:
During an assessment, a penetration tester obtains a list of password digests using Responder. Which of the following tools would the penetration tester most likely use next?
A. Hashcat
B. Hydra
C. CeWL
D. Medusa
-
Question 184:
A penetration tester performs the following command:
curl -l -http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
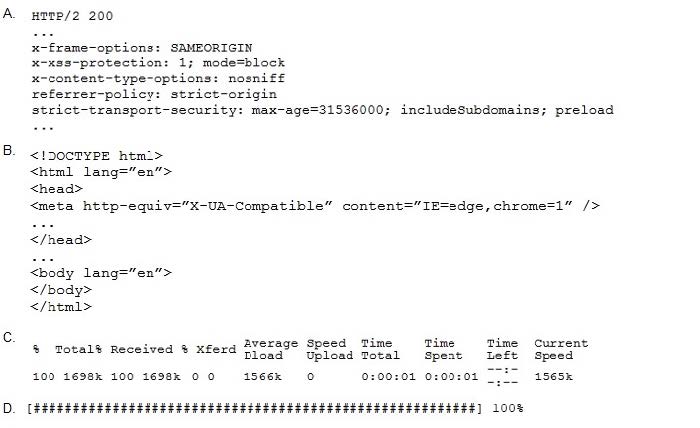
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 185:
The provision that defines the level of responsibility between the penetration tester and the client for preventing unauthorized disclosure is found in the:
A. NDA
B. SLA
C. MSA
D. SOW
-
Question 186:
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company's network. Which of the following accounts should the tester use to return the MOST results?
A. Root user
B. Local administrator
C. Service
D. Network administrator
-
Question 187:
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
A. Direct-to-origin
B. Cross-site scripting
C. Malware injection
D. Credential harvesting
-
Question 188:
A penetration tester wants to perform reconnaissance without being detected. Which of the following activities have a MINIMAL chance of detection? (Choose two.)
A. Open-source research
B. A ping sweep
C. Traffic sniffing
D. Port knocking
E. A vulnerability scan
F. An Nmap scan
-
Question 189:
After running the enum4linux.pl command, a penetration tester received the following output: Which of the following commands should the penetration tester run NEXT?

A. smbspool //192.160.100.56/print$
B. net rpc share -S 192.168.100.56 -U ''
C. smbget //192.168.100.56/web -U ''
D. smbclient //192.168.100.56/web -U '' -N
-
Question 190:
An Nmap scan shows open ports on web servers and databases. A penetration tester decides to run WPScan and SQLmap to identify vulnerabilities and additional information about those systems.
Which of the following is the penetration tester trying to accomplish?
A. Uncover potential criminal activity based on the evidence gathered.
B. Identify all the vulnerabilities in the environment.
C. Limit invasiveness based on scope.
D. Maintain confidentiality of the findings.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.