Exam Details
Exam Code
:PT0-002Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:455 Q&AsLast Updated
:Mar 28, 2025
CompTIA CompTIA Certifications PT0-002 Questions & Answers
-
Question 51:
Which of the following types of information should be included when writing the remediation section of a penetration test report to be viewed by the systems administrator and technical staff?
A. A quick description of the vulnerability and a high-level control to fix it
B. Information regarding the business impact if compromised
C. The executive summary and information regarding the testing company
D. The rules of engagement from the assessment
-
Question 52:
During a web application test, a penetration tester was able to navigate to https://company.com and view all links on the web page. After manually reviewing the pages, the tester used a web scanner to automate the search for vulnerabilities. When returning to the web application, the following message appeared in the browser:
unauthorized to view this page.
Which of the following BEST explains what occurred?
A. The SSL certificates were invalid.
B. The tester IP was blocked.
C. The scanner crashed the system.
D. The web page was not found.
-
Question 53:
A penetration tester has gained access to the Chief Executive Officer's (CEO's) internal, corporate email. The next objective is to gain access to the network. Which of the following methods will MOST likely work?
A. Try to obtain the private key used for S/MIME from the CEO's account.
B. Send an email from the CEO's account, requesting a new account.
C. Move laterally from the mail server to the domain controller.
D. Attempt to escalate privileges on the mail server to gain root access.
-
Question 54:
The following line-numbered Python code snippet is being used in reconnaissance:
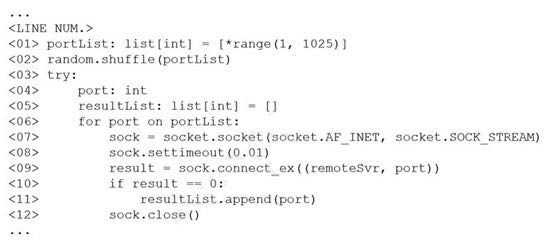
Which of the following line numbers from the script MOST likely contributed to the script triggering a "probable port scan" alert in the organization's IDS?
A. Line 01
B. Line 02
C. Line 07
D. Line 08
-
Question 55:
A penetration tester ran a ping -A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
A. Windows
B. Apple
C. Linux
D. Android
-
Question 56:
During the reconnaissance phase, a penetration tester obtains the following output: Reply from 192.168.1.23: bytes=32 time<54ms TTL=128 Reply from 192.168.1.23: bytes=32 time<53ms TTL=128 Reply from 192.168.1.23: bytes=32 time<60ms TTL=128 Reply from 192.168.1.23: bytes=32 time<51ms TTL=128 Which of the following operating systems is MOST likely installed on the host?
A. Linux
B. NetBSD
C. Windows
D. macOS
-
Question 57:
A security analyst needs to perform a scan for SMB port 445 over a/16 network. Which of the following commands would be the BEST option when stealth is not a concern and the task is time sensitive?
A. Nmap -s 445 -Pn -T5 172.21.0.0/16
B. Nmap -p 445 -n -T4 -open 172.21.0.0/16
C. Nmap -sV --script=smb* 172.21.0.0/16
D. Nmap -p 445 -max -sT 172. 21.0.0/16
-
Question 58:
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device. Which of the following tools would be BEST to use for this purpose?
A. Hashcat
B. Mimikatz
C. Patator
D. John the Ripper
-
Question 59:
Which of the following types of assessments MOST likely focuses on vulnerabilities with the objective to access specific data?
A. An unknown-environment assessment
B. A known-environment assessment
C. A red-team assessment
D. A compliance-based assessment
-
Question 60:
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
nmap -n -vv -sV -p- 10.10.10.23-28
ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
A. -su
B. -pn
C. -sn
D. -ss
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.