Exam Details
Exam Code
:PT0-003Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:271 Q&AsLast Updated
:Mar 21, 2025
CompTIA CompTIA Certifications PT0-003 Questions & Answers
-
Question 21:
A penetration tester attempted a DNS poisoning attack. After the attempt, no traffic was seen from the target machine. Which of the following MOST likely caused the attack to fail?
A. The injection was too slow.
B. The DNS information was incorrect.
C. The DNS cache was not refreshed.
D. The client did not receive a trusted response.
-
Question 22:
Which of the following tools would be BEST suited to perform a manual web application security assessment? (Choose two.)
A. OWASP ZAP
B. Nmap
C. Nessus
D. BeEF
E. Hydra
F. Burp Suite
-
Question 23:
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following:
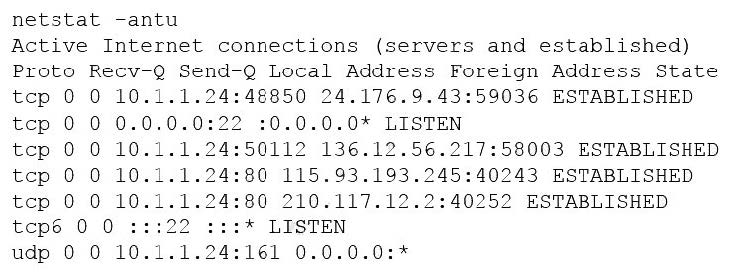
Which of the following should the penetration tester do NEXT?
A. Close the reverse shell the tester is using.
B. Note this finding for inclusion in the final report.
C. Investigate the high numbered port connections.
D. Contact the client immediately.
-
Question 24:
Which of the following can be used to store alphanumeric data that can be fed into scripts or programs as input to penetration-testing tools?
A. Dictionary
B. Directory
C. Symlink
D. Catalog
E. For-loop
-
Question 25:
A compliance-based penetration test is primarily concerned with:
A. obtaining Pll from the protected network.
B. bypassing protection on edge devices.
C. determining the efficacy of a specific set of security standards.
D. obtaining specific information from the protected network.
-
Question 26:
A penetration tester is assessing a wireless network. Although monitoring the correct channel and SSID, the tester is unable to capture a handshake between the clients and the AP. Which of the following attacks is the MOST effective to allow the penetration tester to capture a handshake?
A. Key reinstallation
B. Deauthentication
C. Evil twin
D. Replay
-
Question 27:
A penetration testing firm performs an assessment every six months for the same customer. While performing network scanning for the latest assessment, the penetration tester observes that several of the target hosts appear to be residential
connections associated with a major television and ISP in the area.
Which of the following is the most likely reason for the observation?
A. The penetration tester misconfigured the network scanner.
B. The network scanning tooling is not functioning properly.
C. The IP ranges changed ownership.
D. The network scanning activity is being blocked by a firewall.
-
Question 28:
Which of the following best explains why communication is a vital phase of a penetration test?
A. To discuss situational awareness
B. To build rapport with the emergency contact
C. To explain the data destruction process
D. To ensure the likelihood of future assessments
-
Question 29:
Which of the following tools can a penetration tester use to brute force a user password over SSH using multiple threads?
A. CeWL
B. John the Ripper
C. Hashcat
D. Hydra
-
Question 30:
A penetration tester was hired to test Wi-Fi equipment.
Which of the following tools should be used to gather information about the wireless network?
A. Kismet
B. Burp Suite
C. BeEF
D. WHOIS
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.