Exam Details
Exam Code
:PT0-003Exam Name
:CompTIA PenTest+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:272 Q&AsLast Updated
:Apr 02, 2025
CompTIA CompTIA Certifications PT0-003 Questions & Answers
-
Question 71:
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
A. MD5
B. bcrypt
C. SHA-1
D. PBKDF2
-
Question 72:
A penetration tester is conducting an unknown environment test and gathering additional information that can be used for later stages of an assessment. Which of the following would most likely produce useful information for additional testing?
A. Searching for code repositories associated with a developer who previously worked for the target company code repositories associated with the
B. Searching for code repositories target company's organization
C. Searching for code repositories associated with the target company's organization
D. Searching for code repositories associated with a developer who previously worked for the target company
-
Question 73:
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
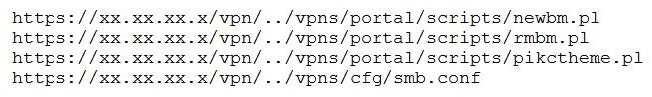
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A. Edit the discovered file with one line of code for remote callback
B. Download .pl files and look for usernames and passwords
C. Edit the smb.conf file and upload it to the server
D. Download the smb.conf file and look at configurations
-
Question 74:
During an assessment, a penetration tester was able to access the organization's wireless network from outside of the building using a laptop running Aircrack-ng. Which of the following should be recommended to the client to remediate this issue?
A. Changing to Wi-Fi equipment that supports strong encryption
B. Using directional antennae
C. Using WEP encryption
D. Disabling Wi-Fi
-
Question 75:
Which of the following should be included in scope documentation?
A. Service accounts
B. Tester experience
C. Disclaimer
D. Number of tests
-
Question 76:
A Chief Information Security Officer wants to evaluate the security of the company's e- commerce application.
Which of the following tools should a penetration tester use FIRST to obtain relevant information from the application without triggering alarms?
A. SQLmap
B. DirBuster
C. w3af
D. OWASP ZAP
-
Question 77:
The following line-numbered Python code snippet is being used in reconnaissance:
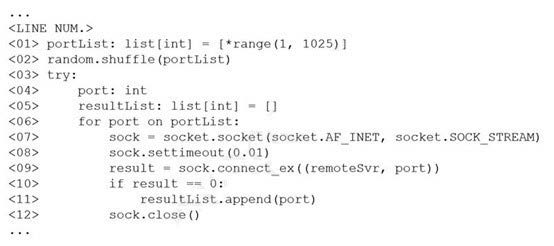
Which of the following line numbers from the script MOST likely contributed to the script triggering a "probable port scan" alert in the organization's IDS?
A. Line 01
B. Line 02
C. Line 07
D. Line 08
-
Question 78:
A company provided the following network scope for a penetration test: 169.137.1.0/24 221.10.1.0/24 149.14.1.0/24 A penetration tester discovered a remote command injection on IP address 149.14.1.24 and exploited the system. Later, the tester learned that this particular IP address belongs to a third party.
Which of the following stakeholders is responsible for this mistake?
A. The company that requested the penetration test
B. The penetration testing company
C. The target host's owner
D. The penetration tester
E. The subcontractor supporting the test
-
Question 79:
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
A. Halt the penetration test.
B. Contact law enforcement.
C. Deconflict with the penetration tester.
D. Assume the alert is from the penetration test.
-
Question 80:
During a vulnerability scanning phase, a penetration tester wants to execute an Nmap scan using custom NSE scripts stored in the following folder:
/home/user/scripts
Which of the following commands should the penetration tester use to perform this scan?
A. nmap resume "not intrusive"
B. nmap script default safe
C. nmap script /home/user/scripts
D. nmap -load /home/user/scripts
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT0-003 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.