Exam Details
Exam Code
:SC-200Exam Name
:Microsoft Security Operations AnalystCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:394 Q&AsLast Updated
:Mar 30, 2025
Microsoft Microsoft Certifications SC-200 Questions & Answers
-
Question 191:
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Microsoft Defender for Cloud and configure Defender for Cloud to use workspace1.
You need to collect security event logs from the Azure virtual machines that report to workspace1.
What should you do?
A. From Defender for Cloud, modify Microsoft Defender for Servers plan settings.
B. In sub1, register a provider.
C. From Defender for Cloud, create a workflow automation.
D. In workspace1, create a workbook.
-
Question 192:
You have an Azure subscription that contains a Microsoft Sentinel workspace named WS1 and 100 virtual machines that run Windows Server. You need to configure the collection of Windows Security event logs for ingestion to WS1. The solution must meet the following requirements:
1.
Capture a full user audit trail including user sign-in and user sign-out events.
2.
Minimize the volume of events.
3.
Minimize administrative effort. Which event set should you select?
A. Minimal
B. Common
C. All events
D. Custom
-
Question 193:
You have a Microsoft 365 E5 subscription that uses Microsoft Defender XDR and contains a user named User1.
You need to ensure that User1 can manage Microsoft Defender XDR custom detection rules and Endpoint security policies. The solution must follow the principle of least privilege.
Which role should you assign to User1?
A. Security Administrator
B. Security Operator
C. Cloud Device Administrator
D. Desktop Analytics Administrator
-
Question 194:
You have a Microsoft Sentinel workspace that contains a custom workbook named Workbook1.
You need to create a visual based on the SecurityEvent table. The solution must meet the following requirements:
1.
Identify the number of security events ingested during the past week.
2.
Display the count of events by day in a timechart. What should you add to Workbook1?
A. a query
B. a metric
C. a group
D. links or tabs
-
Question 195:
You have an Azure subscription.
You need to stream the Microsoft Graph activity logs to a third-party security information and event management (SIEM) tool. The solution must minimize administrative effort.
To where should you stream the logs?
A. an Azure Event Hubs namespace
B. an Azure Storage account
C. an Azure Event Grid namespace
D. a Log Analytics workspace
-
Question 196:
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint Plan 2 and contains 500 Windows devices. As part of an incident investigation, you identify the following suspected malware files:
1.
sys
2.
pdf
3.
docx
4.
xlsx
You need to create indicator hashes to block users from downloading the files to the devices.
Which files can you block by using the indicator hashes?
A. File1.sys only
B. File1.sys and File3.docx only
C. File1.sys, File3.docx, and File4.xlsx only
D. File2.pdf, File3.docx, and File4.xlsx only
E. File1.sys, File2.pdf, File3.docx, and File4.xlsx
-
Question 197:
You have a Microsoft 365 subscription that uses Microsoft Defender XDR.
You are investigating an attacker that is known to use the Microsoft Graph API as an attack vector. The attacker performs the tactics shown the following table.
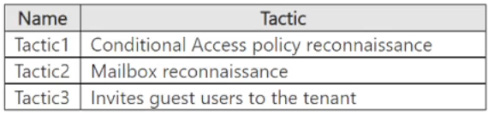
You need to search for malicious activities in your organization.
Which tactics can you analyze by using the MicrosoftGraphActivityLogs table?
A. Tactic1 only
B. Tactic2 only
C. Tactic1 and Tactic2 only
D. Tactic2 and Tactic3 only
E. Tactic1, Tactic2, and Tactic3
-
Question 198:
You have an Azure subscription that contains a user named User1 and a Microsoft Sentinel workspace named WS1. WS1 uses Microsoft Defender for Cloud. You have the Microsoft security analytics rules shown in the following table.
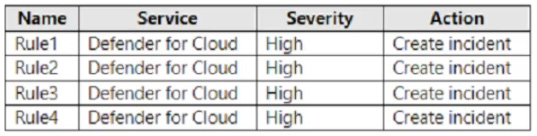
User1 performs an action that matches Rule1, Rule2, Rule3, and Rule4. How many incidents will be created in WS1?
A. 1
B. 2
C. 3
D. 4
-
Question 199:
You have a Microsoft 365 subscription that uses Microsoft Defender for Endpoint and contains a user named User1 and a Microsoft 365 group named Group1. All users are assigned a Defender for Endpoint Plan 1 license.
You enable Microsoft Defender XDR Unified role-based access control (RBAC) for Endpoints and Vulnerability Management.
You need to ensure that User1 can configure alerts that will send email notifications to Group1. The solution must follow the principle of least privilege.
Which permissions should you assign to User1?
A. Defender Vulnerability Management - Remediation handling
B. Alerts investigation
C. Live response capabilities: Basic
D. Manage security settings
-
Question 200:
You have a Microsoft 365 subscription that contains the following resources:
1.
100 users that are assigned a Microsoft 365 E5 license
2.
100 Windows 11 devices that are joined to the Microsoft Entra tenant
The users access their Microsoft Exchange Online mailbox by using Outlook on the web.
You need to ensure that if a user account is compromised, the Outlook on the web session token can be revoked. What should you configure?
A. security defaults in Microsoft Entra
B. Microsoft Entra Verified ID
C. a Conditional Access policy in Microsoft Entra
D. Microsoft Entra ID Protection
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-200 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.