Exam Details
Exam Code
:SC-200Exam Name
:Microsoft Security Operations AnalystCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:394 Q&AsLast Updated
:Mar 22, 2025
Microsoft Microsoft Certifications SC-200 Questions & Answers
-
Question 71:
HOTSPOT
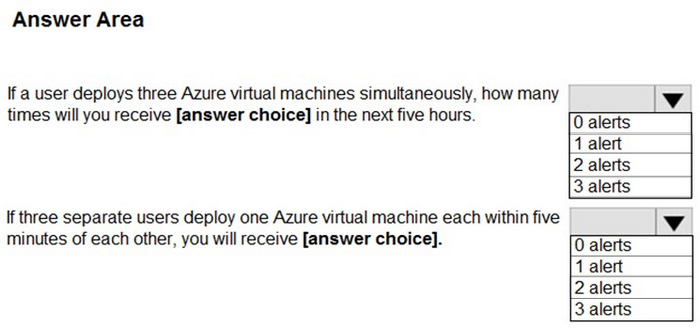
You use Azure Sentinel to monitor irregular Azure activity.
You create custom analytics rules to detect threats as shown in the following exhibit.
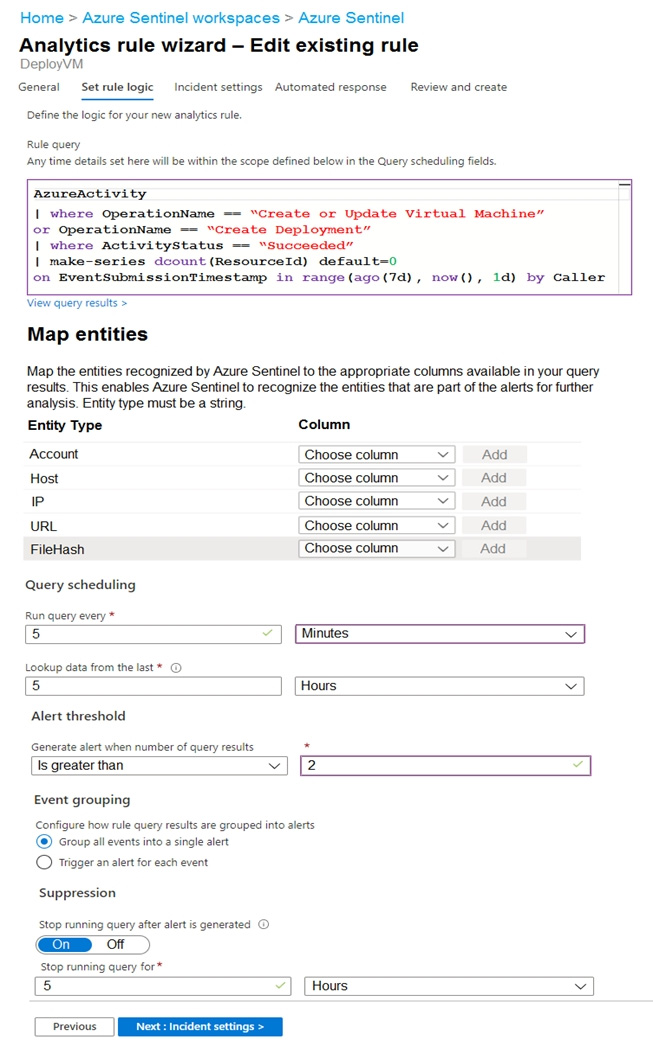
You do NOT define any incident settings as part of the rule definition.
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic.
NOTE: Each correct selection is worth one point.
Hot Area:
-
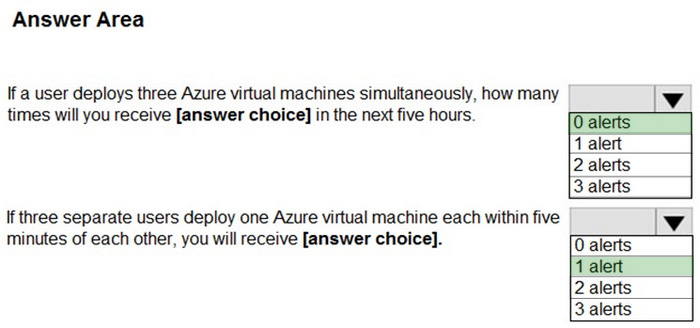
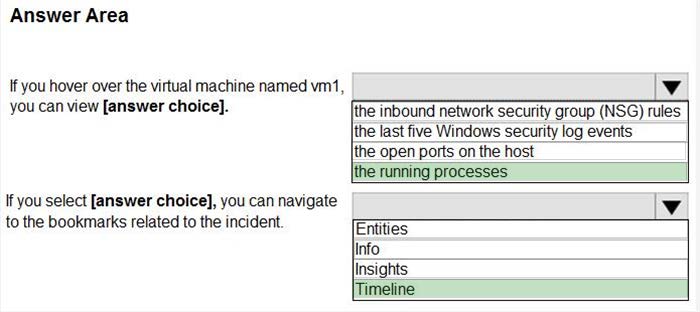
Question 72:
HOTSPOT
From Azure Sentinel, you open the Investigation pane for a high-severity incident as shown in the following exhibit.
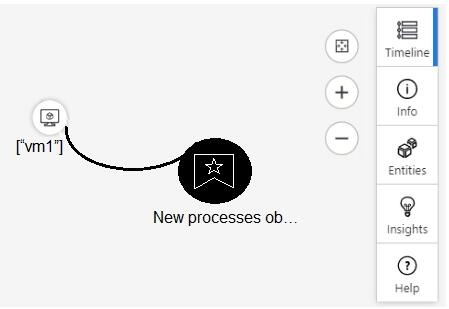
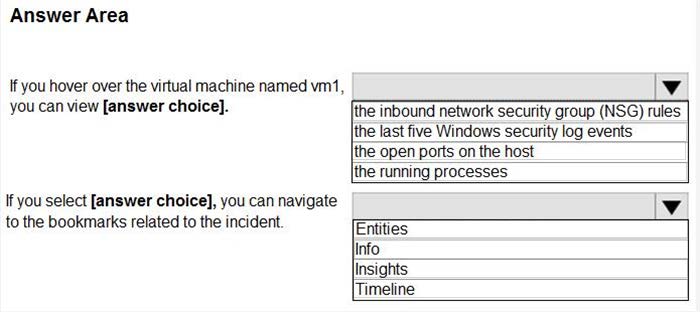
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
-
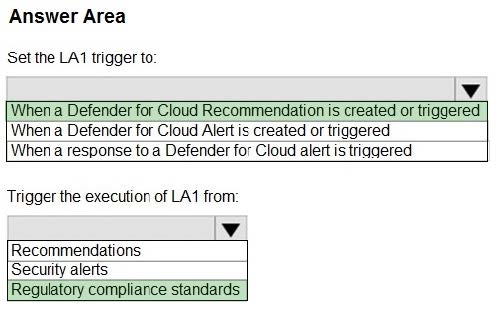
Question 73:
HOTSPOT
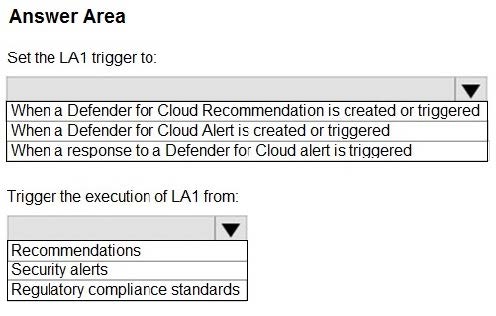
You have an Azure subscription that has Microsoft Defender for Cloud enabled for all supported resource types.
You create an Azure logic app named LA1.
You plan to use LA1 to automatically remediate security risks detected in Defender for Cloud.
You need to test LA1 in Defender for Cloud.
What should you do? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 74:
You create an Azure subscription.
You enable Azure Defender for the subscription.
You need to use Azure Defender to protect on-premises computers.
What should you do on the on-premises computers?
A. Install the Log Analytics agent.
B. Install the Dependency agent.
C. Configure the Hybrid Runbook Worker role.
D. Install the Connected Machine agent.
-
Question 75:
You have an Azure subscription named Sub1 and a Microsoft 365 subscription. Sub1 is linked to an Azure Active Directory (Azure AD) tenant named contoso.com.
You create an Azure Sentinel workspace named workspace1. In workspace1, you activate an Azure AD connector for contoso.com and an Office 365 connector for the Microsoft 365 subscription.
You need to use the Fusion rule to detect multi-staged attacks that include suspicious sign-ins to contoso.com followed by anomalous Microsoft Office 365 activity.
Which two actions should you perform? Each correct answer present part of the solution.
NOTE: Each correct selection is worth one point.
A. Create custom rule based on the Office 365 connector templates.
B. Create a Microsoft incident creation rule based on Azure Security Center.
C. Create a Microsoft Cloud App Security connector.
D. Create an Azure AD Identity Protection connector.
-
Question 76:
You create an Azure subscription named sub1.
In sub1, you create a Log Analytics workspace named workspace1.
You enable Azure Security Center and configure Security Center to use workspace1.
You need to collect security event logs from the Azure virtual machines that report to workspace1.
What should you do?
A. From Security Center, enable data collection
B. In sub1, register a provider.
C. From Security Center, create a Workflow automation.
D. In workspace1, create a workbook.
-
Question 77:
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You are configuring Azure Sentinel.
You need to create an incident in Azure Sentinel when a sign-in to an Azure virtual machine from a malicious IP address is detected.
Solution: You create a livestream from a query.
Does this meet the goal?
A. Yes
B. No
-
Question 78:
You use Azure Sentinel.
You need to use a built-in role to provide a security analyst with the ability to edit the queries of custom Azure Sentinel workbooks. The solution must use the principle of least privilege.
Which role should you assign to the analyst?
A. Azure Sentinel Contributor
B. Security Administrator
C. Azure Sentinel Responder
D. Logic App Contributor
-
Question 79:
You create a hunting query in Azure Sentinel.
You need to receive a notification in the Azure portal as soon as the hunting query detects a match on the query. The solution must minimize effort.
What should you use?
A. a playbook
B. a notebook
C. a livestream
D. a bookmark
-
Question 80:
A user wants to sign in from a location which has never been used by the other users in your organization. Which anomaly detection policy will you use if you need to receive a security alert ?
A. Activity from infrequent country
B. Activity from anonymous IP addresses
C. Impossible travel
D. Malware detection
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-200 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.