Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:718 Q&AsLast Updated
:Apr 11, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
Question 151:
A network administrator is working on a project to deploy a load balancer in the company's cloud environment. Which of the following fundamental security requirements does this project fulfil?
A. Privacy
B. Integrity
C. Confidentiality
D. Availability
-
Question 152:
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
A. ARO
B. RTO
C. RPO
D. ALE
E. SLE
-
Question 153:
In order to strengthen a password and prevent a hacker from cracking it, a random string of 36 characters was added to the password. Which of the following best describes this technique?
A. Key stretching
B. Tokenization
C. Data masking
D. Salting
-
Question 154:
A technician is deploying a new security camera. Which of the following should the technician do?
A. Configure the correct VLAN.
B. Perform a vulnerability scan.
C. Disable unnecessary ports.
D. Conduct a site survey.
-
Question 155:
A company is experiencing a web services outage on the public network. The services are up and available but inaccessible. The network logs show a sudden increase in network traffic that is causing the outage. Which of the following attacks is the organization experiencing?
A. ARP poisoning
B. Brute force
C. Buffer overflow
D. DDoS
-
Question 156:
Which of the following threat actors is the most likely to be motivated by profit?
A. Hacktivist
B. Insider threat
C. Organized crime
D. Shadow IT
-
Question 157:
An organization experiences a cybersecurity incident involving a command-and-control server. Which of the following logs should be analyzed to identify the impacted host? (Choose two.)
A. Application
B. Authentication
C. DHCP
D. Network
E. Firewall
F. Database
-
Question 158:
During a penetration test, a vendor attempts to enter an unauthorized area using an access badge. Which of the following types of tests does this represent?
A. Defensive
B. Passive
C. Offensive
D. Physical
-
Question 159:
A threat actor was able to use a username and password to log in to a stolen company mobile device. Which of the following provides the best solution to increase mobile data security on all employees' company mobile devices?
A. Application management
B. Full disk encryption
C. Remote wipe
D. Containerization
-
Question 160:
A systems administrator is advised that an external web server is not functioning property. The administrator reviews the following firewall logs containing traffic going to the web server:
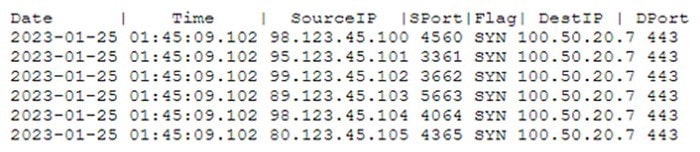
Which of the following attacks is likely occurring?
A. DDoS
B. Directory traversal
C. Brute-force
D. HTTPS downgrade
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.