Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:718 Q&AsLast Updated
:Apr 11, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
Question 171:
An organization recently experienced the following social engineering attacks that introduced malware into the network:
1.
In the first attack, the sender impersonated a staff member in the legal department and sent an email stating that the employee needed to click a link to sign an NDA in order to remain employed. The link provided was to a malicious website.
2.
In the second attack, the sender impersonated the director of finance and instructed the accounts payable department to pay an outstanding invoice. The attached invoice contained malware.
Which of the following is the most likely reason these attacks were successful?
A. Both attacks passed the spam filters, which resulted in the end users thinking the emails were legitimate.
B. Both attacks concealed the delivery of malware, which led end users to trust the emails.
C. Both attacks appealed to authority, which made the end users feel obligated to perform the requested actions.
D. Both attacks relied on dumpster diving to obtain a list of valid contacts to receive the malicious emails.
-
Question 172:
Which of the following security program audits includes a comprehensive evaluation of the security controls in place at an organization over a six- to 12-month time period?
A. NIST CSF
B. SOC 2 Type II
C. ISO 27001
D. PCI DSS
-
Question 173:
Development team members set up multiple application environments so they can develop, test, and deploy code in a secure and reliable manner. One of the environments is configured with real data that has been obfuscated so the team can adequately assess how the code will work in production. Which of the following environments is set up?
A. Quality assurance
B. Development
C. Sandbox
D. Production
-
Question 174:
Which of the following provides guidelines for the management and reduction of information security risk?
A. CIS
B. NIST CSF
C. ISO
D. PCI DSS
-
Question 175:
A security analyst is reviewing a secure website that is generating TLS certificate errors. The analyst determines that the browser is unable to receive a response from the OCSP for the certificate. Which of the following actions would most likely resolve the issue?
A. Run a traceroute on the OCSP domain to find where the domain is failing.
B. Create an exclusion for the OCSP domain in the content filter
C. Unblock the OCSP protocol in the host-based firewall
D. Add the root certificate to the trusted sites on the workstation with the issue.
-
Question 176:
During a wireless network scan at a data center the IT security team discovered Wi-Fi signals broadcasting from an unknown device. Which of the following best describes the cause of the incident?
A. Domain hijacking
B. On-path attack
C. Rogue access point
D. Jamming
-
Question 177:
An organization plans to take online orders via a new website. Three web servers are available for this website. However, the organization does not want to reveal the network addresses or quantity of the individual servers to the general public. Which of the following would best fulfill these requirements?
A. IPSec
B. Explicit proxy
C. Port security
D. Virtual IP
-
Question 178:
A security administrator recently reset local passwords and the following values were recorded in the system:
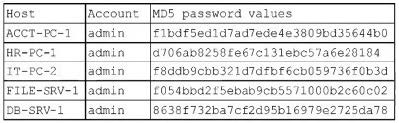
Which of the following is the security administrator most likely protecting against?
A. Account sharing
B. Weak password complexity
C. Pass-the-hash attacks
D. Password compromise
-
Question 179:
Which of the following security controls is used to isolate a section of the network and its externally available resources from the internal corporate network in order to reduce the number of possible attacks?
A. Faraday cages
B. Air gap
C. Vaulting
D. Proximity readers
-
Question 180:
A security analyst is responding to a malware incident at a company. The malware connects to a command-and-control server on the internet in order to function. Which of the following should the security analyst implement first?
A. Network segmentation
B. IP-based firewall rules
C. Mobile device management
D. Content filler
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.