Exam Details
Exam Code
:SY0-701Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:718 Q&AsLast Updated
:Apr 11, 2025
CompTIA CompTIA Certifications SY0-701 Questions & Answers
-
Question 181:
An accounting intern receives an invoice via email from the Chief Executive Officer (CEO). In the email, the CEO demands the immediate release of funds to the bank account that is listed. Which of the following principles best describes why this attack might be successful?
A. Authority
B. Scarcity
C. Consensus
D. Familiarity
-
Question 182:
A web application for a bank displays the following output when showing details about a customer's bank account:
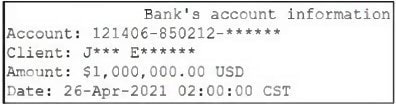
Which of the following techniques is most likely implemented in this web application?
A. Data minimization
B. Data scrambling
C. Data masking
D. Anonymization
-
Question 183:
The security operations center is researching an event concerning a suspicious IP address. A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced failed log-in attempts when authenticating from the same IP address:
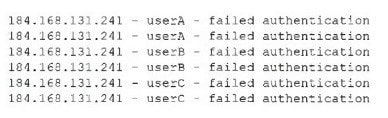
Which of the following most likely describes the attack that took place?
A. Spraying
B. Brute-force
C. Dictionary
D. Rainbow table
-
Question 184:
A security analyst finds a rogue device during a monthly audit of current endpoint assets that are connected to the network. The corporate network utilizes 802.1 X for access control. To be allowed on the network, a device must have a known hardware address, and a valid username and password must be entered in a captive portal. The following is the audit report:
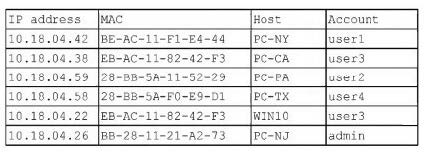
Which of the following is the most likely way a rogue device was allowed to connect?
A. A user performed a MAC cloning attack with a personal device.
B. A DHCP failure caused an incorrect IP address to be distributed.
C. An administrator bypassed the security controls for testing.
D. DNS hijacking let an attacker intercept the captive portal traffic.
-
Question 185:
Which of the following incident response activities ensures evidence is properly handied?
A. E-discovery
B. Chain of custody
C. Legal hold
D. Preservation
-
Question 186:
Visitors to a secured facility are required to check in with a photo ID and enter the facility through an access control vestibule. Which of the following but describes this form of security control?
A. Physical
B. Managerial
C. Technical
D. Operational
-
Question 187:
A company must ensure sensitive data at rest is rendered unreadable. Which of the following will the company most likely use?
A. Hashing
B. Tokenization
C. Encryption
D. Segmentation
-
Question 188:
Which of the following would help ensure a security analyst is able to accurately measure the overall risk to an organization when a new vulnerability is disclosed?
A. A full inventory of all hardware and software
B. Documentation of system classifications
C. A list of system owners and their departments
D. Third-party risk assessment documentation
-
Question 189:
A security analyst receives alerts about an internal system sending a large amount of unusual DNS queries to systems on the internet over short periods of time during non-business hours. Which of the following is most likely occurring?
A. A worm is propagating across the network.
B. Data is being exfiltrated.
C. A logic bomb is deleting data.
D. Ransomware is encrypting files.
-
Question 190:
A company is planning a disaster recovery site and needs to ensure that a single natural disaster would not result in the complete loss of regulated backup data. Which of the following should the company consider?
A. Geographic dispersion
B. Platform diversity
C. Hot site
D. Load balancing
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-701 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.