Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Mar 07, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
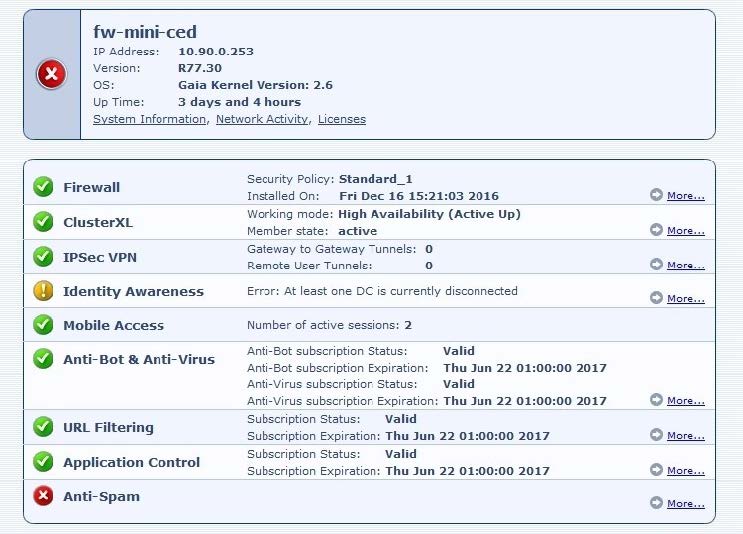
Question 11:
Consider the Global Properties following settings:
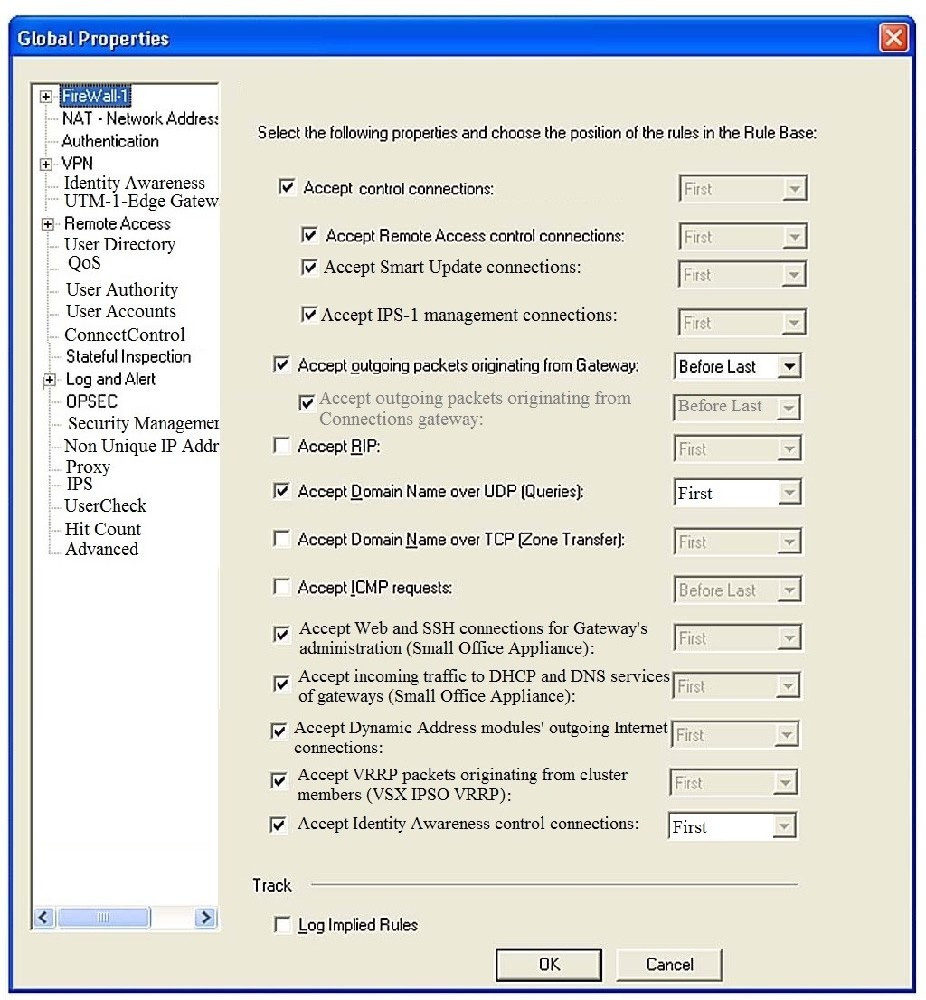
The selected option "Accept Domain Name over UDP (Queries)" means:
A. UDP Queries will be accepted by the traffic allowed only through interfaces with external anti-spoofing topology and this will be done before first explicit rule written by Administrator in a Security Policy.
B. All UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
C. No UDP Queries will be accepted by the traffic allowed through all interfaces and this will be done before first explicit rule written by Administrator in a Security Policy.
D. All UDP Queries will be accepted by the traffic allowed by first explicit rule written by Administrator in a Security Policy.
-
Question 12:
Choose what BEST describes the reason why querying logs now is very fast.
A. New Smart-1 appliances double the physical memory install
B. Indexing Engine indexes logs for faster search results
C. SmartConsole now queries results directly from the Security Gateway
D. The amount of logs been store is less than the usual in older versions
-
Question 13:
What does it mean if Deyra sees the gateway status:
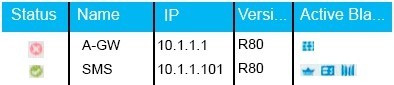
Choose the BEST answer.
A. SmartCenter Server cannot reach this Security Gateway
B. There is a blade reporting a problem
C. VPN software blade is reporting a malfunction
D. Security Gateway's MGNT NIC card is disconnected.
-
Question 14:
You noticed that CPU cores on the Security Gateway are usually 100% utilized and many packets were dropped. You don't have a budget to perform a hardware upgrade at this time. To optimize drops you decide to use Priority Queues and fully enable Dynamic Dispatcher. How can you enable them?
A. fw ctl multik dynamic_dispatching on
B. fw ctl multik dynamic_dispatching set_mode 9
C. fw ctl multik set_mode 9
D. fw ctl miltik pq enable
-
Question 15:
Identity Awareness lets an administrator easily configure network access and auditing based on three items Choose the correct statement.
A. Network location, the identity of a user and the active directory membership.
B. Network location, the identity of a user and the identity of a machine.
C. Network location, the telephone number of a user and the UID of a machine D. Geographical location, the identity of a user and the identity of a machine
-
Question 16:
When defining group-based access in an LDAP environment with Identity Awareness, what is the BEST object type to represent an LDAP group in a Security Policy?
A. Access Role
B. User Group
C. SmartDirectory Group
D. Group Template
-
Question 17:
Which message indicates IKE Phase 2 has completed successfully?
A. Quick Mode Complete
B. Aggressive Mode Complete
C. Main Mode Complete
D. IKE Mode Complete
-
Question 18:
Which statement is TRUE of anti-spoofing?
A. Anti-spoofing is not needed when IPS software blade is enabled
B. It is more secure to create anti-spoofing groups manually
C. It is BEST Practice to have anti-spoofing groups in sync with the routing table
D. With dynamic routing enabled, anti-spoofing groups are updated automatically whenever there is a routing change
-
Question 19:
What licensing feature is used to verify licenses and activate new licenses added to the License and Contracts repository?
A. Verification tool
B. Verification licensing
C. Automatic licensing
D. Automatic licensing and Verification tool
-
Question 20:
Identity Awareness allows easy configuration for network access and auditing based on what three items?
A. Client machine IP address.
B. Network location, the identity of a user and the identity of a machine.
C. Log server IP address.
D. Gateway proxy IP address.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.