Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Mar 07, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
Question 391:
What are the three components for Check Point Capsule?
A. Capsule Docs, Capsule Cloud, Capsule Connect
B. Capsule Workspace, Capsule Cloud, Capsule Connect
C. Capsule Workspace, Capsule Docs, Capsule Connect
D. Capsule Workspace, Capsule Docs, Capsule Cloud
-
Question 392:
R80.10 management server can manage gateways with which versions installed?
A. Versions R77 and higher
B. Versions R76 and higher
C. Versions R75.20 and higher
D. Version R75 and higher
-
Question 393:
In order to see real-time and historical graph views of Security Gateway statistics in SmartView Monitor, what feature needs to be enabled on the Security Gateway?
A. Logging and Monitoring
B. None - the data is available by default
C. Monitoring Blade
D. SNMP
-
Question 394:
Administrator Dave logs into R80 Management Server to review and makes some rule changes. He notices that there is a padlock sign next to the DNS rule in the Rule Base.
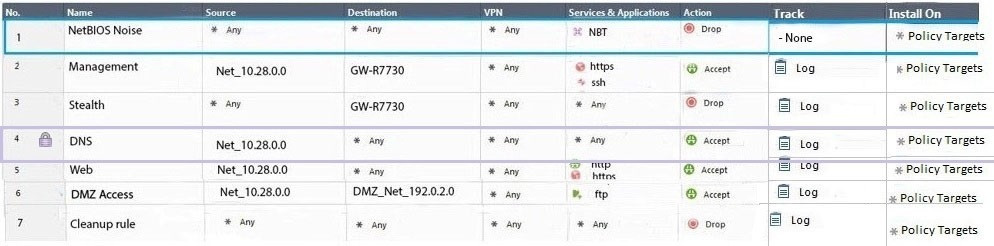
What is the possible explanation for this?
A. DNS Rule is using one of the new feature of R80 where an administrator can mark a rule with the padlock icon to let other administrators know it is important.
B. Another administrator is logged into the Management and currently editing the DNS Rule.
C. DNS Rule is a placeholder rule for a rule that existed in the past but was deleted.
D. This is normal behavior in R80 when there are duplicate rules in the Rule Base.
-
Question 395:
What is the purpose of the Stealth Rule?
A. To prevent users from directly connecting to a Security Gateway.
B. To reduce the number of rules in the database.
C. To reduce the amount of logs for performance issues.
D. To hide the gateway from the Internet.
-
Question 396:
What is the purpose of a Stealth Rule?
A. A rule used to hide a server's IP address from the outside world.
B. A rule that allows administrators to access SmartDashboard from any device.
C. To drop any traffic destined for the firewall that is not otherwise explicitly allowed.
D. A rule at the end of your policy to drop any traffic that is not explicitly allowed.
-
Question 397:
What are the steps to configure the HTTPS Inspection Policy?
A. Go to ManageandSettings > Blades > HTTPS Inspection > Configure in SmartDashboard
B. Go to Applicationandurl filtering blade > Advanced > Https Inspection > Policy
C. Go to ManageandSettings > Blades > HTTPS Inspection > Policy
D. Go to Applicationandurl filtering blade > Https Inspection > Policy
-
Question 398:
Which of the following describes how Threat Extraction functions?
A. Detect threats and provides a detailed report of discovered threats
B. Proactively detects threats
C. Delivers file with original content
D. Delivers PDF versions of original files with active content removed
-
Question 399:
What is the best sync method in the ClusterXL deployment?
A. Use 1 cluster + 1st sync
B. Use 1 dedicated sync interface
C. Use 3 clusters + 1st sync + 2nd sync + 3rd sync
D. Use 2 clusters + 1st sync + 2nd sync
-
Question 400:
Aggressive Mode in IKEv1 uses how many packages for negotiation?
A. 6
B. 3
C. depends on the make of the peer gateway
D. 5
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.