Exam Details
Exam Code
:156-215.81Exam Name
:Check Point Certified Security Administrator - R81 (CCSA)Certification
:Checkpoint CertificationsVendor
:CheckPointTotal Questions
:400 Q&AsLast Updated
:Mar 07, 2025
CheckPoint Checkpoint Certifications 156-215.81 Questions & Answers
-
Question 381:
Which option, when applied to a rule, allows traffic to VPN gateways in specific VPN communities?
A. All Connections (Clear or Encrypted)
B. Accept all encrypted traffic
C. Specific VPN Communities
D. All Site-to-Site VPN Communities
-
Question 382:
If there are two administrators logged in at the same time to the SmartConsole, and there are objects locked for editing, what must be done to make them available to other administrators? Choose the BEST answer
A. Save and install the Policy
B. Delete older versions of database
C. Revert the session.
D. Publish or discard the session
-
Question 383:
Where is the "Hit Count" feature enabled or disabled in SmartConsole?
A. On the Policy Package
B. On each Security Gateway
C. On the Policy layer
D. In Global Properties for the Security Management Server
-
Question 384:
The Gateway Status view in SmartConsole shows the overall status of Security Gateways and Software Blades. What does the Status Attention mean?
A. Cannot reach the Security Gateway.
B. The gateway and all its Software Blades are working properly.
C. At least one Software Blade has a minor issue, but the gateway works.
D. Cannot make SIC between the Security Management Server and the Security Gateway
-
Question 385:
Which of the following cannot be configured in an Access Role Object?
A. Networks
B. Users
C. Time
D. Machines
-
Question 386:
When a gateway requires user information for authentication, what order does it query servers for user information?
A. First - Internal user database, then LDAP servers in order of priority, finally the generic external user profile
B. First the Internal user database, then generic external user profile, finally LDAP servers in order of priority.
C. First the highest priority LDAP server, then the internal user database, then lower priority LDAP servers, finally the generic external profile
D. The external generic profile, then the internal user database finally the LDAP servers in order of priority.
-
Question 387:
What are two basic rules Check Point recommending for building an effective security policy?
A. Accept Rule and Drop Rule
B. Cleanup Rule and Stealth Rule
C. Explicit Rule and Implied Rule
D. NAT Rule and Reject Rule
-
Question 388:
Name the pre-defined Roles included in Gaia OS.
A. AdminRole, and MonitorRole
B. ReadWriteRole, and ReadyOnly Role
C. AdminRole, cloningAdminRole, and Monitor Role
D. AdminRole
-
Question 389:
Vanessa is attempting to log into the Gaia Web Portal. She is able to login successfully. Then she tries the same username and password for SmartConsole but gets the message in the screenshot image below. She has checked that the IP address of the Server is correct and the username and password she used to login into Gaia is also correct.
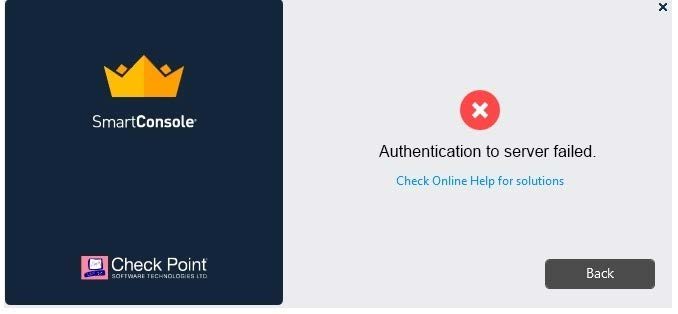
What is the most likely reason?
A. Check Point R80 SmartConsole authentication is more secure than in previous versions and Vanessa requires a special authentication key for R80 SmartConsole. Check that the correct key details are used.
B. Check Point Management software authentication details are not automatically the same as the Operating System authentication details. Check that she is using the correct details.
C. SmartConsole Authentication is not allowed for Vanessa until a Super administrator has logged in first and cleared any other administrator sessions.
D. Authentication failed because Vanessa's username is not allowed in the new Threat Prevention console update checks even though these checks passed with Gaia.
-
Question 390:
You have enabled "Extended Log" as a tracking option to a security rule. However, you are still not seeing any data type information. What is the MOST likely reason?
A. Identity Awareness is not enabled.
B. Log Trimming is enabled.
C. Logging has disk space issues
D. Content Awareness is not enabled.
Related Exams:
156-110
Check Point Certified Security Principles Associate (CCSPA)156-115.80
Check Point Certified Security Master - R80156-215.71
Check Point Certified Security Administrator R71156-215.80
Check Point Certified Security Administrator (CCSA)156-215.81
Check Point Certified Security Administrator - R81 (CCSA)156-215.81.20
Check Point Certified Security Administrator - R81.20 (CCSA)156-315.80
Check Point Certified Security Expert - R80 (CCSE)156-315.81
Check Point Certified Security Expert - R81 (CCSE)156-315.81.20
Check Point Certified Security Expert - R81.20156-560
Check Point Certified Cloud Specialist
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CheckPoint exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 156-215.81 exam preparations and CheckPoint certification application, do not hesitate to visit our Vcedump.com to find your solutions here.