Exam Details
Exam Code
:312-49Exam Name
:ECCouncil Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:
EC-COUNCIL EC-COUNCIL Certifications 312-49 Questions & Answers
-
Question 271:
What type of flash memory card comes in either Type I or Type II and consumes only five percent of the power required by small hard drives?
A. SD memory
B. CF memory
C. MMC memory
D. SM memory
-
Question 272:
When searching through file headers for picture file formats, what should be searched to find a JPEG file in hexadecimal format?
A. FF D8 FF E0 00 10
B. FF FF FF FF FF FF
C. FF 00 FF 00 FF 00
D. EF 00 EF 00 EF 00
-
Question 273:
Jack Smith is a forensics investigator who works for Mason Computer Investigation Services. He is investigating a computer that was infected by Ramen Virus.
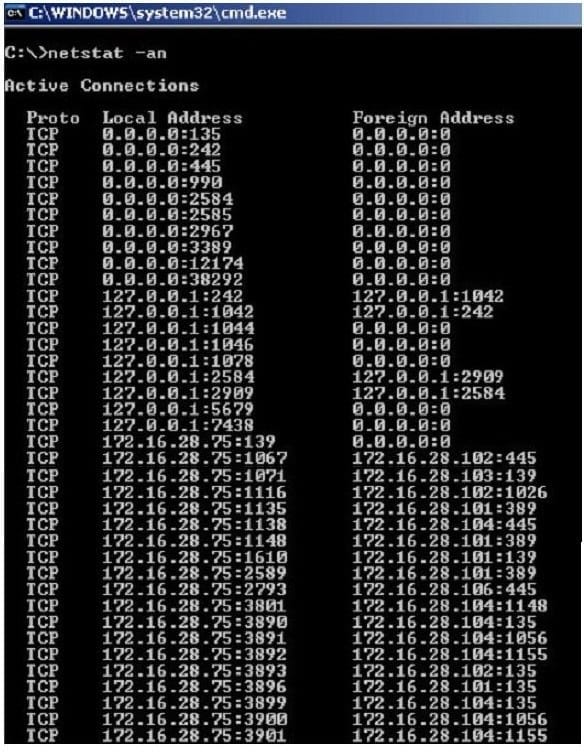
He runs the netstat command on the machine to see its current connections. In the following screenshot, what do the 0.0.0.0 IP addresses signify?
A. Those connections are established
B. Those connections are in listening mode
C. Those connections are in closed/waiting mode
D. Those connections are in timed out/waiting mode
-
Question 274:
Davidson Trucking is a small transportation company that has three local offices in Detroit Michigan. Ten female employees that work for the company have gone to an attorney reporting that male employees repeatedly harassed them and that management did nothing to stop the problem. Davidson has employee policies that outline all company guidelines, including awareness on harassment and how it will not be tolerated. When the case is brought to court, whom should the prosecuting attorney call upon for not upholding company policy?
A. IT personnel
B. Employees themselves
C. Supervisors
D. Administrative assistant in charge of writing policies
-
Question 275:
When should an MD5 hash check be performed when processing evidence?
A. After the evidence examination has been completed
B. On an hourly basis during the evidence examination
C. Before and after evidence examination
D. Before the evidence examination has been completed
-
Question 276:
At what layer does a cross site scripting attack occur on?
A. Presentation
B. Application
C. Session
D. Data Link
-
Question 277:
John is working on his company policies and guidelines. The section he is currently working on covers company documents; how they should be handled, stored, and eventually destroyed. John is concerned about the process whereby outdated documents are destroyed. What type of shredder should John write in the guidelines to be used when destroying documents?
A. Strip-cut shredder
B. Cross-cut shredder
C. Cross-hatch shredder
D. Cris-cross shredder
-
Question 278:
To check for POP3 traffic using Ethereal, what port should an investigator search by?
A. 143
B. 25
C. 110
D. 125
-
Question 279:
How often must a company keep log files for them to be admissible in a court of law?
A. All log files are admissible in court no matter their frequency
B. Weekly
C. Monthly
D. Continuously
-
Question 280:
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
A. NTOSKRNL.EXE
B. NTLDR
C. LSASS.EXE
D. NTDETECT.COM
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.