Exam Details
Exam Code
:312-49Exam Name
:ECCouncil Computer Hacking Forensic Investigator (V9)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:531 Q&AsLast Updated
:Apr 11, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49 Questions & Answers
-
Question 281:
Jacob is a computer forensics investigator with over 10 years experience in investigations and has written over 50 articles on computer forensics. He has been called upon as a qualified witness to testify the accuracy and integrity of the technical log files gathered in an investigation into computer fraud. What is the term used for Jacob testimony in this case?
A. Justification
B. Authentication
C. Reiteration
D. Certification
-
Question 282:
What method of copying should always be performed first before carrying out an investigation?
A. Parity-bit copy
B. Bit-stream copy
C. MS-DOS disc copy
D. System level copy
-
Question 283:
Where is the default location for Apache access logs on a Linux computer?
A. usr/local/apache/logs/access_log
B. bin/local/home/apache/logs/access_log
C. usr/logs/access_log
D. logs/usr/apache/access_log
-
Question 284:
What technique is used by JPEGs for compression?
A. ZIP
B. TCD
C. DCT
D. TIFF-8
-
Question 285:
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
A. It contains the times and dates of when the system was last patched
B. It is not necessary to scan the virtual memory of a computer
C. It contains the times and dates of all the system files
D. Hidden running processes
-
Question 286:
Paraben Lockdown device uses which operating system to write hard drive data?
A. Mac OS
B. Red Hat
C. Unix
D. Windows
-
Question 287:
Paul is a computer forensics investigator working for Tyler and Company Consultants. Paul has been called upon to help investigate a computer hacking ring broken up by the local police. Paul begins to inventory the PCs found in the hackers hideout. Paul then comes across a PDA left by them that is attached to a number of different peripheral devices. What is the first step that Paul must take with the PDA to ensure the integrity of the investigation?
A. Place PDA, including all devices, in an antistatic bag
B. Unplug all connected devices
C. Power off all devices if currently on
D. Photograph and document the peripheral devices
-
Question 288:
During an investigation, an employee was found to have deleted harassing emails that were sent to someone else. The company was using Microsoft Exchange and had message tracking enabled. Where could the investigator search to find the message tracking log file on the Exchange server?
A. C:\Program Files\Exchsrvr\servername.log
B. D:\Exchsrvr\Message Tracking\servername.log
C. C:\Exchsrvr\Message Tracking\servername.log
D. C:\Program Files\Microsoft Exchange\srvr\servername.log
-
Question 289:
What must be obtained before an investigation is carried out at a location?
A. Search warrant
B. Subpoena
C. Habeas corpus
D. Modus operandi
-
Question 290:
What is the CIDR from the following screenshot?
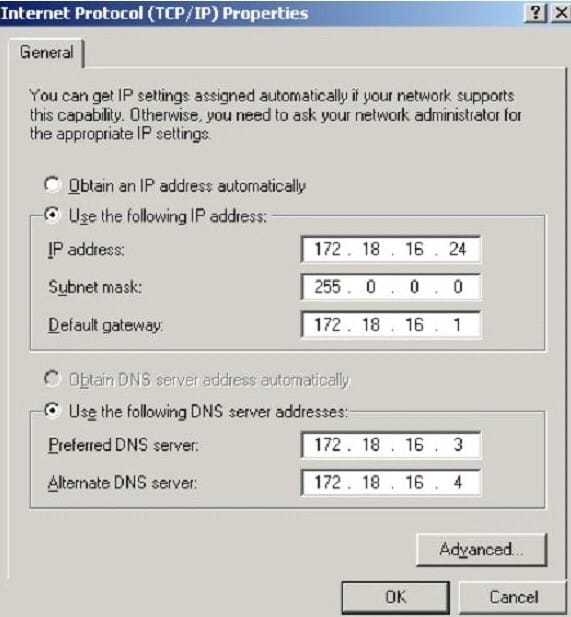
A. /24A./24A./24
B. /32 B./32 B./32
C. /16 C./16 C./16
D. /8D./8D./8
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.