Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 721:
The IIS log file format is a fixed (cannot be customized) ASCII text-based format. The IIS format includes basic items, such as client IP address, user name, date and time, service and instance, server name and IP address, request type, target of operation, etc. Identify the service status code from the following IIS log.
192.168.100.150, -, 03/6/11, 8:45:30, W3SVC2, SERVER, 172.15.10.30, 4210, 125, 3524, 100, 0, GET, / dollerlogo.gif,
A. W3SVC2
B. 4210
C. 3524
D. 100
-
Question 722:
Task list command displays a list of applications and services with their Process ID (PID) for all tasks running on either a local or a remote computer.
Which of the following task list commands provides information about the listed processes, including the image name, PID, name, and number of the session for the process?
A. tasklist/s
B. tasklist/u
C. tasklist/p
D. tasklist/V
-
Question 723:
A mobile operating system manages communication between the mobile device and other compatible devices like computers, televisions, or printers.
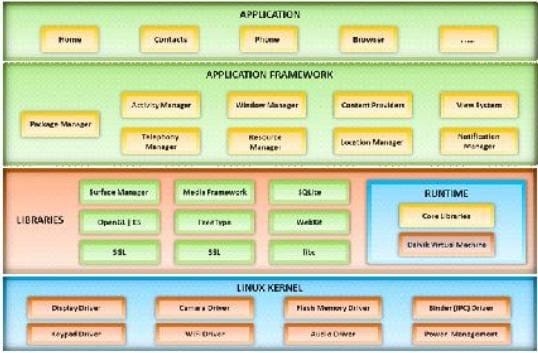
Which mobile operating system architecture is represented here?
A. webOS System Architecture
B. Symbian OS Architecture
C. Android OS Architecture
D. Windows Phone 7 Architecture
-
Question 724:
Which of the following Wi-Fi chalking methods refers to drawing symbols in public places to advertise open Wi-Fi networks?
A. WarWalking
B. WarFlying
C. WarChalking
D. WarDhving
-
Question 725:
In what circumstances would you conduct searches without a warrant?
A. When destruction of evidence is imminent, a warrantless seizure of that evidence is justified if there is probable cause to believe that the item seized constitutes evidence of criminal activity
B. Agents may search a place or object without a warrant if he suspect the crime was committed
C. A search warrant is not required if the crime involves Denial-Of-Service attack over the Internet
D. Law enforcement agencies located in California under section SB 567 are authorized to seize computers without warrant under all circumstances
-
Question 726:
WPA2 provides enterprise and Wi-Fi users with stronger data protection and network access control which of the following encryption algorithm is used DVWPA2?
A. RC4-CCMP
B. RC4-TKIP
C. AES-CCMP
D. AES-TKIP
-
Question 727:
MAC filtering is a security access control methodology, where a ___________ is assigned to each network card to determine access to the network
A. 16-bit address
B. 24-bit address
C. 32-bit address
D. 48-bit address
-
Question 728:
Network forensics can be defined as the sniffing, recording, acquisition and analysis of the network traffic and event logs in order to investigate a network security incident.
A. True
B. False
-
Question 729:
SIM is a removable component that contains essential information about the subscriber. It has both volatile and non-volatile memory. The file system of a SIM resides in _____________ memory.
A. Volatile
B. Non-volatile
-
Question 730:
JPEG is a commonly used method of compressing photographic Images. It uses a compression algorithm to minimize the size of the natural image, without affecting the quality of the image. The JPEG lossy algorithm divides the image in separate blocks of____________.
A. 4x4 pixels
B. 8x8 pixels
C. 16x16 pixels
D. 32x32 pixels
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.