Exam Details
Exam Code
:312-49V10Exam Name
:EC-Council Certified Computer Hacking Forensic Investigator (V10)Certification
:EC-COUNCIL CertificationsVendor
:EC-COUNCILTotal Questions
:1006 Q&AsLast Updated
:Apr 12, 2025
EC-COUNCIL EC-COUNCIL Certifications 312-49V10 Questions & Answers
-
Question 731:
You should always work with original evidence
A. True
B. False
-
Question 732:
When the operating system marks cluster as used, but does not allocate them to any file, such clusters are known as ___________.
A. Lost clusters
B. Bad clusters
C. Empty clusters
D. Unused clusters
-
Question 733:
You can interact with the Registry through intermediate programs. Graphical user interface (GUI) Registry editors such as Regedit.exe or Regedt32 exe are commonly used as intermediate programs in Windows 7. Which of the following is a root folder of the registry editor?
A. HKEY_USERS
B. HKEY_LOCAL_ADMIN
C. HKEY_CLASSES_ADMIN
D. HKEY_CLASSES_SYSTEM
-
Question 734:
Which is not a part of environmental conditions of a forensics lab?
A. Large dimensions of the room
B. Good cooling system to overcome excess heat generated by the work station
C. Allocation of workstations as per the room dimensions
D. Open windows facing the public road
-
Question 735:
Digital photography helps in correcting the perspective of the Image which Is used In taking the measurements of the evidence. Snapshots of the evidence and incident-prone areas need to be taken to help in the forensic process. Is digital photography accepted as evidence in the court of law?
A. Yes
B. No
-
Question 736:
Which of the following statements is incorrect related to acquiring electronic evidence at crime scene?
A. Sample banners are used to record the system activities when used by the unauthorized user
B. In warning banners, organizations give clear and unequivocal notice to intruders that by signing onto the system they are expressly consenting to such monitoring
C. The equipment is seized which is connected to the case, knowing the role of the computer which will indicate what should be taken
D. At the time of seizing process, you need to shut down the computer immediately
-
Question 737:
What document does the screenshot represent?
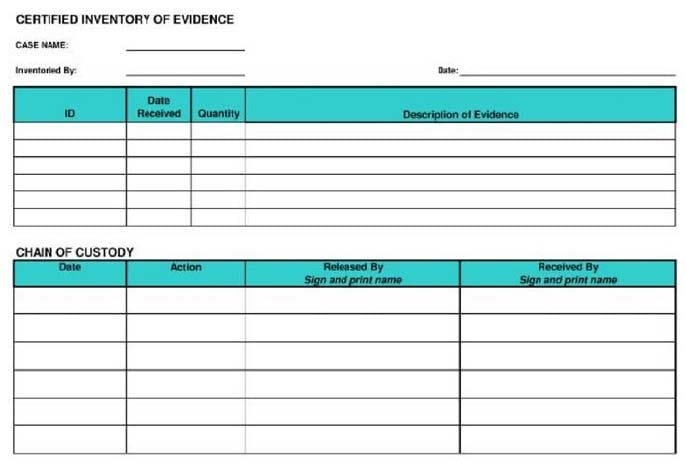
A. Chain of custody form
B. Search warrant form
C. Evidence collection form
D. Expert witness form
-
Question 738:
Volatile information can be easily modified or lost when the system is shut down or rebooted. It helps to determine a logical timeline of the security incident and the users who would be responsible.
A. True
B. False
-
Question 739:
Hard disk data addressing is a method of allotting addresses to each ___________of data on a hard disk
A. Physical block
B. Logical block
C. Operating system block
D. Hard disk block
-
Question 740:
The disk in the disk drive rotates at high speed, and heads in the disk drive are used only to read data.
A. True
B. False
Related Exams:
112-51
EC-Council Certified Network Defense Essentials (NDE)212-77
EC-Council Certified Linux Security212-81
EC-Council Certified Encryption Specialist (ECES)212-82
EC-Council Certified Cybersecurity Technician (C|CT)212-89
EC-Council Certified Incident Handler (ECIH)312-38
EC-Council Certified Network Defender (CND)312-39
EC-Council Certified SOC Analyst (CSA)312-40
EC-Council Certified Cloud Security Engineer (CCSE)312-49
ECCouncil Computer Hacking Forensic Investigator (V9)312-49V10
EC-Council Certified Computer Hacking Forensic Investigator (V10)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only EC-COUNCIL exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 312-49V10 exam preparations and EC-COUNCIL certification application, do not hesitate to visit our Vcedump.com to find your solutions here.