Exam Details
Exam Code
:350-901Exam Name
:Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)Certification
:Cisco Certified DevNet ProfessionalVendor
:CiscoTotal Questions
:414 Q&AsLast Updated
:Apr 14, 2025
Cisco Cisco Certified DevNet Professional 350-901 Questions & Answers
-
Question 271:
What are two advantages of using model-driven telemetry, such as gRPC. instead of traditional telemetry gathering methods? (Choose two.)
A. all data is ad-hoc
B. efficient use of bandwidth
C. no overhead
D. decentralized storage of telemetry
E. continuous information with incremental updates
-
Question 272:
What is the function of dependency management?
A. separating code into modules that execute independently
B. utilizing a single programming language/framework for each code project
C. automating the identification and resolution of code dependencies
D. managing and enforcing unique software version names or numbers
-
Question 273:
Refer to the exhibit.
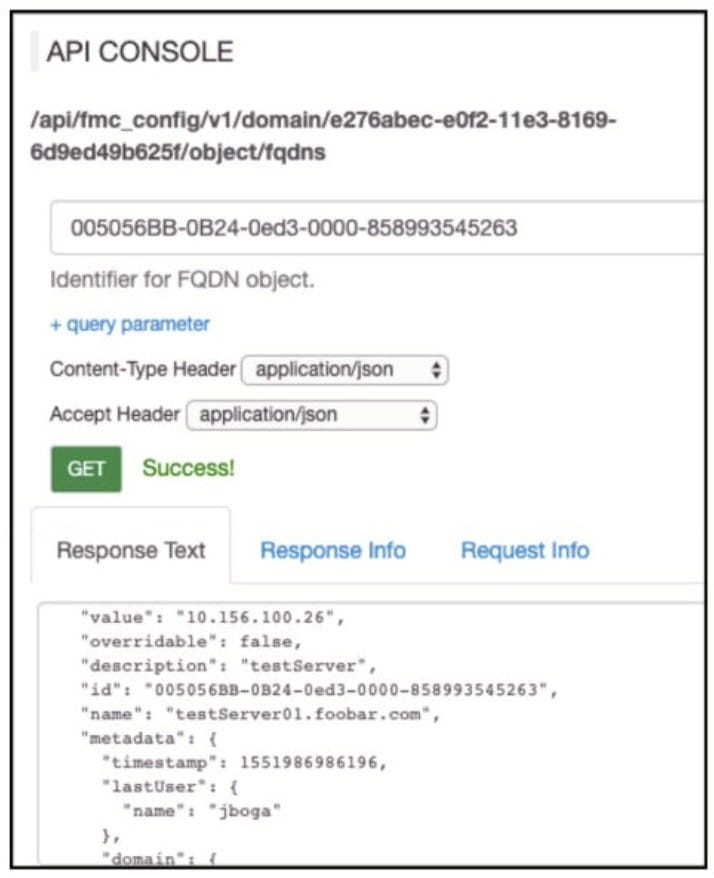
Which AP! call does an engineer use to delete the FQDN object?
A. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f
B. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169- 6d9ed49b625f/object/fqdns/005056BB-0B24-0ed3-0000-858993545263
C. DELETE /api/fmc_config/v1/domain?id=e276abec-e0f2-11e3-8169-6d9ed49b625f
D. DELETE /api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169- 6d9ed49b625f/object/fqdns?id=005056BB-0B24-0ed3-0000-858993545263
-
Question 274:
An engineer is developing a Docket container for an application in Python For security reasons the application needs to be accessible on port 5001 only. Which line should be added to the dockerfile m order to accomplish this?
A. ENTRYPOINT 5001
B. PORT SRC 5001
C. ADO PORT 5001
D. EXPOSE 5001
-
Question 275:
While working with the Webex Teams API, on an application that uses end-to-end encryption, a webhook has been received. What must be considered to read the message?
A. Webhook information cannot be used to read the message because of end-to-end encryption. The API key is needed to decrypt the message.
B. Webhook returns the full unencrypted message. Only the body is needed to query the API.
C. Webhook returns a hashed version of the message that must be unhashed with the API key.
D. Webhook returns message identification. To query, the API is needed for that message to get the decrypted information.
-
Question 276:
Why is end-to-end encryption deployed when exposing sensitive data through APIs?
A. Traffic is encrypted and decrypted at every hop in the network path.
B. Data transfers are untraceable from source to destination.
C. Data cannot be read or modified other than by the true source and destination.
D. Server-side encryption enables the destination to control data protection.
-
Question 277:
Refer to the exhibit.

A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the file, and which cluster FS accessed using username/password authentication rather than using a certificate?
A. three dusters; scratch
B. three clusters: development
C. two dusters; development
D. two clusters: scratch
-
Question 278:
A developer has created an application based on customer requirements. The customer needs to run the application with the minimum downtime. Which design approach regarding high-availability applications, Recovery Time Objective, and Recovery Point Objective must be taken?
A. Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
B. Active/passive results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
C. Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers does not need to be timely to allow seamless request flow.
D. Active/active results in lower RTO and RPO. For RPO, data synchronization between the two data centers must be timely to allow seamless request flow.
-
Question 279:
A local data center deployment using Cisco NX-OS switches is scaling and requires automatic configuration at scale Configuration management must be set up for a Cisco NX- OS switch by using Ansible. The Ansible control server is currently located on a different subnet than the switch The solution has these requirements:
The transport protocol used must be encrypted The connections must originate from a server m the same local network Enable mode must be supported
Which connectivity method must be used?
A. SSH through a bastion host and ansible_become method for privilege escalation.
B. HTTPS through a repository and ansible_become method for privilege escalation
C. XML-RPC through a web proxy.
D. HTTP through a web proxy.
-
Question 280:
Which OAuth mechanism enables clients to continue to have an active access token without further interaction from the user?
A. JWT
B. password grant
C. refresh grant
D. preshared key
Related Exams:
300-435
Automating and Programming Cisco Enterprise Solutions (ENAUTO)300-535
Automating and Programming Cisco Service Provider Solutions (SPAUTO)300-635
Automating and Programming Cisco Data Center Solutions (DCAUTO)300-735
Automating and Programming Cisco Security Solutions (SAUTO)300-835
Automating Cisco Collaboration Solutions (CLAUTO)300-910
Implementing DevOps Solutions and Practices using Cisco Platforms (DEVOPS)350-901
Developing Applications Using Cisco Core Platforms and APIs (DEVCOR)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 350-901 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.