Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 221:
The IT department at a growing law firm wants to begin using a third-party vendor for vulnerability monitoring and mitigation. The executive director of the law firm wishes to outline the assumptions and expectations between the two companies. Which of the following documents might be referenced in the event of a security breach at the law firm?
A.SLA
B. MOU
C. SOW
D. NDA
-
Question 222:
During a red team engagement, a penetration tester found a production server. Which of the following portions of the SOW should be referenced to see if the server should be part of the testing engagement?
A. Authorization
B. Exploitation
C. Communication
D. Scope
-
Question 223:
An analyst is conducting a log review and identifies the following snippet in one of the logs:
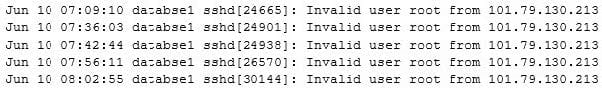
Which of the following MOST likely caused this activity?
A. SQL injection
B. Privilege escalation
C. Forgotten password
D. Brute force
-
Question 224:
A company requests a security assessment of its network. Permission is given, but no details are provided. It is discovered that the company has a web presence, and the company's IP address is 70.182.11.4. Which of the following Nmap commands would reveal common open ports and their versions?
A. nmap - oV
B. nmap -vO
C. nmap -sv
-
Question 225:
An alert is issued from the SIEM that indicates a large number of failed logins for the same account name on one of the application servers starting at 10:20 a.m. No other significant failed login activity is detected. Using Splunk to search for activity pertaining to that account name, a security analyst finds the account has been authenticating successfully for some time and started to fail this morning. The account is attempting to authenticate from an internal server that is running a database to an application server. No other security activity is detected on the network. The analyst discovers the account owner is a developer who no longer works for the company. Which of the following is the MOST likely reason for the failed login attempts for that account?
A. The account that is failing to authenticate has not been maintained, and the company password change policy time frame has been reached for that account
B. The host-based firewall is blocking port 389 LDAP communication, preventing the login credentials from being received by the application server
C. The license for the application has expired, and the failed logins will continue to occur until a new license key is installed on the application
D. A successful malware attack has provided someone access to the network, and failed login attempts are an indication of an attempt to privilege access to the application
-
Question 226:
Which of the following is a vulnerability that is specific to hypervisors?
A. DDoS
B. VLAN hopping
C. Weak encryption
D. WMescape
-
Question 227:
An organization is performing vendor selection activities for penetration testing, and a security analyst is reviewing the MOA and rules of engagement, which were supplied with proposals. Which of the following should the analyst expect will be included in the documents and why?
A. The scope of the penetration test should be included in the MOA to ensure penetration testing is conducted against only specifically authorized network resources.
B. The MOA should address the client SLA in relation to reporting results to regulatory authorities, including issuing banks for organizations that process cardholder data.
C. The rules of engagement should include detailed results of the penetration scan, including all findings, as well as designation of whether vulnerabilities identified during the scanning phases are found to be exploitable during the penetration test.
D. The exploitation standards should be addressed in the rules of engagement to ensure both parties are aware of the depth of exploitation that will be attempted by penetration testers.
-
Question 228:
A manufacturing company has decided to participate in direct sales of its products to consumers. The company decides to use a subdomain of its main site with its existing cloud service provider as the portal for e-commerce. After launch, the site is stable and functions properly, but after a robust day of sales, the site begins to redirect to a competitor's landing page. Which of the following actions should the company's security team take to determine the cause of the issue and minimize the scope of impact?
A. Engage a third party to provide penetration testing services to see if an exploit can be found
B. Check DNS records to ensure Cname or alias records are in place for the subdomain
C. Query the cloud provider to determine the nature of the DNS attack and find out which other clients are affected
D. Check the DNS records to ensure a correct MX record is established for the subdomain
-
Question 229:
An employee was conducting research on the Internet when a message from cyber criminals appeared on the screen, stating the hard drive was just encrypted by a ransomware variant. An analyst observes the following:
1.
Antivirus signatures were updated recently
2.
The desktop background was changed
3.
Web proxy logs show browsing to various information security sites and ad network traffic
4.
There is a high volume of hard disk activity on the file server
5.
SMTP server shown the employee recently received several emails from blocked senders
6.
The company recently switched web hosting providers
7.
There are several IPS alerts for external port scans
Which of the following describes how the employee got this type of ransomware?
A. The employee fell victim to a CSRF attack
B. The employee was using another user's credentials
C. The employee opened an email attachment
D. The employee updated antivirus signatures
-
Question 230:
The Chief Information Security Officer (CISO) has asked the security analyst to examine abnormally high processor utilization on a key server. The output below is from the company's research and development (RandD) server.
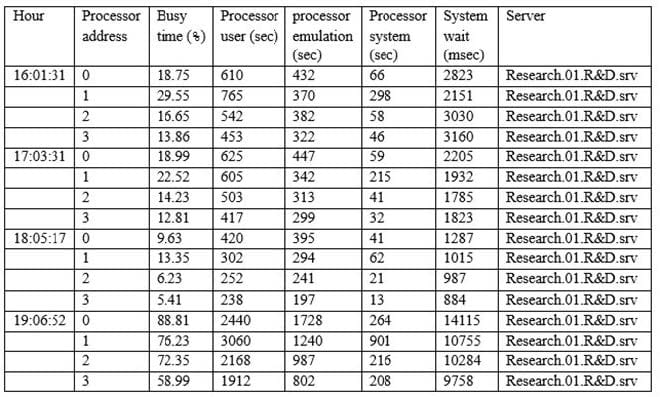
Which of the following actions should the security analyst take FIRST?
A. Initiate an investigation
B. Isolate the RandD server
C. Reimage the server
D. Determine availability
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.