Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 09, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 331:
The board of directors made the decision to adopt a cloud-first strategy. The current security infrastructure was designed for on-premises implementation. A critical application that is subject to the Federal Information Security Management Act (FISMA) of 2002 compliance has been identified as a candidate for a hybrid cloud deployment model. Which of the following should be conducted FIRST?
A. Develop a request for proposal.
B. Perform a risk assessment.
C. Review current security controls.
D. Review the SLA for FISMA compliance.
-
Question 332:
Given a packet capture of the following scan:
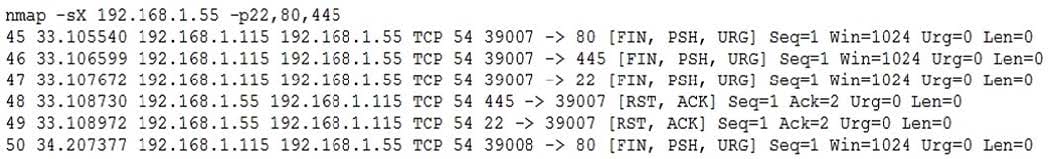
Which of the following should MOST likely be inferred on the scan's output?
A. 192.168.1.115 is hosting a web server.
B. 192.168.1.55 is hosting a web server.
C. 192.168.1.55 is a Linux server.
D. 192.168.1.55 is a file server.
-
Question 333:
A cyber incident response team finds a vulnerability on a company website that allowed an attacker to inject malicious code into its web application. There have been numerous unsuspecting users visiting the infected page, and the malicious code executed on the victim's browser has led to stolen cookies, hijacked sessions, malware execution, and bypassed access control. Which of the following exploits is the attacker conducting on the company's website?
A. Logic bomb
B. Rootkit
C. Privilege escalation
D. Cross-site scripting
-
Question 334:
After implementing and running an automated patching tool, a security administrator ran a vulnerability scan that reported no missing patches found. Which of the following BEST describes why this tool was used?
A. To create a chain of evidence to demonstrate when the servers were patched.
B. To harden the servers against new attacks.
C. To provide validation that the remediation was active.
D. To generate log data for unreleased patches.
-
Question 335:
A company has established an ongoing vulnerability management program and procured the latest technology to support it. However, the program is failing because several vulnerabilities have not been detected. Which of the following will reduce the number of false negatives?
A. Increase scan frequency.
B. Perform credentialed scans.
C. Update the security incident response plan.
D. Reconfigure scanner to brute force mechanisms.
-
Question 336:
Which of the following is the MOST secure method to perform dynamic analysis of malware that can sense when it is in a virtual environment?
A. Place the malware on an isolated virtual server disconnected from the network.
B. Place the malware in a virtual server that is running Windows and is connected to the network.
C. Place the malware on a virtual server connected to a VLAN.
D. Place the malware on a virtual server running SIFT and begin analysis.
-
Question 337:
A security operations team was alerted to abnormal DNS activity coming from a user's machine. The team performed a forensic investigation and discovered a host had been compromised. Malicious code was using DNS as a tunnel to extract data from the client machine, which had been leaked and transferred to an unsecure public Internet site. Which of the following BEST describes the attack?
A. Phishing
B. Pharming
C. Cache poisoning
D. Data exfiltration
-
Question 338:
Creating an isolated environment in order to test and observe the behavior of unknown software is also known as:
A. sniffing
B. hardening
C. hashing D. sandboxing
-
Question 339:
Company A's security policy states that only PKI authentication should be used for all SSH accounts. A security analyst from Company A is reviewing the following auth.log and configuration settings:

Which of the following changes should be made to the following sshd_config file to establish compliance with the policy?
A. Change PermitRootLogin no to #PermitRootLogin yes
B. Change ChallengeResponseAuthentication yes to ChallangeResponseAuthentication no
C. Change PubkeyAuthentication yes to #PubkeyAuthentication yes
D. Change #AuthorizedKeysFile sh/.ssh/authorized_keys to AuthorizedKeysFile sh/.ssh/authorized_keys
E. Change PassworAuthentication yes to PasswordAuthentication no
-
Question 340:
A security analyst is reviewing packet captures to determine the extent of success during an attacker's reconnaissance phase following a recent incident.
The following is a hex and ASCII dump of one such packet:

Which of the following BEST describes this packet?
A. DNS BIND version request
B. DNS over UDP standard query
C. DNS over TCP server status query
D. DNS zone transfer request
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.