Exam Details
Exam Code
:CS0-002Exam Name
:CompTIA Cybersecurity Analyst (CySA+)Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1059 Q&AsLast Updated
:Apr 17, 2025
CompTIA CompTIA Certifications CS0-002 Questions & Answers
-
Question 351:
Given the following log snippet:

Which of the following describes the events that have occurred?
A. An attempt to make an SSH connection from "superman" was done using a password.
B. An attempt to make an SSH connection from 192.168.1.166 was done using PKI.
C. An attempt to make an SSH connection from outside the network was done using PKI.
D. An attempt to make an SSH connection from an unknown IP address was done using a password.
-
Question 352:
A cybersecurity analyst is hired to review the security measures implemented within the domain controllers of a company. Upon review, the cybersecurity analyst notices a brute force attack can be launched against domain controllers that run on a Windows platform. The first remediation step implemented by the cybersecurity analyst is to make the account passwords more complex. Which of the following is the NEXT remediation step the cybersecurity analyst needs to implement?
A. Disable the ability to store a LAN manager hash.
B. Deploy a vulnerability scanner tool.
C. Install a different antivirus software.
D. Perform more frequent port scanning.
E. Move administrator accounts to a new security group.
-
Question 353:
A vulnerability analyst needs to identify all systems with unauthorized web servers on the 10.1.1.0/24 network. The analyst uses the following default Nmap scan:
nmap -sV -p 1-65535 10.1.1.0/24
Which of the following would be the result of running the above command?
A. This scan checks all TCP ports.
B. This scan probes all ports and returns open ones.
C. This scan checks all TCP ports and returns versions.
D. This scan identifies unauthorized servers.
-
Question 354:
A security analyst discovers a network intrusion and quickly solves the problem by closing an unused port. Which of the following should be completed?
A. Vulnerability report
B. Memorandum of agreement
C. Reverse-engineering incident report
D. Lessons learned report
-
Question 355:
A computer at a company was used to commit a crime. The system was seized and removed for further analysis. Which of the following is the purpose of labeling cables and connections when seizing the computer system?
A. To capture the system configuration as it was at the time it was removed
B. To maintain the chain of custody
C. To block any communication with the computer system from attack
D. To document the model, manufacturer, and type of cables connected
-
Question 356:
An analyst reviews a recent report of vulnerabilities on a company's financial application server. Which of the following should the analyst rate as being of the HIGHEST importance to the company's environment?
A. Banner grabbing
B. Remote code execution
C. SQL injection
D. Use of old encryption algorithms
E. Susceptibility to XSS
-
Question 357:
A security analyst is reviewing packet captures for a specific server that is suspected of containing malware and discovers the following packets:
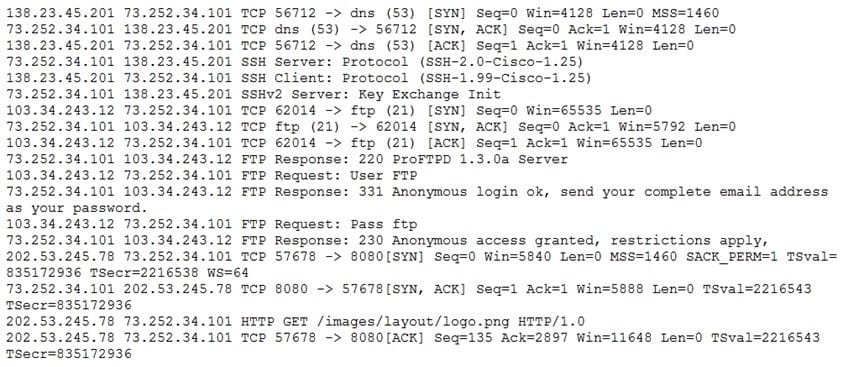
Which of the following traffic patterns or data would be MOST concerning to the security analyst?
A. Port used for SMTP traffic from 73.252.34.101
B. Unencrypted password sent from 103.34.243.12
C. Anonymous access granted by 103.34.243.12
D. Ports used for HTTP traffic from 202.53.245.78
-
Question 358:
A technician receives an alert indicating an endpoint is beaconing to a suspect dynamic DNS domain. Which of the following countermeasures should be used to BEST protect the network in response to this alert? (Choose two.)
A. Set up a sinkhole for that dynamic DNS domain to prevent communication.
B. Isolate the infected endpoint to prevent the potential spread of malicious activity.
C. Implement an internal honeypot to catch the malicious traffic and trace it.
D. Perform a risk assessment and implement compensating controls.
E. Ensure the IDS is active on the network segment where the endpoint resides.
-
Question 359:
Which of the following utilities could be used to resolve an IP address to a domain name, assuming the address has a PTR record?
A. ifconfig
B. ping
C. arp
D. nbtstat
-
Question 360:
A security analyst has just completed a vulnerability scan of servers that support a business critical application that is managed by an outside vendor. The results of the scan indicate the devices are missing critical patches. Which of the following factors can inhibit remediation of these vulnerabilities? (Choose two.)
A. Inappropriate data classifications
B. SLAs with the supporting vendor
C. Business process interruption
D. Required sandbox testing
E. Incomplete asset inventory
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+CS0-002
CompTIA Cybersecurity Analyst (CySA+)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your CS0-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.